A few months ago, Bluetooth-enabled fidget spinners were in the news for blowing up and putting lives in danger. This time, these toys are in discussion for posing a threat to users privacy and stealing their data.
According to Arun Magesh, an IT security researcher at Payatu Technologies, India; the AiTURE fidget hand spinner app on Play Store is collecting data of other installed apps and sending it to a server in China without their consent or knowledge.

Developed by Chinese firm Shenzhen Heaton Technology Co.Ltd, AiTURE supports Bluetooth connectivity to user’s smartphone. Once the app is installed and connected to the phone, users can create their own patterns, single liners, and spin away.
Arun, on the other hand, conducted an experiment on several applications to check how do they transmit the data to the Cloud. After spending some time on AiTURE fidget hand spinner, he reverse-engineered the Bluetooth communications between the app and the fidget spinner. Upon intercepting the app and the Internet connection, he discovered a huge chunk of data, that is being transmitted to a Chinese server. The identified server’s login page (api.e-toys.cn/passport/login) asks for username and password to access “Background System EToys” login system.
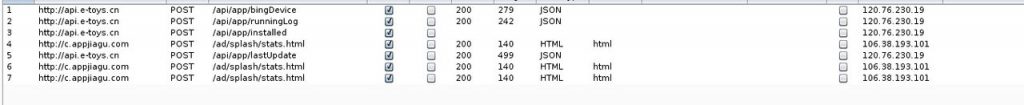
On further analyzing the data packets, the researcher noted that the app sends all the information about the apps installed on his phone to the server in a clear text. Arun believes this data could be used to target ads or even send remote exploits based on 0-days on other installed on phones.
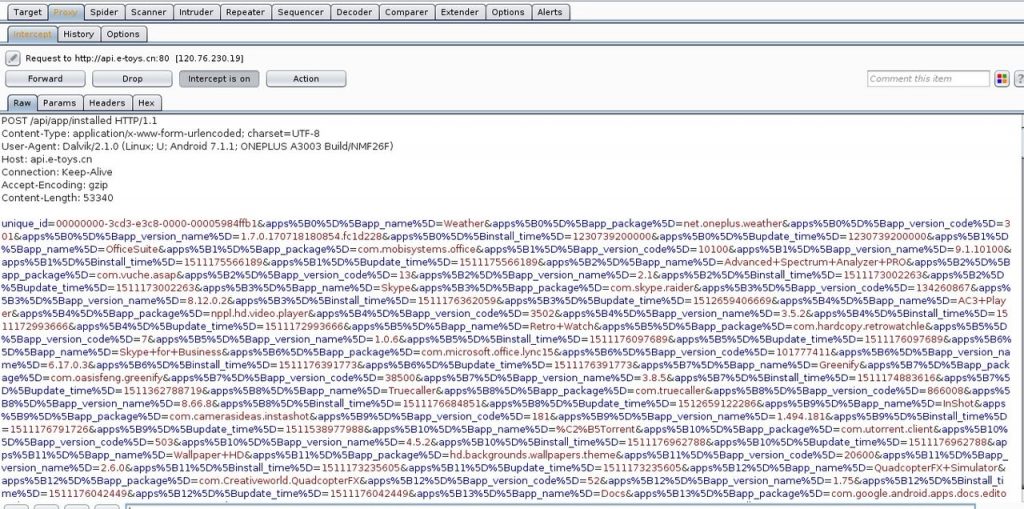
Although the app has only 1,000 – 5,000 installs, it still poses a significant threat to its users since it sends all the information on installed apps along with their version and installation time.
“If they are so smart. Why send it in plain text using HTTP and not HTTPS?? This makes me wonder if all cheap Chinese products which are sold at low prices are sold at the cost of our private data? Are we not safe from anything anymore,” Arun told exclusively to HackRead.
However, encrypted or decrypted, the question is why a fidget spinner app is sending user data to a server in China? Arun’s curiosity about cheap Chinese products makes sense since this is not the first time a Chinese company has been caught getting their hands on user data.
Previously, a Chinese mechanical keyboard manufacturer MantisTek was found spying on users through built-in keylogger in its GK2 model and sending the data to a server apparently hosted on Alibaba Cloud server. In September this year, researchers found popular Chinese keyboard app GoKeyboard collecting data and spying on millions of users.
Those Android users who are concerned about their privacy are advised to avoid downloading unnecessary apps from Play Store and third-party stores. Remember, Play Store itself is home to tons of malware and malicious apps.
