A hacker breached into NASA server and leaked a trove of data that can cause unimaginable damage to the administration.
A couple of days ago it was reported that a hacker going with the handle of @CthulhuSec leaked confidential data stolen from the United States largest police union. Now, the same hacker has come up with another leak of 250GB data stolen from The National Aeronautics and Space Administration (NASA) servers after spending several months inside the administration’s internal network.
It is being reported that around 631 aircraft and radar videos along with 2,143 flight logs and data of at least 2,414 employees is included in the information released by the hacker. The revealed data also included email addresses, names and phone numbers of NASA employees.
The breach was announced on the official Twitter account of @CthulhuSec where he claimed that data may not be harmful for the administration. (Well, that’s for hackers and scammers to decide).
https://twitter.com/CthulhuSec/status/693868995376779264
While the data is out there for the public a hacking group AnonSec claims they have also breached NASA using the same data.
The Zine — Treasure Trove of Information:
In their self-published paper “zine” AnonSec gave away crucial details related to the hack attack, which is now being dubbed as “OpNasaDrones.” The article informs about necessary details such as the hacker group’s motive behind this data breach and the salient technical vulnerabilities that led to such an extensive breach.
While referring to an infamous Trojan that has managed to infect more than 1million computers until now, the hackers wrote in the paper:
“NASA has been breached more times than most people can honestly remember… However, this hack into NASA wasn’t initially focused on drones data and upper atmosphere chemical samples. In fact the original breach into NASA systems wasn’t even planned, it was caught up in a gozi virus spread.”
In the paper, the group also claimed that around two years ago, it purchased “initial foothold” from another hacker who had knowledge about NASA servers. Soon after, the team started testing the number of machines it could “break into” and “root.” Break Into and Root are terms that are used to refer to an account having complete control over any network or computer.
It only took the team “0.32” seconds to brute force an administrator’s SSH password. This can be attributed to the credentials being the default. The hackers then gained deeper access to the intricate system of NASA and acquired an extensive range of login data using a hidden packet sniffer.
Some group members mapped the network while others examined the “different missions, databases, and aircraft” that were listed by the agency. Also, public missions such as “Operation Ice Bridge/OIB” and drones like “Global Hawk” were included among those that were mentioned.
As the team penetrated deeper into NASA’s system, the records of their presence were deleted. They managed to hack the agency’s security cameras and identified the schematics to one of the base camera’s layout. The group then infiltrated the “Glenn Research Center, Goddard Space Flight Center and Dryden Flight Research Center” networks.
When inside, AnonSec stated that they began identifying the presence of various systems; networked devices started “popping up in scans that were not previously visible,” reports the InfoWars
The hackers somehow got hold of a password belonging to the system administrator and thus, they obtained full access to three NAS (network-attached storage) devices, responsible for collecting the aircraft flight logs backups.
The group mocked the system administrator who was in charge of data security at NASA by writing: “Now we had all 3 NAS devices automatically making copies of the logs as they are uploaded from the drones and renaming them to look like semi-ordinary index files.”
As soon as the information started flowing in discreetly, the hackers started analyzing the data acquired from what they believed was a “weird traffic.” The traffic comprised of “pre-planned route option files” that helped NASA to upload flight paths before flights take off.
Few months later, the group decided to carry out a man-in-the-middle attack (MiTM attack) after some group members protested and replaced the drone route file with their own file to crash one aircraft into the ocean.
This is how hacked Israeli drone feeds look like
Secret UFO Reports and Flying Saucer Pictures Released By CIA
AnonSec revealed in “zine” that:
“Several members were in disagreement on this because if it worked, we would be labeled terrorists for possibly crashing a $222.7 million US Drone… but we continued anyways lol.”
The screenshot uploaded by the hackers display their intended flight path, which was cut short when on-ground drone pilots noticed the unusual behavior of the aircraft and forced NASA to reinstate manual control.
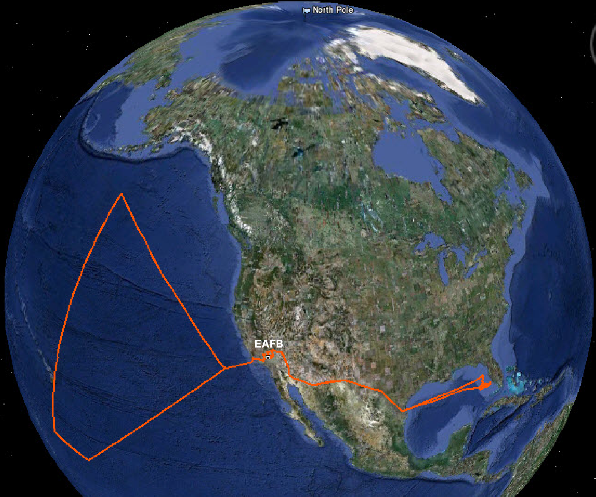
AnonSec wrote:
“This recreated flight is from our attempt to crash the GlobalHawk into the Pacific Ocean but seemed to have been taken off of the malicious pre-planned route and was controlled via SatCom by a pilot once GroundControl realized.”
However in an exclusive conversation with the hacker @CthulhuSec, HackRead asked if AnonSec can hijack drones using his data? The reply was:
“I do not believe at any point drones were in any way hijacked or other such claims. I encourage anyone who says this to back it up with data from the leaked data and other sources. ”
The data can be downloaded from here, however, good luck with the snail speed download.
Note:
HackRead is not responsible for the leaked data nor can we comment on the authenticity of the leaked data. The aforementioned report is a result of information sharing from different publications and hacker himself.
