Today, we at HackRead have discovered a sophisticated malware scam that tricks users into downloading fake Google Chrome browser installer but in reality, the file is infected with malware that installs Potentially Unwanted Programs (PUP’s) on Windows devices and connects to certain servers to receive commands from the remote attacker.
Hackers using Google Adwords for this scam
Google AdWords is an online advertising service that lets users pay Google to display advertisement on prominent slots during its search engine results. For instance, if the user does a Google Search using the term “Download Antivirus,” the top slot will display advertisement. In some cases first four search results display ads paid by people or companies to get quick sale or traffic.
Below is an example screenshot of Google Search Engine results that simplifies the difference between paid search and organic search results. “The top10” Free Anti-Malware 2018 result is an ad while Malwarebytes link is a result of the organic search.
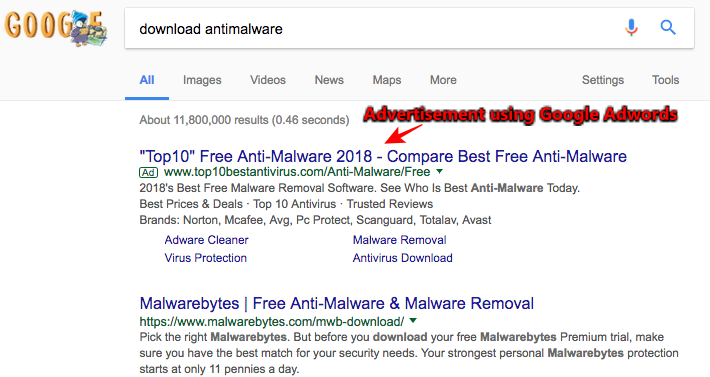
In this malware scam, hackers are taking advantage of Google Adwords service and apparently paying Google to display their website link at the top. But it seems like Google does not scan links before accepting advertiser application or displaying the results to the masses.
Although Google Search Results are linked to user browser cookies and/or varies from country to country, we played with “Download Google Chrome” keywords on Google and found out that the very first search result belongs to an advertiser which once clicked takes the user to a site.google.com link developed using Google Sites service.
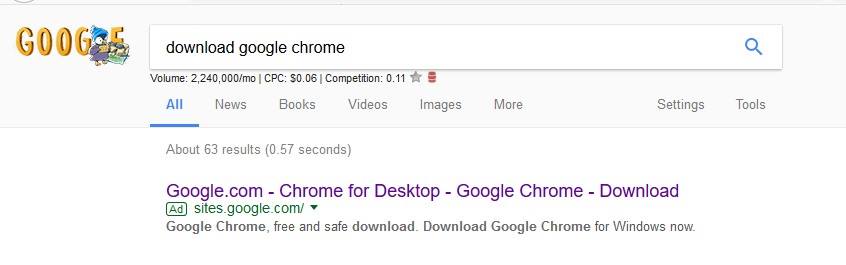
Hackers spreading malware using Google Sites
Google Sites is a structured wiki- and Web page-creation tool offered by Google as part of the G Suite productivity suite. The goal of Google Sites is for anyone to be able to create a team-oriented site where multiple people can collaborate and share files. In this case, however, once the user is on the Google Sites link it tricks users into believing that they are on the authentic Google Chrome browser download site.

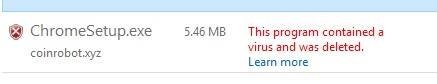
Upon clicking on “Download Chrome” tab, users are taken to a Google Drive link that drops a download file on the device. The download file is labeled as ChromeSetup.exe and detected as a virus by Windows Defender Antivirus, however, its relation with Coinrobot.xyz is unknown.
