Earlier, Chess.com confirmed to Hackread.com that malicious threat actors exploited the “find friends” feature in the platform’s API to extract publically available user data.
On November 10th, 2023, Hackread.com exclusively reported that threat actors had disclosed a scraped database containing information from Chess.com users. The database, containing approximately 828,327 users, was leaked on the notorious Breach Forums.
Over the weekend, a different threat actor leaked another scraped database from Chess.com, affecting nearly 500,000 (476,121) users of the widely used online platform for chess enthusiasts and social networking.
Interestingly, this forum also saw another threat actor leaking a scraped database from LinkedIn just a couple of days prior on the same forum, which contained information from 25 million users.
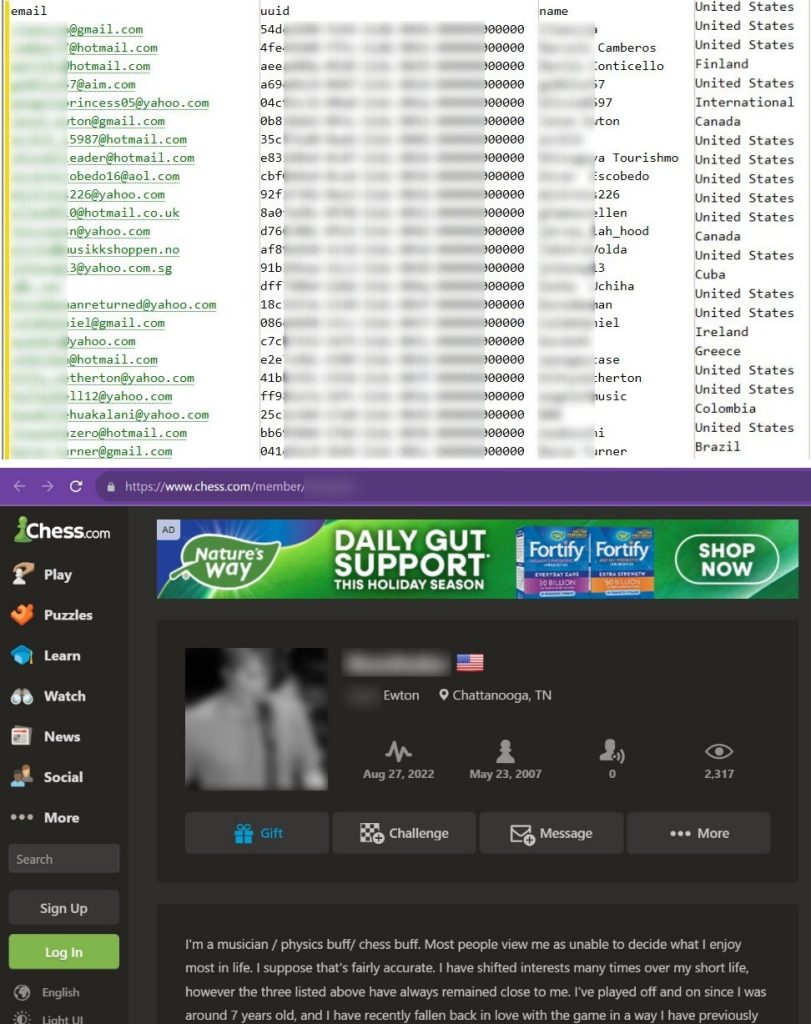
Similar to the previous data breach, the latest incident also involves the exposure of sensitive information. The compromised data includes full names, usernames, profile links, email addresses, users’ originating countries, avatar URLs (profile pictures), Universal Unique Identifier (UUID), user IDs, and registration dates.
In a post on Breach Forums, the threat actor specified that the recently published data leak is distinct and unrelated to the previous one involving the 800,000 scraped records.
According to the threat actor, no data from the earlier leak has been incorporated into the current leak. “Everything was scraped by me and nothing was reused from the 800k leak,” the actor wrote.
A quick analysis by Hackread.com can confirm the actor’s claims to be authentic and no data was taken from the previous leak.
Expect 4 Additional Chess.com Data Scrapes
Since Hackread.com has been monitoring the activities of threat actors on Breach Forums, “DrOne,” the group responsible for the initial Chess.com data leak, has claimed that they have acquired access to four more scraped databases from the site.
According to their claim, these four databases comprise personal information from over 1 million Chess.com users. Nevertheless, it remains uncertain when the databases will be leaked, and whether the actors have any intentions to do so.
This is not a cyber attack – Chess.com is aware of the issue
It is crucial to emphasize that Chess.com has not fallen victim to a cyber attack, and its servers have not been compromised by threat actors. In response to the previous scrape leak reported to Hackread.com, Chess.com affirmed its awareness of the issue. The company clarified that threat actors exploited its public API, highlighting that the breach did not involve a direct intrusion into its servers.
“Today, we learned that some bad actors used our API to collect and release some publicly available member data. This was NOT a data breach. Our infrastructure, member accounts, and data such as passwords are secure,” the company said.
“The bad actors used email addresses found outside Chess.com to search our API via the “find friends” feature and match email addresses to Chess.com accounts. Those Chess.com usernames, email addresses, and other public information such as the account creation date, and last login date were published,” the representative explained.
Still A Danger to Chess.com Users
While it is true that malicious actors have compiled and leaked publicly available information, the inclusion of email addresses in the data poses a significant threat to the site’s users. The leaked information provides a basis for potential malicious activities, such as the creation of fake profiles leading to identity theft.
Additionally, threat actors could leverage the exposed data to search for passwords linked to the compromised email addresses in previous data breaches. Furthermore, the presence of email addresses opens the door for phishing attacks, where attackers may attempt to deceive users by posing as Chess.com in fraudulent email communications.
Web Scraping – Not Easy to Defend Against
Web scraping, also known as data scraping, refers to the automated method employed by software to extract information from websites, particularly to gather specific data from web pages. Given the expansive nature of Chess.com as a large website, the process becomes challenging to block.
In an attempt to thwart scraping activities, large websites implement preventive measures like rate limiting and captcha challenges. Despite these measures, scrapers persistently innovate and devise new techniques to overcome these obstacles. However, not all scrapers are malicious; some engage in data collection for research purposes, ranging from studying social networks to developing machine learning models.
RELATED ARTICLES
- Chess.com flaw allowed access to 50M user records
- Hackers leak scraped data of 87,000 GETTR users online
- Scraped data of 1.3 million Clubhouse users published online
- Twitter Scraping Breach: 209M Accounts Leaked on Hacker Forum
- API Misuse: Hacker Exposes 2.6M Duolingo Users’ Emails & Names
- Data scraping firm leaks 235m Instagram, TikTok, YouTube user data