A new banking malware has been discovered that is targeting bank customers in Brazil. Dubbed as CamuBot, it is identified to be a unique malware because it is disguised as a necessary security module of the bank. The malware can also bypass the biometric authentication feature, which is a disturbing sign.
According to IBM X-Force researchers who discovered the malware, previously discovered banking malware, and Trojans such as BankBot, Emotet, and Kronos worked differently. These were designed to steal online credentials by getting deployed on targeted machines and used complex stealth methods to evade detection. However, CamuBot takes a 360-degree turn in the way banking malware work by camouflaging itself as an authentic security app from the bank.
The focus of this malware, as for now, is online banking users in Brazil and business banking customers are more at risk, reveals IBM Security’s global executive security advisor Limor Kessem. IBM Security researchers identified the malware in August after observing a sudden increase in smoothly targeted attacks against public sector organizations and companies. Most of the targeted institutions and companies relied on social engineering.
The attack involved various steps. The attackers firstly identify businesses that were connected to their preferred bank. After mandatory examination, they make a phone call to someone from that company. The victim is carefully selected as the attackers wanted to contact the one having adequate information about accessing a business bank account. The call is made by an attacker posing as a bank employee, and the victim is tricked into providing the necessary information.
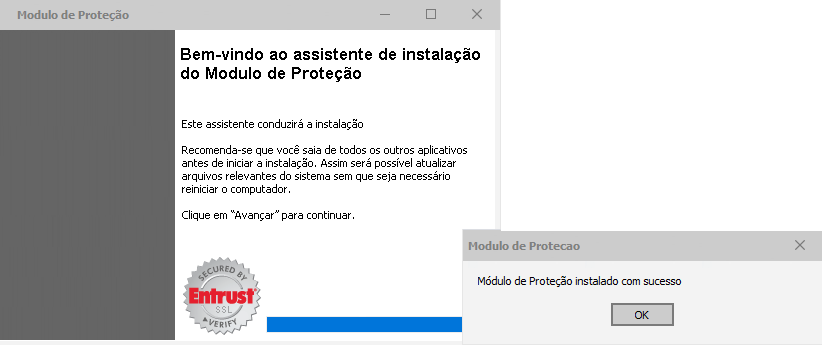
The victim is then directed to an online domain so as to check a security module’s status. The module is designed using the bank’s original logo and color scheme, which is why it appears legitimate. The victim is told that the bank’s security software an update and a new security module need to be installed immediately. This module is the CamuBot Trojan.
As soon as it is installed, a fake Windows app appears featuring the logo of the targeted bank. CamuBot starts writing dynamic files to the folder of this app and managed to create an SSH-based SOCKS proxy module and also adds itself to the Windows Firewall. Once this is done, the victim is asked to visit a phishing website where login credentials are asked to be entered. The malware sends the information to the operators of CamuBot.
According to IBM Security researchers, the proxy module feature is used generally in a “two-way tunneling of application ports from the client’s device to the server.” However, in the case of CamuBot, the tunnel lets the attackers to “direct their own traffic through the infected machine and use the victim’s IP address when accessing the compromised bank account.”
Wondering what happens to that phone call? Well, as soon as the attackers confirm that the credentials are authentic, the one disguising as bank employee hangs up.
The delivery of CamuBot is personalized. Since the malware’s operators target businesses in Brazil, it is very possible that they gather information from local phone books, search engines or professional social networks to get to people who own a business or would have the business’s bank account credentials.
The malware has the capability of bypassing biometric authentication feature as well, which is usually deemed reliable in protecting users’ accounts. CamuBot can also enable remote sharing by installing drivers for authentication devices in order to intercept and steal one-time passcodes used for verification purposes. So far, the malware hasn’t been detected in any other country but attack scope may expand in the upcoming days, researchers suspect.
If you deal with online banking watch out for active banking malware like BankBot, Emotet, and Kronos. Moreover, keep your device updated and scan it with a reliable anti-malware app.
Image credit: Depositphotos.
