Users today realize that they may get hacked, logically because they’re no experts at cyber-security and attackers smarter than they are out there. Yet, a bitter truth amidst this realization is that laymen are not only vulnerable, the world’s securest companies also get breached now and then.
To take it a step further, those who take pride in guarding others against such attacks are no exception. We say this in light of recent revelations where NordVPN has accepted that one of its servers was hacked. Oops.
Last night we reported about Avast, the cyber security giant accepting that it was hacked after unknown hackers gained domain admin privileges through privilege escalation by compromising the VPN profile of an employee that did not require 2FA.
Now, NordVPN, in a blog post made yesterday on 21 October explains that one of their leased data centers in Finland was accessed unauthorizedly in March 2018. Simply put: NordVPN was hacked.
See: Hackers cloned NordVPN website to drop banking trojan
The cause attributed is an insecure remote management system in place by the data center provider without the company having any knowledge about it. Elaborating further, they explain that,
The expired TLS key was taken at the same time the datacenter was exploited. However, the key couldn’t possibly have been used to decrypt the VPN traffic of any other server. On the same note, the only possible way to abuse website traffic was by performing a personalized and complicated MiTM attack to intercept a single connection that tried to access nordvpn.com.
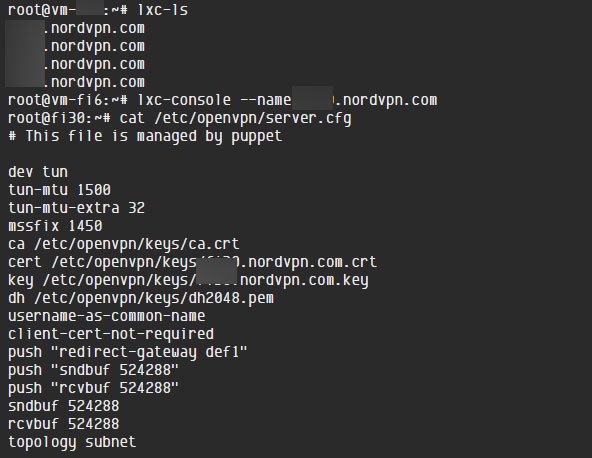
So apparently NordVPN was compromised at some point. Their (expired) private keys have been leaked, meaning anyone can just set up a server with those keys… pic.twitter.com/TOap6NyvNy
— undefined (@hexdefined) October 20, 2019
This, unfortunately, made it possible for malicious attackers to imitate NordVPN tricking users and hence steal their data as Cryptostorm.is explains in the tweet above. However, the good thing is that no user data was compromised and neither was any other datacentre infected in the process. Furthermore, NordVPN’s team has started to move all of their servers to RAM although the process is to be completed next year.
Ted Shorter, CTO at Keyfactor provider of secure digital identity management solutions told HackRead that,
“Hackers gained access to the system at NordVPN that contained this, and at least one other sensitive encryption key. That’s bad, but history has shown us that given enough time and resources, hackers can often find their way into high-value targets: breaches such as this have happened in 2019 more times than I can count. However, a defense-in-depth strategy could have at least prevented the hackers from stealing the private keys.”
It is important to note that this particular incident points to a larger problem. If companies vet data center companies more strictly, such exploits would not take place. Nonetheless even though done in the aftermath, the firm has shredded all of its servers with the compromised data center company and terminated its contract implementing a new set of standards.
See: Avast hacked after attackers gained domain admin privileges
As to why they did not disclose this vulnerability earlier is because of the need to analyze their entire infrastructure including over 3000 servers for any vulnerabilities beforehand. Let’s hope that companies take heed from this incident and step up their security both in and out of the VPN industry.
Did you enjoy reading this article? Kindly do like our page on Facebook and follow us on Twitter.
