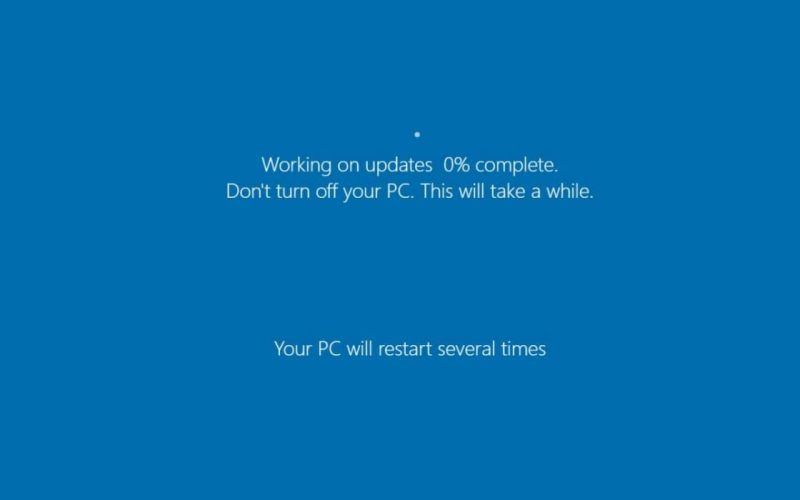
When the fake Windows update UI is launched, the victim believes it to be a legitimate software update process where the progress increment percentage is 100 seconds.
Last month, FortiGuard Labs researchers discovered an emerging new threat called Big Head ransomware that could cause significant harm once it becomes operational. They believe that this ransomware is still under development.
Now, Trend Micro researchers Ieriz Nicolle Gonzalez, Katherine Casona, and Sarah Pearl Camiling have disclosed the inner workings of this ransomware, which is currently under development, in their latest report published on July 7th, 2023.
Researchers have dubbed this .NET-based ransomware “Big Head.” According to their assessment, there is no evidence of successful deployment of Big Head so far, and its developers may be experienced but not sophisticated threat actors.
Several versions of Big Head Ransomware have been spotted so far, raising concerns among the cybersecurity community. It is worth noting that most of the ransomware samples were discovered in the US, France, Spain, and Turkey.
Trend Micro examined three samples for its research, which revealed that Big Head is distributed in a malvertising campaign and as fake Microsoft Windows updates and MS Word installers.
Big Head Ransomware can deploy three encrypted binaries.
- The malware propagator- 1.exe
- The communication facilitator with Telegram- archive.exe
- The file encryption/fake Windows update launcher – Xarch.exe
A variant of the Big Head ransomware launched a fake Windows update, which means that this ransomware is distributed as counterfeit software. When the fake Windows update UI is launched, the victim believes it to be a legitimate software update process where the progress increment percentage is 100 seconds.
On the other hand, the Telegram bot executable (teleratserver.exe) is a 64-bit Python-compiled binary that accepts commands such as Help, Start, Message, and Screenshot to establish communication between the victim and the attacker via the app.
One of the samples deployed the WorldWind Stealer malware and collected a wide range of data, such as browsing history from all installed browsers, a list of directories, and details of running processes.
The third sample deployed the Neshta virus distributing malware capable of inserting malicious code into executable files.
“Incorporating Neshta into the ransomware deployment can also serve as a camouflage technique for the final Big Head ransomware payload. This technique can make the piece of malware appear as a different type of threat, such as a virus, which can divert the prioritization of security solutions that primarily focus on detecting ransomware,” the researchers wrote in a technical blog post.
Like other ransomware, Big Head Ransomware can delete backups, terminate processes, and run system checks to determine if it is running in a virtual environment before encrypting files.
Moreover, it disables the Task Manager so that the victim cannot terminate or investigate its malicious activities and self-aborts if the device language is detected as Russian, Ukrainian, Belarusian, Kyrgyz, Kazakh, Armenian, Tatar, Georgian, or Uzbek. In addition, it has a self-delete function to erase its traces.
This ransomware features diverse functionalities, including stealers, infectors, and ransomware samples. This is the most troubling part of the discovery. After performing encryption, the attackers ask for payment in cryptocurrency for decryption.
The threat actor behind this campaign is still unidentified, but Trend Micro researchers detected a YouTube channel and Telegram username involved in the campaign. The channel’s name is “aplikasi premium cuma cuma” (translation: premium application for free), indicating that the ransomware operator could be an Indonesian.