A “secure” cloud storage provider is not so “secure” for customers after all.
Another day, another data breach – This time, researchers have identified a massive trove of data exposed on an unprotected Amazon S3 bucket. The worse part of it is that anyone with an Internet connection could access the data since it was left without any security authentication.
According to vpnMentor‘s research team, the database was owned by Data Deposit Box., a Canadian secure cloud storage provider. An in-depth analysis by the team revealed that the misconfigured S3 bucket contained around 270,000 personal files uploaded by the company’s customers using its secure cloud storage service.
If a company claims to be one of the most secure cloud storage providers then it should stand by its word. However, in this incident, the worrisome part is that among other sensitive data such as usernames, passwords, IP addresses, email addresses, and globally unique identifiers for resources (GUIDs), the database also contained PII (personally identifiable information) of customers – All in plain-text format.
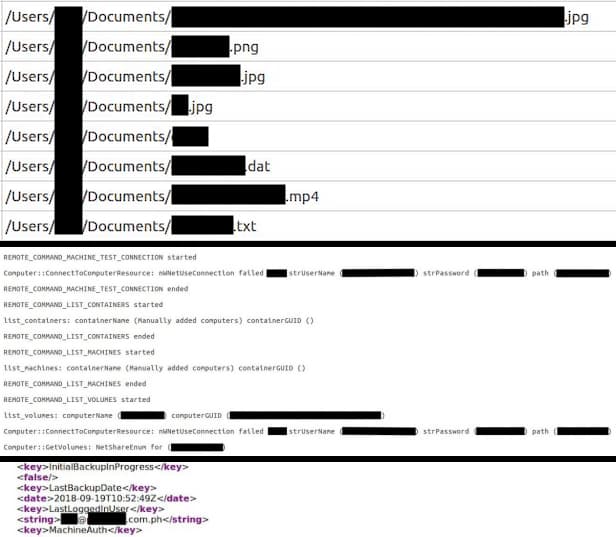
Although it is unclear if the database was accessed by a third party with malicious intent, if it was, it exposes customers to real-life blackmailing, extortion, and identity theft-related scams. An attacker can also use exposed login credentials to hack victims’ accounts on other websites in case they are using the same password.
Nevertheless, this, not only puts their social media and personal email accounts at risk but also opens doors for crooks to distribute malware among their contacts.
As for Data Deposit Box, the incident can be devastating starting with GDPR and customers mistrust who uploaded their highly sensitive records on the site.
The good news is that since the database was found exposed on 25th December, the company was able to secure it within a few days after vpnMentor informed them about the incident.
If you have an account on Data Deposit Box, it’s time to change its password along with its email address. It is also advised that users should rely on dummy email addresses made solely for file sharing and other services that do not require their personal information to signup.
This, as you may already know, is not the first time when an Amazon S3 bucket has exposed such personal data of unsuspecting users. Last month, a plastic surgery technology firm had images of 100,000+ customers exposed due to a misconfigured S3 bucket.
In May last year, another misconfigured S3 database exposed the personal and contact information of millions of Instagram influencers. The list goes on…
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
