The Revil ransomware group has released a notice stating that more than 1 million systems have been infected – far more than initially believed.
A couple of days ago, we reported on how the infamous REvil ransomware had targeted over 40 Managed Service Providers (MSPs) compromising more than 1000 businesses in the process. In the latest, we have updated information regarding the ongoing supply chain attack against Kaseya.
Just recently, the group behind the ransomware attack has released a notice stating that more than 1 million systems have been infected – far more than initially believed. These businesses are believed to be based in a range of countries including Canada, the UK, Mexico, and many more.
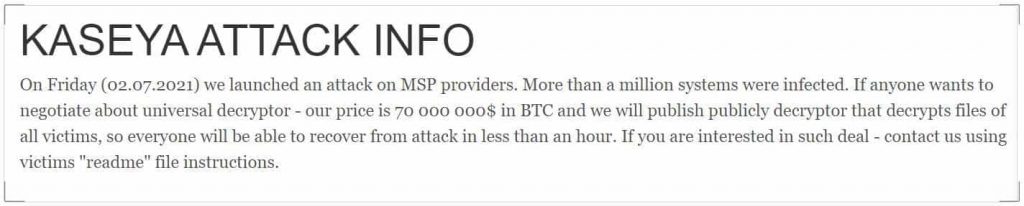
Moreover, the group is demanding $70 million in return for a decryptor that can help restore the data of all businesses compromised. This number has a special significance in that it is the highest ransom amount that has ever been demanded by a threat actor. Previously, we saw how in March earlier this year, REvil had demanded $50 million from Acer.
On the other hand, since this demand is not geared towards any one particular victim, it may be an attempt by the group to get all businesses to consolidate their resources and pay together increasing the total amount of money they get while simultaneously reducing their ransom efforts.
This is a move away from what we saw a couple of days ago when they demanded $5 million from a few MSPs to get the decryption tool.
Kaseya itself on the other hand has released a Compromise Detection Tool which can help clients identify if they too have been compromised.
Talking about the vulnerability that the attackers exploited, the Dutch Institute for Vulnerability Disclosure (DIVD) has stated that these are zero-day vulnerabilities that it had previously reported to Kaseya.
However, while Kaseya was in the process of validating the patch by sharing it with DIVD, the REvil group already exploited these vulnerabilities before customers could access the patch. The Institute in an official blog post states,
“From our side, we would like to mention Kaseya has been very cooperative. Once Kaseya was aware of our reported vulnerabilities, we have been in constant contact and cooperation with them. When items in our report were unclear, they asked the right questions.”
Concluding, at the moment, the US President, Joe Biden has also taken notice of the situation ordering intelligence agencies to conduct an investigation. This shows us the severity of the situation. With time, we will also be able to correctly assess how much financial loss this would translate into which would give us a true picture of its consequences. Kaseya is also actively working and issuing updates on the entire situation.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
