Google is yet to delete the malicious Chrome extensions reported by security researchers.
One major problem with user-generated web stores is that malicious players find their way in more than usual. This has been very true for both the Google Play Store and the Chrome Web Store.
In a similar case shedding light on the latter, a researcher from AdGuard named Andrew Meshkov has discovered that over 80 million people have been the victims of fake ad blocker extensions on Chrome Web Store.
These extensions can be divided into 3 distinct groups, each engaging in different activities by defrauding users:
1. 295 Extensions with Steganography
These extensions are not only limited to ad blockers and also include other niches such as Wallpapers.
How these works is that once they are installed, they sit idle for a while and only start acting maliciously after receiving a command from their remote server. They do this with the help of loading an apparently harmless script which eventually evolves to track the pages opened by the user and then loading an image with an embedded ad from its own domain name on the respective page.
Clarifying, the researcher’s wrote in a blog post;
This loaded image has ads ‘coded in’, and it tries to insert these ads. This technique is called Steganography and it’s often resorted to by malware developers.
In a Steganography attack, hackers hide malicious data within another file or a message to avoid detection; the data is then extracted when directed by an attacker.
2. 6 Cookie Stuffing Extensions
Having a total number of 1.65 million users, these extensions also start operating after receiving a command from their server. They do so by tampering with the browser’s cookies to reflect “special affiliate cookies” and then earn commissions on the purchases a user does from the seller’s website.
See: These Chrome extensions & Android apps collect your Facebook data
An alarming aspect uncovered here is that according to AdGuard, the code used in the extensions is the same that was exposed back in 2019 but despite this, it evaded Google’s filters leading users to harm’s way. The list of the extensions is as follows:
uBlocker — #1 Adblock Tool for Chrome, 1,000,000+ users (Deleted)
Video Downloader professional, 300,000+ users (Deleted)
Dark Theme for Youtube, FB, Chrome, 100,000+ users (Still not deleted by Google)
AdBlock — Stop Ad on every Site, 100,000+ users (Still not deleted by Google)
2048 Game, 100,000+ users (Deleted)
Music Saver, 60,000+ users (Deleted)
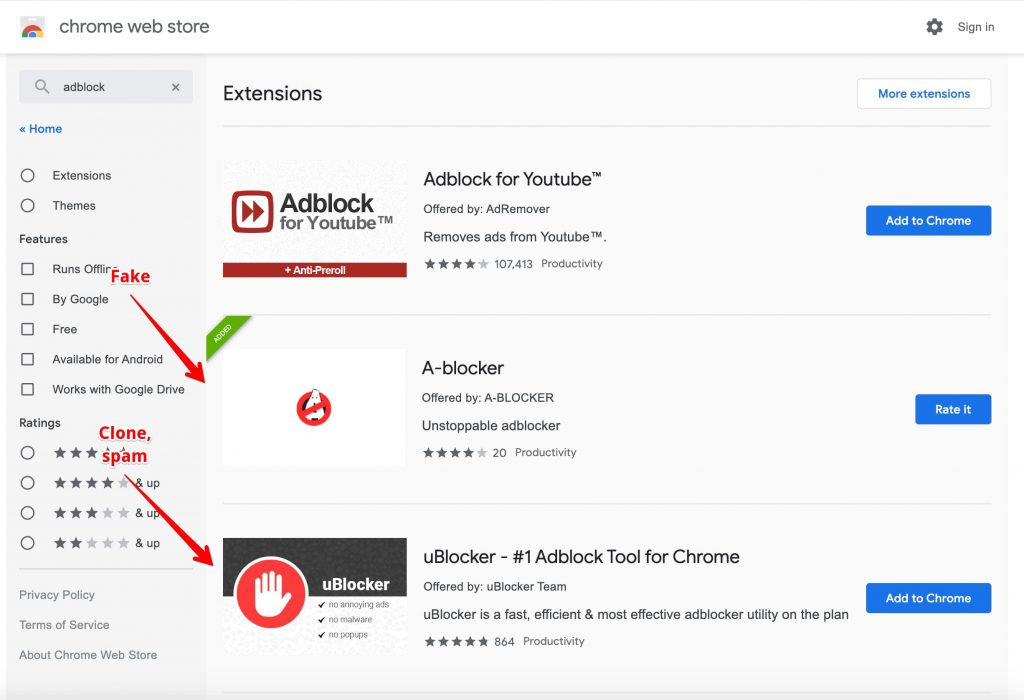
3. Spamming Extensions
The last group hasn’t really engaged in malicious activities, nonetheless has engaged in a range of behaviors that are damaging to the ecosystem in itself. These include listing a false number of active users, copying the source code of other ad blockers, and even questionable developer practices such as loading code from Google Tag Manager (GTM) which can be changed anytime to conduct any sort of malicious behavior by the owner of the GTM account.
Although the number of such extensions is unknown, the top 5 alone bring in 10 million users.
See: Over 20 million Chrome users have installed fake malicious Ad Blockers
As an example of the active users’ problem, one extension named Adburner boasts 1,000,000+ users yet only has 63 reviews as of now. For anyone with common sense, this seems like a very uneven ratio, one that is most likely not backed up by real numbers.
Conclusion
In summation, Google needs to step up its game of removing such extensions quickly when reported by users. We say “reported by users” because as the researcher has stated in this case, 3 weeks have passed since he notified Google through their bug bounty program but till now, only a few extensions have been removed.
On the other hand, the “Report Abuse” button which is more accessible doesn’t yield any results either creating a nightmare for legitimate developers who are having their listings overcrowded by the bad guys.
Here a few tangible solutions that could be put in place by Google:
- Do not allow remote code and instead make extension developers “migrate to Manifest V3“.
- Ask for legal information from developers that can be used to prosecute them in the real world if they are found engaging in malicious or fraudulent behavior.
- Dedicate more employees to keep a check on the extensions in-store and also review abuse reports.
By these, we believe Google could go a long way to help protect users. If you are one of those users who have installed the aforementioned extensions it is advised to get rid of them.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.