123456 was the most used passwords in 2019.
As 2019 came to an end, we got the opportunity to look back and analyze the various cyberattacks that occurred in the past year and what it means for the future. One such analysis has been compiled by SpyCloud which looks at the numerous data breaches that occurred, various attack vectors used, and how users could guard against them.
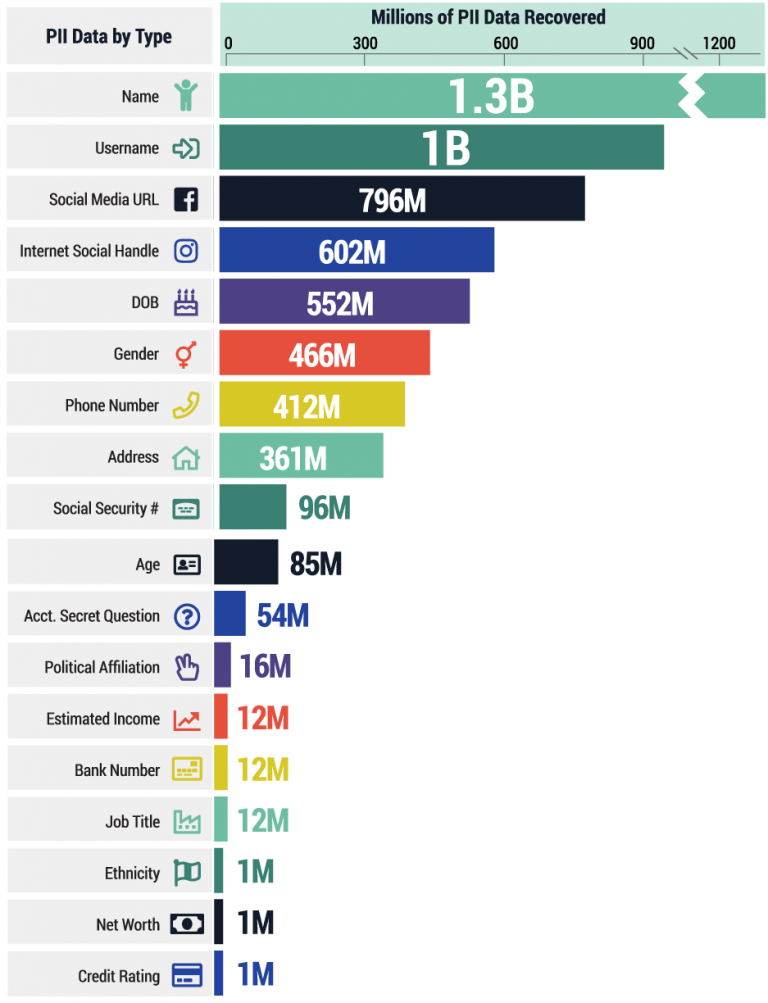
To start with data breaches, a total of 640 breaches were recorded resulting in a recovery of over 9 billion login credentials. These were composed up of usernames & email address associated with their respective passwords.
As a result, attackers could gain access to one’s highly sensitive information including Personally Identifiable Information(PII) & financial information which could be used to steal funds.
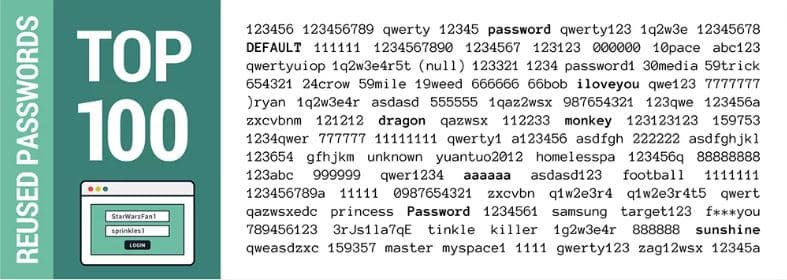
Moreover, since many users re-use the same passwords for their other accounts, this creates a multiplier effect where unauthorized access of one account paves the way for others. This is backed by the fact that the report found 28% of users that had re-used one or more passwords out of which “94 percent of those reused passwords being exact matches.”
