Explore insights into the rise of Quishing attacks, the risks associated with QR code exploitation, and crucial preventive measures to protect against this growing cybersecurity threat.
Check Point’s Harmony Email team has reported a startling increase of 587% in QR code phishing or Quishing attacks. This shocking rise was observed between August and September 2023. Researchers noted thousands of QR code-related attacks each month.
In the company’s blog post, authored by Check Point’s cybersecurity researcher/analyst Jeremy Fuchs, explained that hackers lure users with QR codes, redirecting them to credential-harvesting websites. In the UK and Europe, around 86.66% of smartphone users have scanned one QR code at least in their lifetime, and 36.40% scanned a code at least once a week.
It isn’t surprising though because in October, Hackread.com reported the findings of SaaS-base cloud messaging security firm SlashNext, according to which a sudden spike was witnessed in QR code-based phishing attacks.
QR codes are easier to exploit because these encode complex data and a compromised code can quickly redirect users to malicious websites. SlashNext researchers noted that attackers prefer two prominent attack methods to exploit QR codes: Quishing and QRLJacking. Now, Check Point has reported that a massive rise in Quishign attacks has been noticed.
Quishing is a type of phishing attack. Unsuspecting users are tricked into accessing malicious websites or downloading malware after scanning a QR code. There are several reasons why Quishing attacks are on the rise, such as their widespread nature, as millions use them to make payments, scan menus, and access information, which makes them an attractive target for threat actors.
Moreover, QR codes can be exploited to hide malicious links, which can lead users to any website the attacker wants them to without alerting them about suspicious activity.
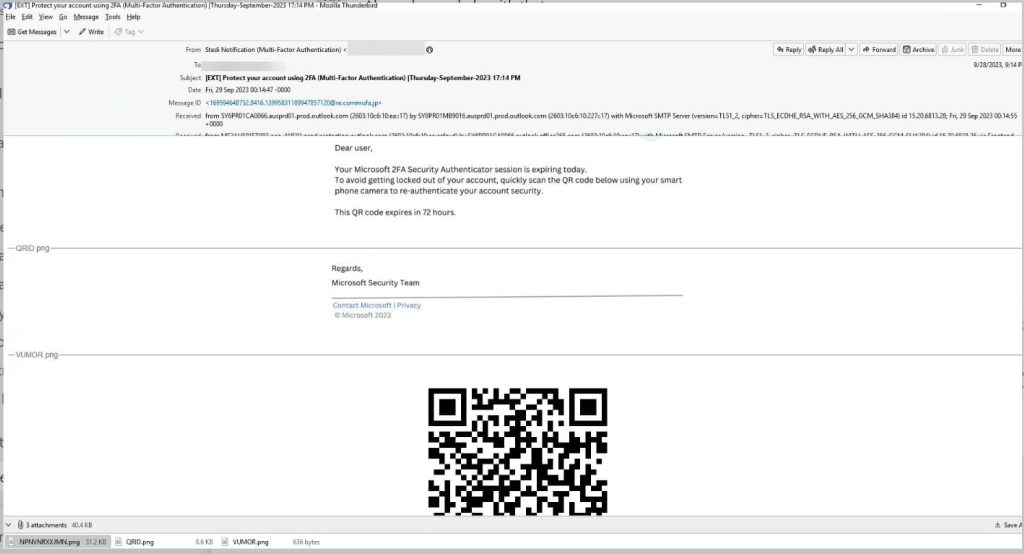
Harmony Email’s team found that lately, attackers are redirecting users to credential-harvesting sites through QR code lures using social engineering to target end-users with emails that can look like this:
The lure used in the email is that Microsoft multi-factor authentication is expiring, and the users must re-authenticate. It is worth noting that the email’s body content claims to be sent by Microsoft, but the sender’s address is different.
To combat Quishing, you must add the OCR (Optical Character Recognition) feature in security solutions to detect malicious QR codes. OCR can help you translate the codes into the URL behind the code, and then you can run the URL through a URL analysis tool. However, suspicion should be raised right when you observe that a QR code is present in the email message body.
Since Quishing attacks are becoming a solid threat, it is essential to exercise caution. Never scan without checking the sender’s source, and avoid scanning codes provided with emails unless you have verified the sender. Security professionals must implement email security that leverages OCR for all attacks. They must implement AL, ML, and NLP-based security to understand the real intentions of a message.
RELATED ARTICLES
- Barcode Reader Apps on Play Store Infected with Adware
- Stream-Jacking: Malicious YouTube Livestreams Aid Malware
- How to make a QR code to accept Bitcoin while keeping it secure
- “Picture in Picture” Technique Exploited in Deceptive Phishing Attack
- Fake ROBLOX and Nintendo game cracks drop ChromeLoader malware