The Windows default Terminal or Remote Desktop Services have become the perfect platform to infect a computer with a new ransomware campaign.
Hackers are using Microsoft Windows to install ransomware in computers, encrypt data and demand ransom of their choice in bitcoin.
In this case, the demanded amount is 4 Bitcoin or $1,000.
This ransomware was initially identified in Greece and Bulgaria because users from these regions were seen to be asking for help on various online forums such as the Bleeping Computer tech.
Nathan Scott, a malware researcher, identified some interesting facts about the ransomware such as it is being installed on all infected devices through brute-forcing the user account passwords.
The ransomware is installed on computers equipped with open Remote Desktop/Terminal Services connections.
Never open an unknown email nor download files from it
After infecting the system, the hackers execute the ransomware executable that locates all network and local drives.
Once a virtual map of all available drives and files is created, the software searches for data files of a particular extension and encrypts them with a strong 2048-bit RSA key.
This is the same system that Cryptolocker uses and is regarded as the most common, nefarious and harmful ransomware family currently affecting computers.
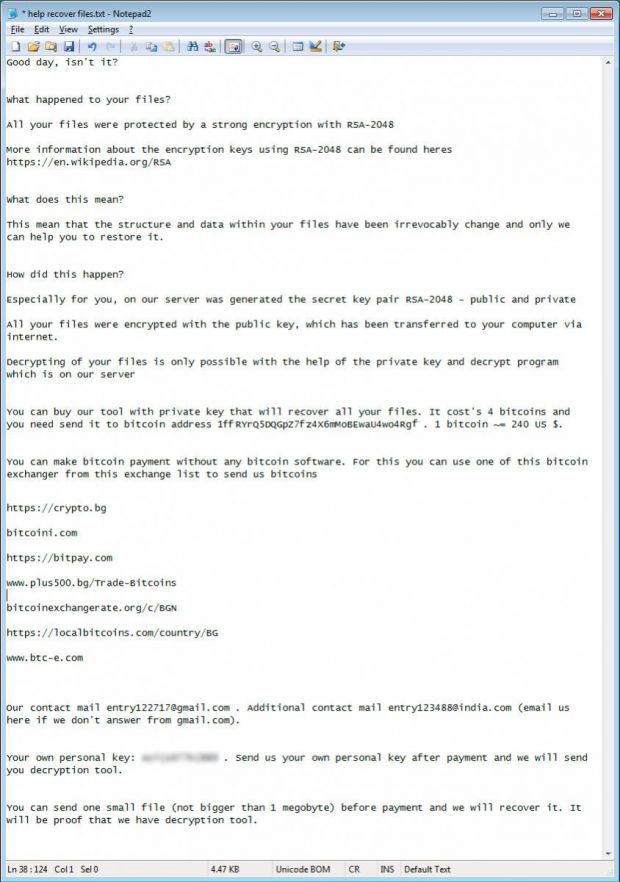
To ensure that the ransomware works properly, a file names “helprecoverfiles.txt” is dropped in every folder that contains the encrypted files.
This particular file contains information about the way the ransom has to be paid and how the encryption could be removed.
The email IDs used in this ransomware campaign are:
[email protected] and [email protected].
There are some methods available for recovering the encrypted files such as if any of the file is synchronized and/or hosted on cloud services such as Dropbox or stored on Google Drive, then it is possible to delete the oor.prefix string and revert the file to its previous version.
Another method that can help is by recovering the hard drive’s shadow volume copies because these cannot be deleted by the ransomware. This act can be performed used ShadowExplorer.
Do keep in mind that these above-mentioned methods can only help in retrieving some amount of lost data and not all of it in case you don’t want to pay the ransom.
Here is a screenshot of ransomware message left by the cyber criminals:
To protect your PC from ransomware make sure never to download any file from an unknown email. In the past, even the Midlothian Village, Illinois, Police Department and Tewksbury Police Department were infected and forced to pay a ransom.
These ransomware scams are not limited to Windows OS, we also reported how hackers are hiding Android ransomware behind fake pornography app in Google Play Store.