Researchers observed that Tesla was the most targeted brand in the Stream-Jacking campaign, and these scams continue to increase on YouTube.
Executive Summary
- New research from Bitdefender has revealed shocking details of his threat actors hijacking YouTube accounts through stream-jacking.
- The attack targets popular YouTube channels and lures their followers to a fake channel promising exclusive rewards.
- The attackers use different tactics to lure channel followers, such as Livestream popups, infected links, and QR codes.
- Researchers observed that Tesla was the most hijacked brand in this campaign.
- The target accounts mostly had around ten million subscribers and up to 3.6 million views.
Bitdefender has published new research, revealing a sudden rise in stream-jacking attacks targeted against high-profile, popular streaming services like YouTube and aimed at distributing malicious links or lures. The attacks lead to complete account takeover, but in some cases, the followers are lured towards mimicked channels promising rewards.
The focus of this research was stream-jacking attacks against YouTube. Researchers found that cybercriminals target accounts with large follower counts to spread fraudulent messages to the masses. They embed suspicious YouTube livestream popups in the end-users’ feeds promoting the same content but with malicious intentions.
YouTube channels with large followership are desirable in this campaign as cybercriminals can easily monetize them after hijacking by demanding ransom from the owner or distributing malware/scams to their viewers/subscribers. These channels are primarily top-rated brands like Tesla, featuring millions of followers and billions of views.
Crypto scams on YouTube are a serious issue. In 2020, Apple co-founder Steve Wozniak sued YouTube over Bitcoin scams using his name. Wozniak accused YouTube and Google of enabling Bitcoin giveaway scams by failing to take action against them.
“Observing such a “large-scale operation” made us wonder about the channels behind these scams, and, upon closer inspection, we noticed that most of the YouTube channels were, in fact, hijacked/stolen.”
Bitdefender
The modus operandi is generally the same involving phishing attacks. Cybercriminals send emails presenting opportunities for the owner, such as brand collaboration or sponsorship deals.
Sometimes, they may send fake copyright notices from YouTube to the owner. This email, designed as a legitimate business proposition, encourages the recipient to download a malicious file presented as a crucial element of the collaboration offer. It is usually a PDF file carrying the Redline Infostealer malware. It is a large file (over 300 MB) and can easily bypass most standard security mechanisms.
When it is opened, within 30 seconds, it starts collecting vital data from the computer, including session tokens and cookies. With this information, the attacker can access the YouTube channel directly, even if the user has enabled 2FA. After gaining control of the account, attackers re-broadcast or re-upload content after embedding a scam.
The commentary sections of these malicious livestreams could be enabled or disabled, but the catch is that subscribers of 10 to 15 years are allowed to comment. Most of the content featured on the hijacked channels are livestream scams, indicating that the original videos and playlists were made private or deleted.
Attackers also edit channel descriptions as per their requirements, but the channels also feature official Tesla playlists to create legitimacy, leaving the original owner with nothing.
“The process is very likely automated, as conducting an operation on such a large scale would be time-consuming and could potentially give the actual owner of the channel enough time to spot suspicious behaviour.”
Bitdefender
The Second Part
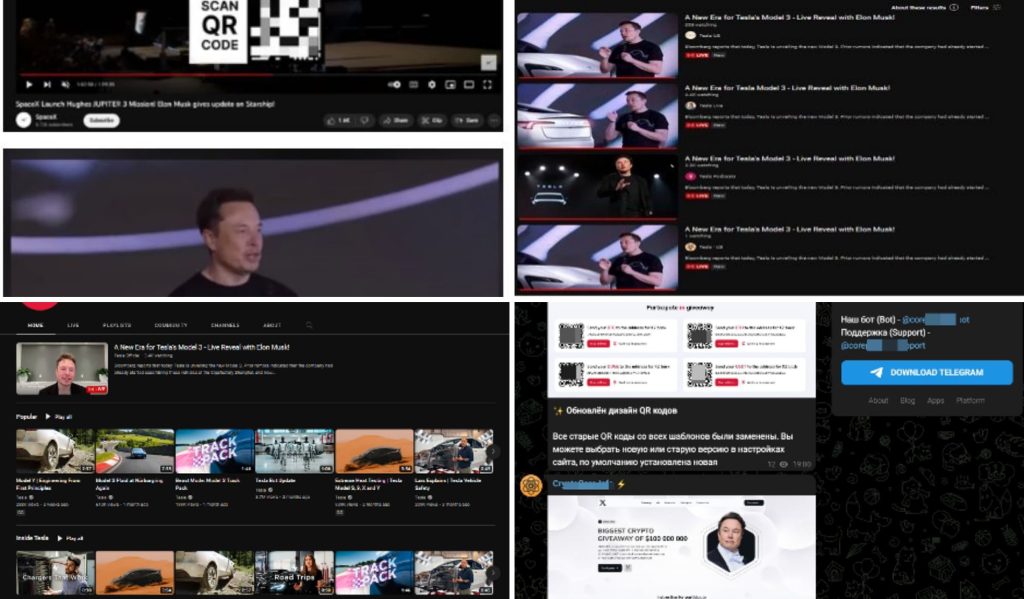
According to Bitdefender’s report, the second part of the attack is targeting account subscribers/viewers with fraudulent offers. Attackers use several techniques to deceive channel subscribers, such as livestream popups, malicious links, and QR codes.
The mimicked channels try to create a sense of legitimacy by using official names, for instance, Tesla US, Tesla Official, Tesla (INC), and Tesla News, but, in reality, most account names involve homoglyphs where the letter L is substituted for an uppercased i (I) and include noise characters such as ‘_’ (for instance, @tesla—us_, @tesla—corp., @tesla_us_live24, etc.).
The maximum number of thumbnails in this attack features Elon Musk. The titles are also the same and less diverse. Such as:
- Rebrands to X!
- A New Era for Tesla Model 3 – Live Reveal with Elon Musk!
- A New Era for Tesla Model 3 – Live Reveal with Elon Musk! Twitter
- Live Stream of Tesla Model 3 2024 Unveiling with Elon Musk!
- CEO Elon Musk Presents: Live Reveal of Upgraded Tesla Model 3
The videos’ descriptions, tags, thumbnails, and channel banners are also the same. Official Tesla streams mostly inspire stream titles. Sometimes, the channel name stays the same due to YouTube’s policy of two changes in two weeks, and when YouTube detects malicious activity, the account sadly gets deleted.
In some instances, researchers noted a QR code embedded in the video leading to a phishing website, and if the comments section is enabled, the same link is posted there by the moderator, and sometimes the link is directly featured on the video. The malicious links promise similar rewards, such as sending cryptocurrency (e.g. bitcoin, Ethereum, BNB, USDT, Inu, Dogecoin, or Shiba) to get double the amount.
Sometimes, the looped audio/video in the livestream are high quality, genuine-looking, deep fakes of Elon Musk. They also suggest a Telegram channel where the attackers promote phishing kits like those featured on the hijacked channel. Over 1300 crypto scams came from the same kits featured on over 150 websites, all with Cloudflare protection.
YouTube channel owners must remain vigilant and use strong, unique passwords, enable multiple layers of security (2FA or MFA), and install software to detect phishing attacks.
RELATED ARTICLES
- Fake YouTube Android Apps Used to Distribute CapraRAT
- New YouTube phishing scam using authentic email address
- British Military’s YouTube Accounts Hacked to Scam Crypto Users
- Hackers using smart home devices to live stream swatting attacks
- Google details cookie stealer malware campaign targeting YouTubers