See: Here is a list of top 25 worst passwords of 2019
The rest of the 6% although not exactly the same could be identified by attackers using certain tools as they were variations of the original password.
![]() Moving forward, another key finding was that data breaches due to insecure and misconfigured servers were on the rise. We can fairly attest to this seeing how we’ve been covering famous incidents like the Eucodarian and Estee Lauder data breach, both among the various cases that can be attributed to open servers.
Moving forward, another key finding was that data breaches due to insecure and misconfigured servers were on the rise. We can fairly attest to this seeing how we’ve been covering famous incidents like the Eucodarian and Estee Lauder data breach, both among the various cases that can be attributed to open servers.
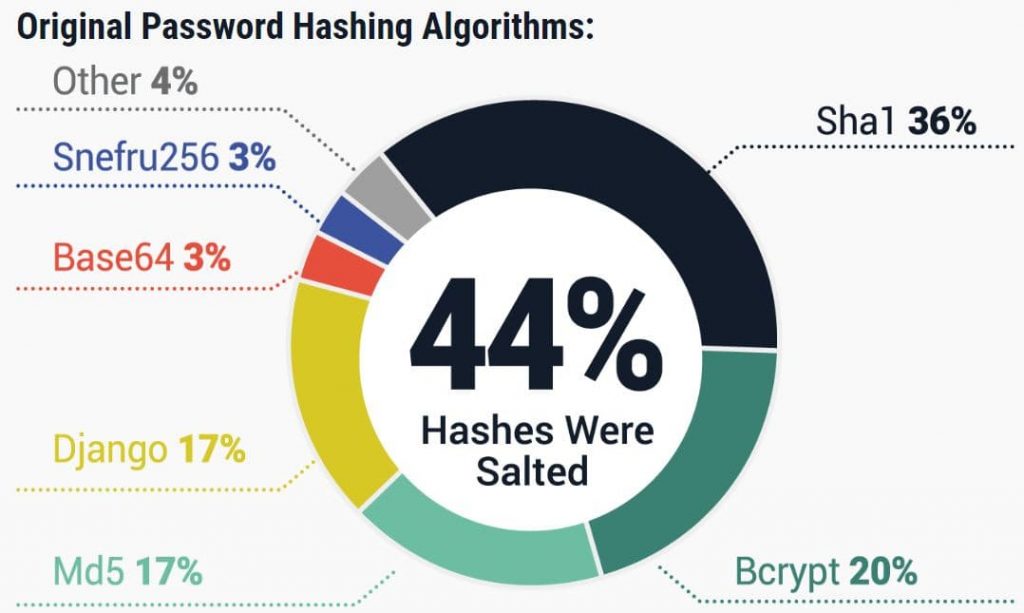
Additionally, hashing algorithms such as MD5 and SHA-1 are being used to protect user passwords in these were also found to be outdated in 53.7% of all passwords recovered leading to questions about the security measures employed.
Elaborating further on the damage caused, Spycloud stated in the report that,
“Its customers have shared that 80 percent of their losses came from just 10 percent of attacks. These attacks can be quite creative, difficult to detect, and highly effective, ranging from MFA bypass via social engineering to SIM swapping, to extortion and blackmail.”
To conclude, apart from users being responsible for putting up strong passwords, it is also important that organizations take strong measures. Some include obvious ones like securing a server with access control mechanisms and using the latest hashing algorithms but a more regular approach needs to be followed in regards to others. This would include compliance with the password guidelines of standardized bodies such as the National Institute of Standards and Technology (NIST) whose measures could significantly reduce such breaches and attacks.
See: Cyber attacks cost $45 billion in 2018 with Ransomware at top
Stay safe online.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.