While the ThirdEye infostealer is now in town, researchers have already identified several of its variants, all aiming at victims’ data.
FortiGuard Labs uncovered a not-so-sophisticated but highly malicious infostealer while analyzing suspicious files during a cursory review. They named this ThirdEye Infostealer. According to the report authored by Fred Gutierrez, James Slaughter, and Shunichi Imano, researchers became suspicious after spotting an archive file in Russian titled “Табель учета рабочего времени.zip“, which means “time sheet” in the English language.
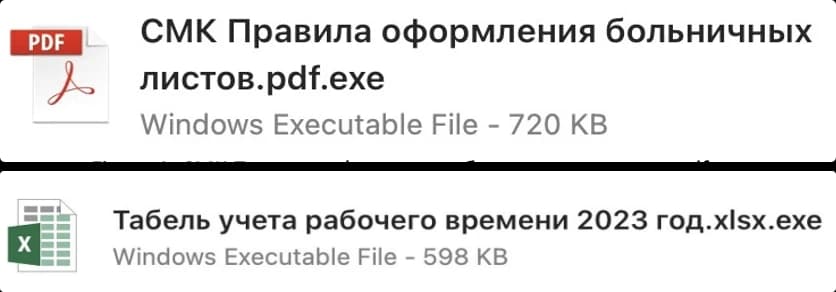
This file contained two additional files, both with double extensions, including a .exe extension and another document-related extension. One of these files is titled “CMK Правила оформления больничных листов.pdf.exe.”
The title means “QMS Rules for issuing sick leave” in the English language. Further investigation revealed traits that researchers had previously seen in ThirdEye infostealer samples they had been detecting since early April 2023.
Various Versions of ThirdEye ThirdEye Infostealer Discovered
The earliest sample of ThirdEye infostealer was discovered on 3 April 2023 at 12:36:37 GMT. This sample collected client_hash, OS_type, host_name and user_name and sent it to C2 server “(glovatickets(.)ru/ch3ckState)” with a custom web request header: Cookie: 3rd_eye=. It was submitted to a file scanning service on 4 April 2023.
A few weeks later, researchers found a variant which had a compile timestamp of 26 April 09:56:55 GMT. This variant collected additional data, including the BIOS vendor and release date, RAM size, CPU core number, user’s desktop files list, list of registered users on the device, and network interface data. However, this version crashes in some virtual machines.
One day later, they found a new variant with just one change: it used a PDF icon. This variant used “(ohmycars(.)ru/ch3ckState)” as C2 communications.
Later, another variant was found which gathered additional data such as total and free disk space on the C drive, domain name, network ports list, list of programs and version numbers, systemUptime, CD-ROM, drive letters volume information, currently running processes list, and programs installed in the Program Files directory.
Another file in the archive WAS titled “Табель учета рабочего времени.xls.exe,” which is a ThirdEye infostealer variant capable of performing the same activities.
Functionalities of ThirdEye Infostealer
in their blog post, FortiGuard Labs’ researchers revealed that ThirdEye Infostealer can steal system data from infected devices, including BIOS and hardware information. In addition, it can enumerate folder files, running processes, and network data.
Upon execution, the infostealer quickly gathers the data and transmits it to a C2 server hosted at “shlalala(.)ru/ch3ckState.” Apart from this, ThirdEye Infostealer does not perform any other function.
While researching, an interesting feature was noted – a string named 3rd eye, from which they derived the name of this malware family. The malware decrypts this string and uses it with another hash value to identify the C2 server. ThirdEye infostealer isn’t too sophisticated; however, it is evolving fast. Some recently collected samples stole more system data than the previously discovered versions.
Moreover, researchers noted that the infostealer targets Windows-based systems with a medium severity level. There is currently no evidence that ThirdEye Infostealer has been used in attacks.
However, since it is designed to collect data from compromised devices and systems, it can come in handy for cybercriminals in launching attacks. Researchers believe that all previous and latest variants of ThirdEye Infostealer are named in Russian, so the attacker is probably eyeing Russian-speaking organizations to deploy malware.