Researchers at Kromtech Security Center discovered a trove of data belonging to Honda Connect App which was exposed online. The data was stored in two unsecured Amazon AWS S3 Buckets available for public access without any protection
More: 119,000 FedEx users passports, security ID & driving licenses exposed
Simply put, anyone with an Internet connection and basic knowledge of AWS buckets had access to over 50,000 customers using Honda Connect, an app developed for Indian customer of Honda vehicles providing access to detailed information about Honda vehicles and other services.
According to Kromtech researchers, the exposed data contained personal data of users including names, gender, vehicle identification number (VIN), Connect IDs, phone numbers, emails and passwords for users and their trusted contacts.
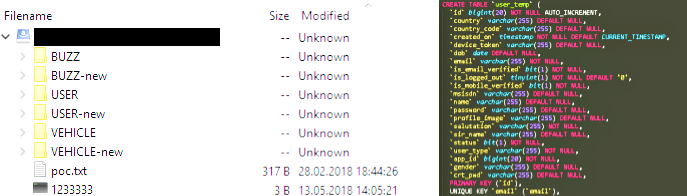
Kromtech researchers further noted that they were not the only good guys to access the exposed data, in fact, the United Kingdom-based IT security researcher Robert Wiggins identified the Honda Connect app databases before Kromtech and left a note on February 28, 2018, urging the company to secure their data.
Wiggins is the same researcher who a few days ago identified how a teen monitoring app exposing plaintext Apple ID passwords of its users stored on an unprotected Amazon S3 bucket. As for Honda Connect, Kromtech researchers contacted Honda India who was slow to respond but ultimately secured both S3 Buckets.
More: Localblox exposes personal data of millions of Facebook & LinkedIn users
If you are hosting your data on Amazon AWS S3 Buckets make sure they are properly secured and not available for public access. Lately, there have been tons of cases in which unprotected S3 buckets have posed a major threat to user privacy. For instance, a few weeks ago, India cricket board exposed data of thousands of players and official hosted on an S3 bucket.
In another incident, researchers identified hackers were mining Monero cryptocurrency on exposed S3 buckets – One of the buckets belonged to LA times while the other was owned by Tesla, Inc. (formerly Tesla Motors).
