The Krasue Linux RAT is quite sophisticated, and equipped with the capability to evade detection through Rootkit and RTSP communication.
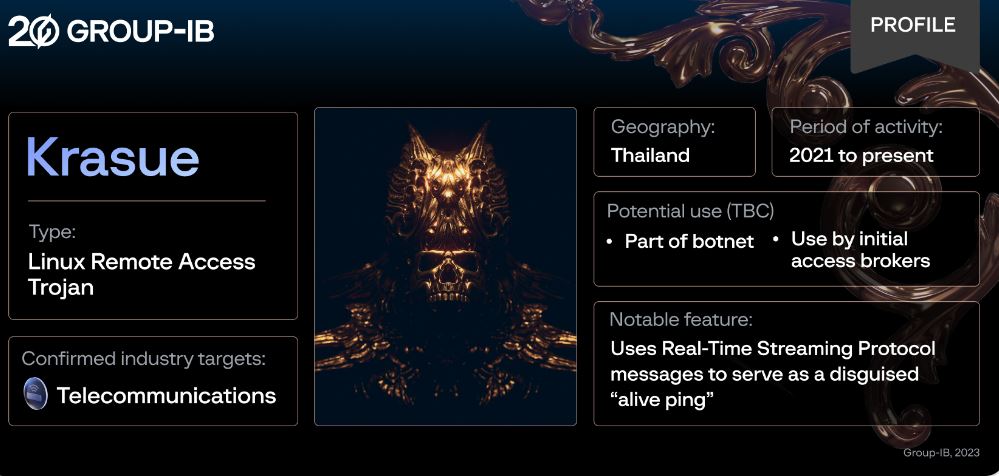
Group-IB, a leading cybersecurity company, has uncovered a sophisticated new Linux RAT (Remote Access Trojan) they have dubbed “Krasue.” The malware is actively targeting organizations, mainly telecommunication firms, in Thailand and has been active since 2021.
GroupIB’s Threat Intelligence unit researchers found that Krause operates by gaining access to the targeted network and uses its rootkit capabilities to maintain persistence and ensure stealthy access.
The researchers are still investigating the initial infection vector and the full scale of the RAT’s usage. However, they believe that potential methods include vulnerability exploitation, deceptive downloads, and credential brute force attacks.
A notable feature of Krause is that it uses the Real Time Streaming Protocol (RTSP) for communication with its C2 server. This is an unusual tactic and is most likely used to evade detection by security software.
Report author Sharmine Low, Group-IB’s Malware Analyst, wrote that Krause is named after a nocturnal spirit mentioned in Southeast Asian folklore. It lets cybercriminals remotely access and control compromised systems and remain undetected for a significant period.
Krasue uses multiple embedded rootkits to ensure compatibility with different Linux kernel versions. Interestingly, as with several other Linux rootkits, Krasue’s rootkit draws its functionalities from publicly available sources, specifically incorporating code from three open-source Linux Kernel Module rootkits.
This embedded rootkit can hook key system calls like kill(), network-related functions, and file listing operations to effectively mask its presence and evade detection. Researchers believe that this RAT was created by the same person who developed the XorDdos Linux Trojan or someone who has access to its source code.
Benyatip Hongto, Group-IB’s Business Development Manager in Thailand, highlighted the company’s commitment and proactive efforts to fighting cybercrime, including the planned opening of a Digital Crime Resistance Center in Thailand and their partnership with leading cybersecurity distributor nForce.
Upon discovering Krause, Group-IB researchers promptly notified their Threat Intelligence customers and published a report with YARA rules, which was shared with Thai authorities including ThaiCERT and TTC-CERT.
This revelation underscores the ever-looming threat of cyber risks and the need for strong cybersecurity measures. Organizations must be aware of threats like Krause and implement suitable security measures like strict access control, regular patching, and advanced threat detection solutions.