The malware attack involves NoxPlayer; which is an emulator used for running Android apps on Windows and macOS.
ESET unveiled that BigNox was compromised in a supply-chain attack. BigNox is famous for its NoxPlayer; which is an emulator used for running Android apps on Windows and macOS. The attack was mainly for surveillance purposes according to the gathered information.
Who’s affected?
The attackers used BigNox’s update infrastructure for downloading the malware onto the user’s computer. This malware can be used for surveillance purposes and the online gaming community is affected by it, but it is observed that this attack was highly targeted.
Out of more than a hundred thousand users that have the NoxPlayer running on their computers, a total of five people got the malicious update. This confirms the highly targeted nature of this attack.
Although any relation between the victims or the reason for them being targeted is yet to be found as they are from separate countries, in essence, Taiwan, Hong Kong, and Sri Lanka.
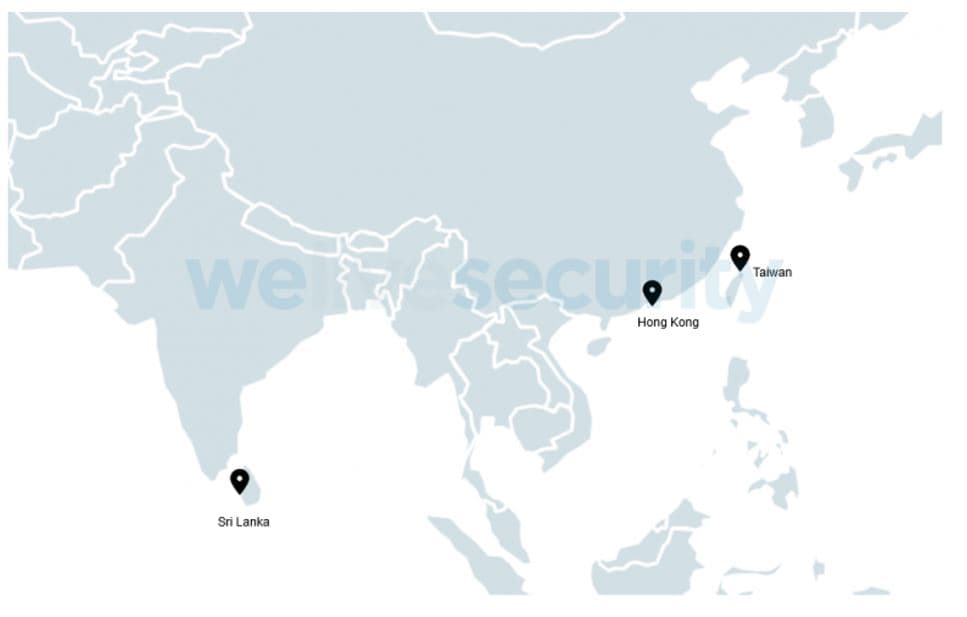
This makes this cyberespionage attack very peculiar as the victims are neither human-rights activists nor government officials which are the typical targets of such attacks instead of online gamers.
When inquired about the said malware attack, BigNox denied being affected. According to ESET’s malware researcher Ignacio Sanmillan,
“We have contacted BigNox about the intrusion, and they denied being affected.”
However, after ESET’s research was published, BigNox clarified that this denial was a misunderstanding. They further claimed that the company is taking steps to ensure better security for their users.
ESET has offered their support for an internal investigation if BigNox needs it, Sanmillan added. He also said that the lack of any relationship between the targeted individuals suggests that the surveillance capabilities of the malware were intended to collect information about the targets related to the gaming community.
How it Happened:
According to the researchers, BigNox’s update mechanism is compromised, and the malware is hosted on their infrastructure (res06.bignox.com). Along with that, BigNox’s HTTP API infrastructure (api.bignox(.)com) may also be compromised. This infrastructure is used to transfer requests and responses between the servers and the clients.
For understanding exactly how the supply-chain attack was carried out, it is important to know how the update mechanism works. NoxPlayer checks for the availability of a newer version upon launch. If a newer version is detected it prompts the user to install an update using a message box.
The user can opt to install the update. If the user opts for the update to be installed, a query goes to the server using the HTTP API infrastructure mentioned above. This retrieves the needed update information. “Nox.exe” which is the main binary application for NoxPlayer will deliver these parameters to the “NoxPaxk.exe” toolbox. The toolbox then downloads the update.
If everything goes well, NoxPlayer will be updated but in the case of the attack under discussion additional payload was download to the victim’s computer as well. This payload was downloaded from servers controlled by the attackers. This proposes that the BigNox API responded with a URL that was altered by the attackers.
The diagram below explains the flow of the intrusion observed by the researchers at ESET:
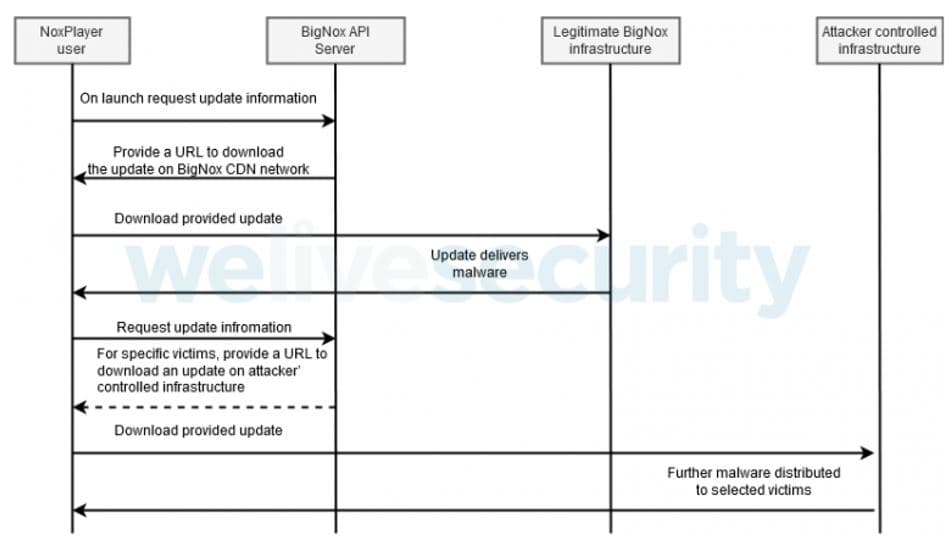
Another speculation is that the actual update was replaced with the malware in BigNox’s servers. The downloaded updates are also not digitally signed like the legitimate updates from BigNox. This means that the Software Build System at BigNox is not compromised and only the delivery system is responsible for the leak.
ESET also wrote in published research that it is very unlikely that this was Man in the Middle (MitM) attack. This is because in Man in the Middle attack, the attackers intercept the communication between two parties for information. But the foothold of the attackers in the BigNox infrastructure and different countries of the targets debunks this hypothesis.
How to be Safe?
The malware has not attempted to gain any financial information due to which ESET believes that the main purpose of this attack was surveillance. ESET discovered a total of three variants of the malware and none of them affected any victim financially.
It is suggested that anyone who has NoxPlayer installed should take the following steps: check your system carefully for signs of infection if NoxPlayer has been used on that machine in the past five months. Do not update NoxPlayer unless there is an official notification that the threat is neutralized.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!
