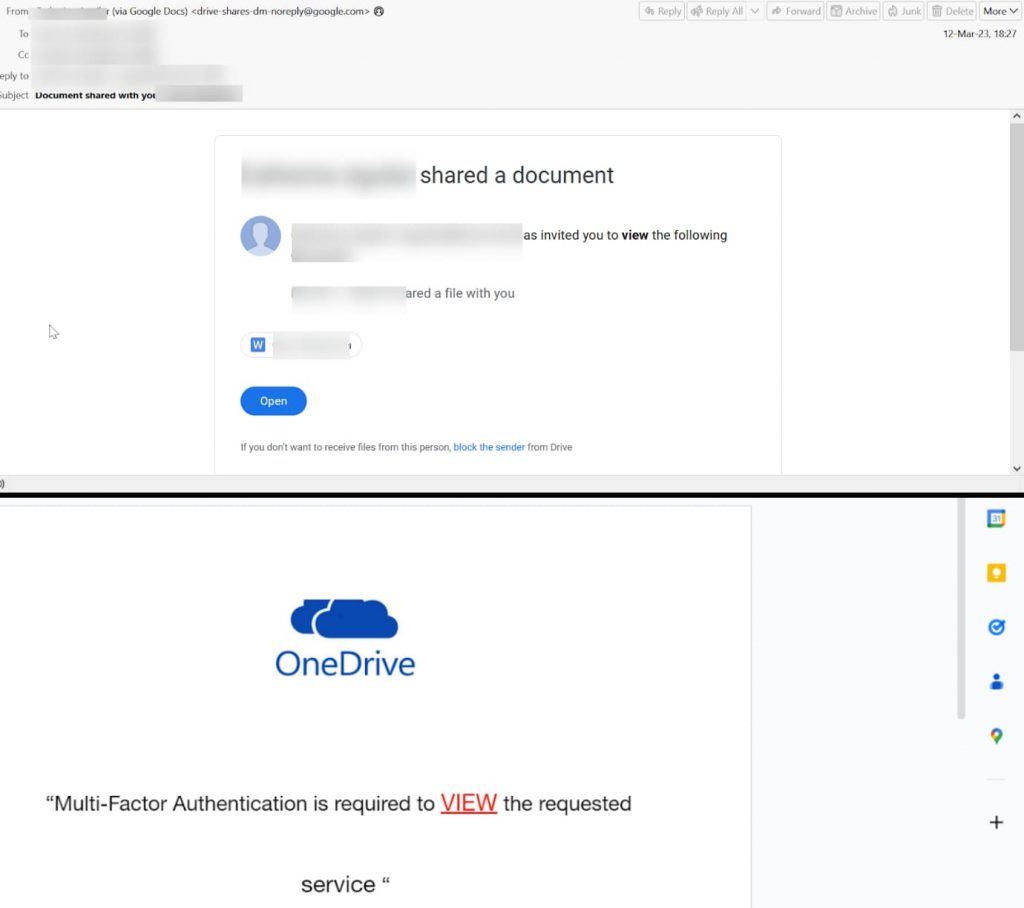
This attack starts with creating a Google document directly sent to the user via email from this spoofed [email protected] address.
Check Point researchers have discovered a new phishing scam campaign that distributes illegitimate URLs by exploiting Google Docs, with the aim of stealing the victim’s cryptocurrency credentials.
According to a research report authored by Jeremy Fuchs, a cybersecurity researcher, and analyst at Check Point Software, and shared with Hackread.com, Google Docs is the latest attack vector phishers are using to redirect users to credential harvesting sites.
Hackers Exploiting Google Docs Services to Distribute Malicious URLs
Check Point researchers observed that legit services of Google Docs are being exploited to send illegitimate messages or URLs, such as the email, pages, and comment features in Google Docs, which indicates the evolving nature of Business Email Compromise (BEC) campaigns.
Dubbing the campaign BEC 3.0, researchers wrote that using legit sites makes it easier for attackers to make their phishing attempts successful because it doesn’t raise any suspicion. In an attack analyzed by Check Point’s team, hackers sent links redirecting to bogus cryptocurrency sites.
How Does The Attack Occur?
This attack starts with creating a Google document directly sent to the user via email from this address: [email protected]. After clicking on the link included in the email, the user is redirected to a legit Google Docs page, supposedly a OneDrive knockoff page, and that’s where the user gets tricked and is made to visit a fake cryptocurrency page. This page was taken down later. Google was notified about these findings on 5th July 2023.
Google’s Response
In a comment to Hackread.com, a Google spokesperson said that since this is not a new or novel attack method, we’ve had strong protections to combat these tactics for years.
“We have numerous layers of protections that protect our users from this class of attack, such as built-in warnings in Docs, and automatic scans in Drive that block the vast majority of phishing attempts.”
Google spokesperson
How to Stay Safe?
Exploiting Google Docs services indicates that hackers are continually working to improve their phishing tactics, especially in BEC. BEC 3.0 has removed much of the previously existing uncertainty among hackers as it doesn’t involve downloading malicious files or software. They now only require user response or engagement to harvest cryptocurrency credentials and steal funds.
BEC 3.0 takes away some of that uncertainty. It requires the best standard link or attachment-based phishing with the social engineering that can make BEC successful. It leverages something we all trust–Google— and processes we all trust–getting a shared document from Google Docs,” Fuchs said.
It is worth noting that there’s nothing wrong with Google Docs; it is how scammers exploit email protocols for their gains, considering that Google cannot be blocked. So, the best line of action is to use AI-powered security mechanisms to simultaneously track all phishing indicators, using a full-suite security program and implementing robust URL security so that all documents, files, and webpages are promptly scanned.
RELATED ARTICLES
- Google Drive accounted for 50% of malicious Office Docs downloads
- LinkedIn Phishing Scam Steals Gmail Credentials Through Google Docs
- Google Docs Phishing Scam Cost Minnesota State Thousands of Dollars
- Royal Ransomware: New Threat Uses Google Ads and Cracked Software
- Research sector targeted in new spear phishing attack using Google Drive