MuddyWater is using a fake memo from the Israeli Civil Service Commission as a lure to trick victims into downloading a RAT.
Iranian state-sponsored threat group MuddyWater is targeting Israeli entities in a spear-phishing campaign, reports cybersecurity firm Deep Instinct.
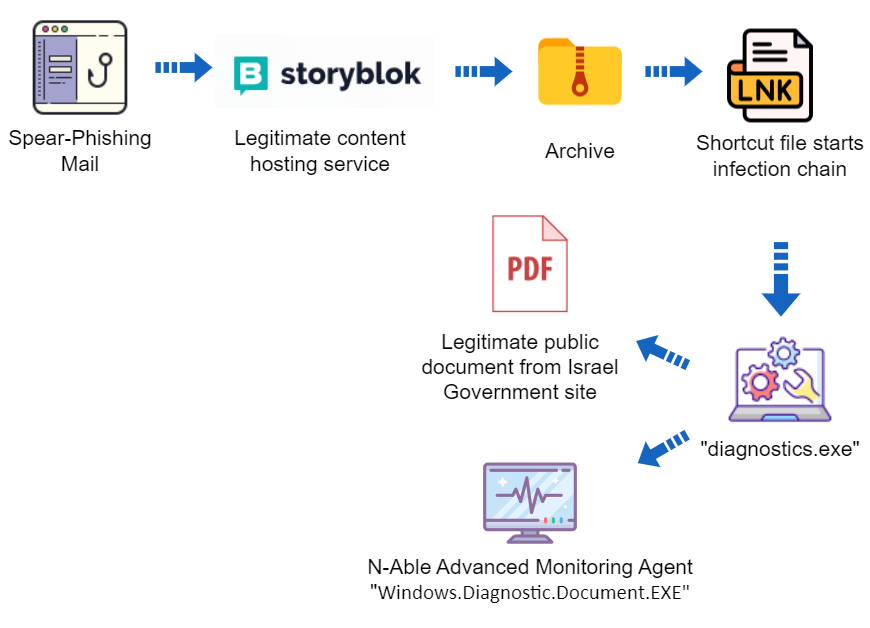
According to Deep Instinct’s treat intelligence researcher, Simon Kenin, MuddyWater is using a fake memo from the Israeli Civil Service Commission as a lure to trick victims into downloading a remote administration tool called Advanced Monitoring Agent (AMA).
This malware lets hackers remotely access their victims’ computers to steal data, disrupt their systems, and perform spying. The threat actor is targeting two Israeli entities to deploy the AMA, a legitimate remote administration tool from N-able.
In their blog post, researchers noted updated TTPs (techniques, tactics, and procedures) in this campaign compared to the group’s previous activities. For instance, the group has used similar attack chains in the past and focused on distributing remote access tools like ScreenConnect, Syncro, RemoteUtilities, SimplyHelp, etc.
However, in this spear-phishing campaign, MuddyWater has used a new technique called ‘eN-Able,’ which is a new type of phishing email designed to evade standard email security filters because the emails combine HTML and JavaScript and appear legitimate. These emails contain malicious code to exploit vulnerabilities in operating systems and email clients.
Another new tactic is called ‘spray and pray.’ This technique is akin to a phishing attack in which a large number of phishing emails are sent to a large number of targets. However, through the spray and pray technique, the chances of success increase dramatically, even if a fraction of the targets fall for the lure.
Furthermore, the group has used a new file-sharing service called Storyblok to launch the multi-stage infection vector containing hidden files, an LNK file that initiates the infection, and an executable to launch the malware. After the victim is compromised, the attacker connects to the infected host using the legit remote administration tool and starts reconnaissance.
Storyblok informed Hackread.com that they are aware of the issue and have taken action by removing the malicious links to prevent misuse by threat actors.
“We remove any dangerous files that we identify or receive reports about. These files were removed and the involved users and IP addresses are banned.”
Dominik Angerer – CEO of Storyblok
In addition to these new TTPs, Deep Instinct notices that the group is leveraging a new C2 framework called Muddy2Go. Using new TTPs indicates that MuddyWater is trying to improve its modus operandi. These findings have been confirmed separately by another cybersecurity firm, Group-IB.
MuddyWater (aka Mango Sandstorm and Static Kitten) is a cyberespionage group that’s believed to be active since 2017. It represents a unit of Iran’s Ministry of Intelligence and Security (MOIS), like other groups, including Agrius, OilRig, and Scarred Manticore.
It is worth noting that this campaign is the latest in a series of targeted cyberattacks against Israeli entities by MuddyWater. In fact, since the escalation of tension between Israel and Palestine, many state-sponsored actors have become active in targeting Israel.
Recently, Hackread reported that Hamas hackers have developed a dangerous new malware dubbed BiBi-Linux to target Israeli systems. This malware can overwrite critical system files, making it impossible to boot up infected systems. The malware was distributed via spear-phishing emails designed to be from legitimate Israeli organizations.
Another spyware campaign was detected in October 2023 in which pro-Palestine hackers delivered malware to unsuspecting Israeli citizens using the rocket alert app.
RELATED NEWS
- Israel’s Channel 10 TV Station Hacked by Hamas
- Hamas hacked the smartphones of over 100 IDF soldiers
- Hamas posed as women to con IDF into downloading malware
- Iranian Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Iranian Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Hamas hacked phones of IDF soldiers with seductive phones of women