MrAnon Stealer is capable of stealing data and gathering information from cryptocurrency wallets, browsers, messaging apps and VPN clients.
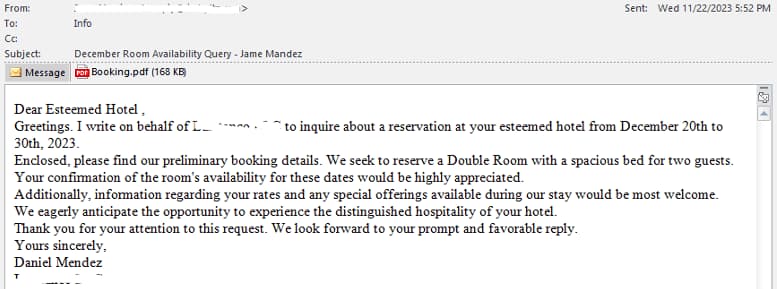
Cybersecurity researchers at FortiGuard Labs have brought to light a new email phishing campaign exploiting false hotel reservations to lure unsuspecting victims. The phishing attack involves the deployment of a malicious PDF file that, once opened, unleashes a chain of events leading to the activation of the MrAnon Stealer malware.
Rather than relying on complex technical details, the attackers cunningly pose as a hotel reservation company, sending phishing emails under the subject, “December Room Availability Query.” The email body contains fabricated holiday season booking details, with the malicious PDF file hiding a downloader link.
Upon closer inspection, cybersecurity experts at FortiGuard Labs uncovered a multi-stage process involving .NET executable files, PowerShell scripts, and deceptive Windows Form presentations. The attackers, posing as a hotel reservation company, skillfully navigate through these stages, using tactics like false error messages to cloak the successful execution of the malware.
The MrAnon Stealer, a Python-based infostealer, operates discreetly, compressing its activities with cx-Freeze to slip past detection mechanisms. The malware executes a meticulous process that includes capturing screenshots, retrieving IP addresses, and stealing sensitive data from various applications.
The attackers demonstrate sophistication by terminating specific processes on the victim’s system and masquerading as legitimate connections to fetch IP addresses, country names, and country codes. The stolen data, including credentials, system information, and browser sessions, is compressed, secured with a password, and uploaded to a public file-sharing website.
According to FortiGuard Labs’ blog post, MrAnon Stealer can gather information from cryptocurrency wallets, browsers, and messaging apps such as Discord, Discord Canary, Element, Signal, and Telegram Desktop. Additionally, it targets VPN clients like NordVPN, ProtonVPN, and OpenVPN Connect.
As for its command and control; the attackers use the Telegram channel as a communication medium. The stolen data, system information, and a download link are sent to the attacker’s Telegram channel using a bot token.
This campaign, active and aggressive during November 2023, primarily targeted Germany, as indicated by the surge in queries for the downloader URL during that period. The cybercriminals behind this operation have exhibited a strategic approach, shifting from Cstealer in July and August to the more potent MrAnon Stealer in October and November.
If you are online, you are vulnerable. Therefore, users are advised to exercise caution when dealing with unexpected emails, especially those containing dubious attachments. Cautiousness and commonsense are keys to thwarting cybercriminals’ attempts to exploit human vulnerabilities and compromise online security.
RELATED ARTICLES
- Booking.com Scam Targeting Guests with Vidar Infostealer
- Silent Ransom Group Utilizes Callback Phishing for Network Hacks
- USPS Delivery Phishing Scam Exploits SaaS Providers to Steal Data
- Iran’s MuddyWater Group Hits Israelis with Fake Memo Spear-Phishing
- LinkedIn Phishing Scam Exploits Smart Links to Steal Microsoft Accounts