The ride-hailing app database was hosted on an insecure MongoDB server.
Another day, another data breach – This time, security researchers have identified a ride-hailing app exposing personal data of 1 to 2 million Iranian drivers, thanks to an insecure MongoDB database.
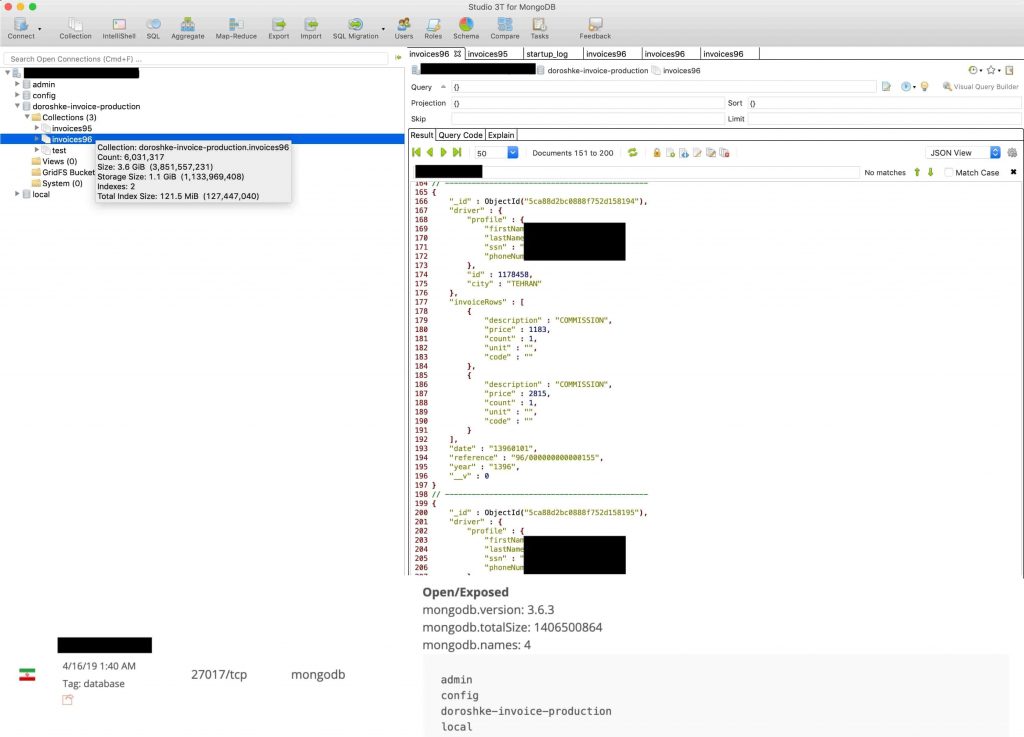
The database (labeled named ‘doroshke-invoice-production) was discovered by Security Discovery’s researcher Bob Diachenko on April 18th which was available to the public for downloading without any authentication.
According to Diachenko’s analysis, the database contained “astonishingly sensitive information” such as full names, city, Iranian ID card numbers in plain-text, phone numbers and invoice data which was divided into two files. The first invoice had 740,952 records from the year 2017 while the second invoice contained 6,031,317 reconds from the year 2018.
Although it is unclear which ride-hailing app company the data belonged to, Diachenko contacted Iranian CERT (The Community Emergency Response Team) about the breach. He also confirmed the legitimacy of the data by contacting some of the drivers who had their details in the database.
MongoDB disaster: Verifications.io breach – Database with 2 billion records leaked
Diachenko believes that the database belonged to Iran’s largest ride-hailing company which could be Snapp (Iranian Uber). Nevertheless, the chances of knowing who owned the database are pretty slim.
Chances are also big that this data was stolen previously from either company and now resurfaced – as a result of human error in the malicious database, Diachenko wrote in his blog post.
It is a fact that insecure MongoDB servers have been causing a great deal of trouble to both businesses and individuals. The situation is so severe that since last year cyber criminals have been carrying our malware and ransomware attacks through these servers due to lack of authentication.
The sensitivity of the matter can be assessed by a test carried out by Diachenko and his team in March 2018 in which they left a honeypot MongoDB database containing 30GB of fake data. Little did they know, it took only three hours for hackers to identify the database before wiping out its data in just 13 seconds and leaving a ransom note demanding 0.2 Bitcoin.
@TAP30_ir @nima @kh_ashkan pic.twitter.com/vk0jqAno1T
— Bob Diachenko 🇺🇦 (@MayhemDayOne) April 19, 2019
“It does not take much effort for outsiders to find unsecured databases and access sensitive information these days. The number one responsibility of all organizations should be to defend their data. Leaving individuals’ personal and sensitive information unprotected is both careless and irresponsible,” said Steve Armstrong, Regional Director UK, Ireland & South Africa at Bitglass.
“The need for comprehensive cybersecurity measures is widely known today; however, many companies continue to display poor stewardship over the personal details belonging to customers, employees, and other parties. Unless organizations begin to respect the importance of protecting customer data, we will continue to see more companies making costly mistakes that have the potential to harm countless individuals,” warned Armstrong.
See: Unprotected MongoDB leaks resumes of 202M Chinese job seekers
If you are interested in reading previous data breaches involving MongoDB servers follow this link.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.