The latest version of Bifrost RAT employs sophisticated techniques including typosquatting, to avoid detection and complicate efforts to trace its origins.
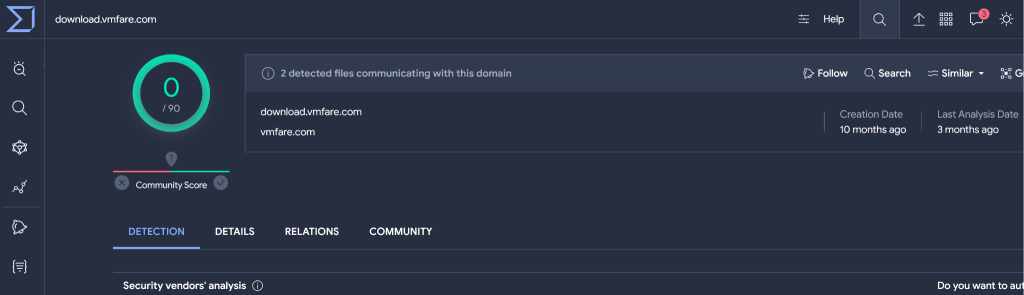
Cybersecurity experts at Palo Alto Networks’ Unit 42 have uncovered a new cybersecurity threat: a new variant of the Bifrost RAT (also known as Bifrose) targeting Linux systems. This variant, utilizing a tricky domain named download.vmfare(.)com, is designed to evade detection and compromise targeted systems.
The malicious domain bears a not-so-easy-to-distinguish resemblance to a legitimate VMware domain, with the only difference being the substitution of the letter “F” for the “W” in the domain: VMware becomes VMfare. For your information, VMware is a leading provider of virtualization and cloud computing software and services.
This type of attack is called a typosquatting attack in which malicious actors register domain names similar to popular ones, relying on users making typing errors to visit their sites, often for phishing or malware distribution purposes. For example, “It’s Google.com, not ɢoogle.com.”
Bifrost, a remote access Trojan (RAT) dating back to 2004, is notorious for its ability to hide within systems, inject malicious code into legitimate processes, and establish covert communication channels with external servers. This allows attackers to steal sensitive data with ease.
The latest version of Bifrost, as detailed by researchers in their technical blog post, employs sophisticated techniques to avoid detection and complicate efforts to trace its origins. By encrypting collected data using RC4 encryption, and the aforementioned domain with a deceptive name, the malware makes it challenging for security experts to thwart its activities.
Additionally, the malware’s recent deployment on a server hosting an ARM version hints at an expansion of its targets.
Analysis of the malware’s code reveals intricate manoeuvres to establish connections and gather data, showcasing its advanced capabilities in evading detection. Palo Alto Networks detected over 100 instances of Bifrost activity in recent months, signalling a critical need for enhanced security measures.
To safeguard against Bifrost attacks, Unit 42 researchers recommend a multi-faceted approach including regular system updates, strong access controls, deployment of endpoint security solutions, and vigilant monitoring of network activity.
RELATED TOPICS
- New Linux Malware “Migo” Exploits Redis for Cryptojacking
- Free Download Manager Site Pushed Linux Password Stealer
- Malicious Ads Infiltrate Bing AI Chatbot in Malvertising Attack
- Hamas Hackers Hit Israelis with New BiBi-Linux Wiper Malware
- Mirai-based NoaBot Botnet Hits Linux Systems with Cryptominer
