If you frequently use Facebook Messenger then we advise that you open attachments in your messages a bit more wisely than before. Researchers at renowned cyber-security firm Trend Micro have discovered a malicious new cryptocurrency mining malware that specifically targets Facebook Messenger users . The malware has been dubbed as Digmine. It is hidden in a video file bearing the title video_xxxx.zip, and it is capable of infecting the entire machine if this file is opened and executed by the user.
According to Trend Micro’s blog post, the malware installs a fake Chrome extension, which lets it access the Facebook profile of the victim and also send messages containing the malware file to all the contacts on the victim’s behalf. This is how this campaign is spreading so rapidly. However, the campaign is mainly effective on the desktop version of Google Chrome whereas it is not infecting users who accessed Facebook Messenger on mobile.
Moreover, when Digmine is installed on the machine, it keeps downloading other components, which includes a cryptocurrency miner, which uses the PC for mining Monero, a popular cryptocurrency. Miner.exe is the mining component, which is basically an iteration of XMRing, an open-source Monero miner. This miner has been reconfigured to launch via config.json file and there is no need to receive parameters from the command line. Specific HTTP headers are used by the downloader and mining component for establishing communication with the command-and-control server.
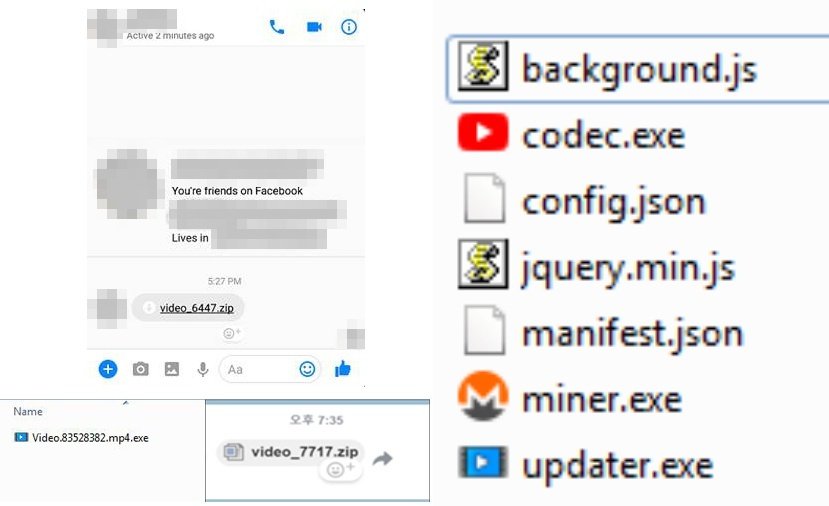
It is also capable of performing other routines including the installation of autostart method registry and system infection marker. It can search and launch Chrome browser to load the infected browser extension retrieved from its command-and-control server. Since the attackers launched the extension through the command line, therefore, they were able to bypass Chrome Web Store scanning, which is responsible for loading and hosting all Chrome extensions.
The malware is currently active in Thailand, Ukraine, Venezuela, Azerbaijan, Vietnam, South Korea and the Philippines but Trend Micro researchers noted that the malware would definitely spread elsewhere because of its default propagation function. The malware was firstly spotted in South Korea.
The malware is coded in Autolt and the file that appears to be containing video is actually an Autolt executable script. This means, if the Facebook account is set to be on automatic log-in then the malware will exploit Facebook Messenger so that the malicious link is sent to other friends of the user.
Facebook reportedly has removed all the links connected to Digmine but it is suspected that hackers would again target users by modifying the current links or by adding fresh code to hijack the user’s account or at least exploit it in some way. As of now, Digmine’s aim is to stay on the infected system for as long as possible and to infect as many computers as possible to get more money.
Facebook states that a number of automated systems are maintained by the social network to stop malicious links and files from invading Facebook and its Messenger app but even then if the computer gets infected with malware, the company will compensate by providing free anti-virus scan conducted by its trusted partners.
