KEY FINDINGS
- APT36, a Pakistani group known for targeting military and diplomatic personnel in Pakistan and India, is exploiting YouTube to infect Android devices with CapraRAT.
- CapraRAT is a highly invasive RAT that gives attackers control over much of the data on infected devices.
- The attackers are using fake YouTube Android apps hosted on third-party websites to distribute CapraRAT.
- The malicious apps request risky permissions during installation and can extract data, record audio/video, serve as potent spyware, and access sensitive communication data.
- Researchers advise organizations and individuals to evaluate their defences against APT36.
- The attacker is suspected to be a Pakistani group called Transparent Tribe, known for targeting diplomatic/military personnel in Pakistan and India.
- The attacker uses malicious Android apps mimicking YouTube for Android to distribute CapraRAT.
SentinelLabs has published research findings about the tactics an advanced persistent threat (APT) actor uses to target individuals and organizations in Pakistani and Indian military and diplomatic sectors and the Indian education sector.
Report author Alex Delamotte noted that in its recent attack spree, the attacker has used fake YouTube Android apps hosted on third-party websites as the primary lure.
SentinelLabs discovered three APK packages (three Android apps) distributing CapraRAT mobile remote access trojan (RAT). This RAT is linked to a Pakistani actor tracked as Transparent Tribe or APT36.
This actor is known for using malicious/compromised Android apps and targets Indian defence/government entities, particularly those linked with Kashmir affairs. It also targets Pakistani military personnel/entities and human rights activists.
The actor’s objective is to gather intelligence info and use a range of tools to infiltrate Windows, Linux, and Android systems.
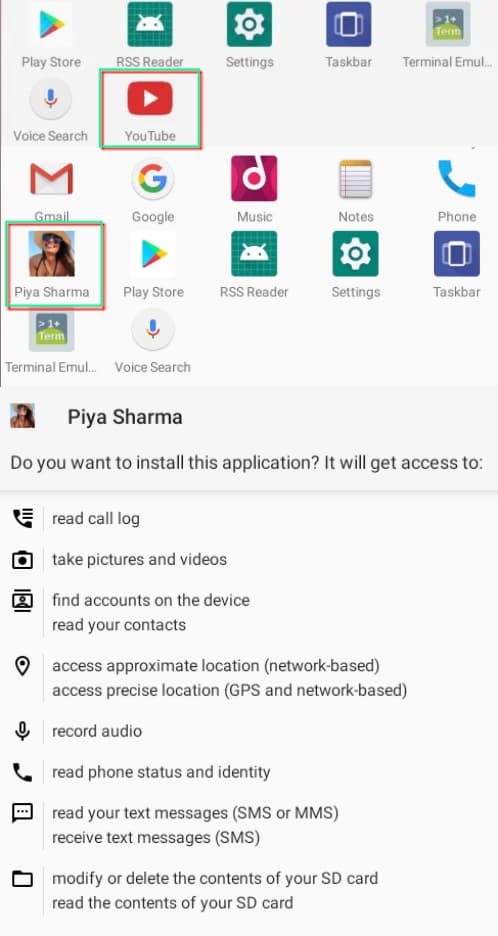
These apps appear as YouTube for Android but are fake versions launched with malicious intentions. The actor has designed these apps to mimic the genuine YouTube app, but keen observation highlights their inherent flaws. For instance, the apps appear more like web browsers than an app because of the use of WebView to load the service and lack many signature features of the original platform.
CapraRAT is a highly invasive tool that gives the attacker control over much of the data on the Android devices that it infects. During the installation process, the apps ask for risky permissions. The malware can extract data, record audio/video, serve as potent spyware, and access sensitive communication data. It can also make calls, intercept/block SMS messages, and override GPS and Network settings. The extracted information is uploaded to the attacker-controlled server.
The malware is promoted as trojanized secure messaging/calling apps under the names MeetsApp and MeetUp, and distributed through social engineering lures. In this campaign, the malicious YouTube apps are distributed via third-party platforms and not from Google Play or Android Play Store.
In their report, researchers found that the APKs were uploaded to VirusTotal in April, July, and August 2023. Two are titled YouTube whereas the third app is linked to a YouTube channel titled Piya Sharma. This indicates the attacker is using this name as a lure as well.
Calling Transparent Tribe a “perennial actor”, Delmotte wrote that the actor displays reliable habits therefore, organizations/individuals should “evaluate defence against this actor and threat.”
It is also important to note that APT36 is a sophisticated threat actor, and organizations + users should be prepared to detect and respond to attacks from this group. Here are some suggestions:
- Android users should only install apps from the Google Play Store or other trusted sources.
- Users should be wary of clicking on links in emails or social media posts from unknown senders.
- Users should keep their devices and apps up to date with the latest security patches.
- Organizations should implement security best practices, such as multi-factor authentication and employee security awareness training.
KEY FINDINGS
- Google Deletes Fake BatteryBot Pro Malware App
- Popular Swing VPN Android App Identified as DDoS Botnet
- Botnet found using YouTube to illegally mine cryptocurrency
- Google details cookie stealer malware campaign hits YouTubers
- YouTube scammers impersonated Elon Musk; stole $150k in BTC
- New MMRat Android Trojan Uses Fake App Stores for Bank Fraud