MS Word’s Malicious Macro Facilitates Downloading of Vawtrak Trojan – This time attackers rely upon VBS file containing Execution Policy Bypass Flag.
Hackers have managed to implement yet another cybercrime campaign by installing Vawtrak banking Trojan into users’ computers.
According to security researchers at Trend Micro, this latest attack relies upon a multi-stage hacking routine that entails use of Microsoft Word documents. These documents are infected with malicious macros.
The current campaign targets high-profile banks including Bank of America, HSBC, Barclays, J.P. Morgan and Lloyd’s Bank.
Evasive tactics used by Cybercriminals:
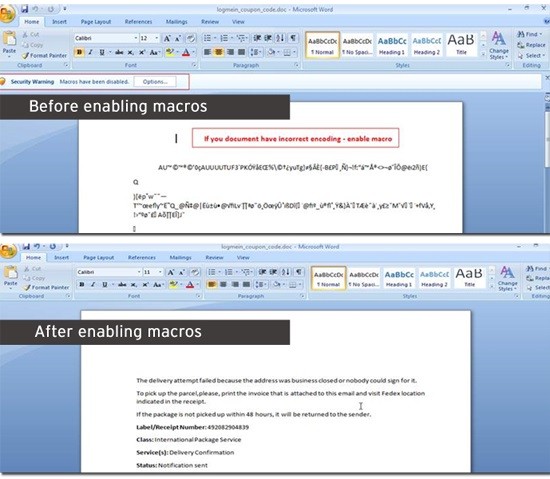
Multiple tactics are used by the perpetrators of such malicious campaigns for masking their attack mechanism. One such tactic is of equipping the document with scrambled content.
This mechanism gets identified when the macro feature in MS Word software component is enabled.
Another commonly preferred mechanism of hackers involves delivering a VBS file containing a “-ExecutionPolicy bypass” policy flag.
Usually system administrators use this system as a security mechanism for preventing users from activating scripts that don’t comply with the requirements of their policy.
“Bypass” command if used in scripts makes it easier to execute unrestricted files without giving warnings.
According to Security Researchers at Trend Micro, this three-step infection serves as an evasive tactic. Evasion Tactic is a theory which the “bypass” execution flag for the VBS script supports.
How the Attack Occurs?
Such infected emails appear to have been sent from credible services like FedEx or American Airlines.
All these emails have a Word document attached. This document illegally offers exclusive details about the content mentioned in the message such as information about a courier or bank transaction.
When the victim opens the Word file, they are asked to enable macros.
These macros have commands that initiate downloading of a batch file, a VBS script and a PowerShell file. VBS script is activated by the batch file and this collaboration results in execution of the PowerShell file. The PowerShell file installs the malware onto the computer system of the user.
Macros actually are a set of commands that run automated routines in any MS Office document. This feature has been disabled by-default by Microsoft in Office component due to the risk of being used by hackers. Users trying to perform automated tasks need to enable macros manually.
United States users most affected by Vawtrak Campaign:
Trend Micro’s estimation is that this modified version of Vawtrak steals MS Outlook’s log-in data, personal information stored in Google Chrome, FTP Clients and Mozilla Firefox.
The malware’s analysis reveals that it can bypass the SSL mechanism by hooking into the web browser, reports SoftPedia.
Cybercriminals can easily trick the victim and compel him into providing the two-factor authentication code by serving client modified pages created by running the connection to the bank via their infrastructure. All fraudulent transactions will be implemented from the computer system of the victim.
The number of infections facilitated by this version of Vawtrak Trojan is comparatively higher in the US with 60.71%, then in Japan with 10.22% and third is Germany with 6.83%.