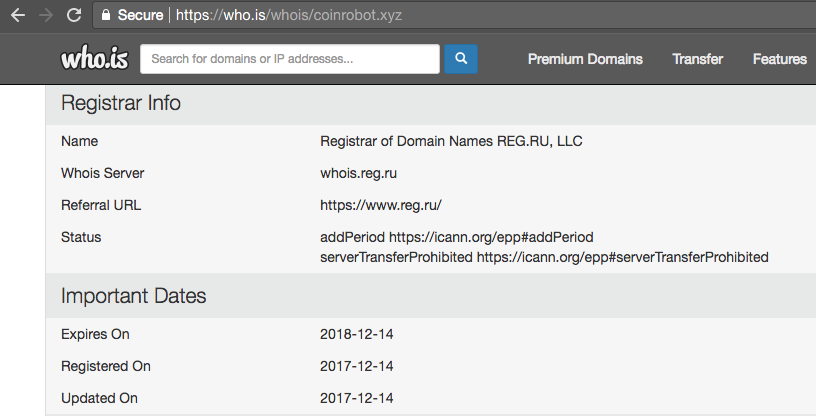
A look at Coinrobot.xyz website shows it is a Russian language website that provides cryptocurrency miners to users. However, a background check on Coinrobot.xyz shows the domain was registered on December 14th, 2017 and is used for the sole purpose of spreading malware that targets Windows users and possibly use their computing power to generate cryptocurrency for cybercriminals.
Furthermore, upon scanning the malware file on VirusTotal seventeen antivirus software came up with the following results:
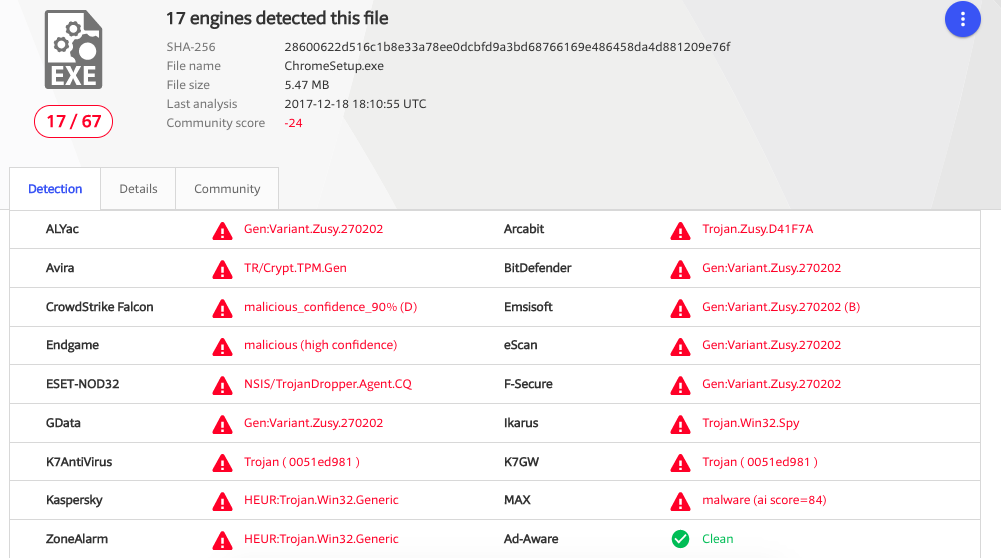
Kaspersky has identified the file as “HEUR.Trojan.Win32.Generic” which according to MalwareTips:
Download and install other malware.
Use your computer for click fraud.
Record your keystrokes and the sites you visit.
Send information about your PC, including usernames and browsing history, to a remote malicious hacker.
Give a remote malicious hacker access to your PC.
Advertising banners are injected with the web pages that you are visiting.
Random web page text is turned into hyperlinks.
Browser popups appear which recommend fake updates or other software.
Scam reported to Google
We at HackRead believe in online security and busting scams like this one. We have already reported the incident to Google and hopefully, the issue will be resolved soon. As for the users; the lesson is never to click links on the Internet without verification but when hackers can trick Google into using its own platform such as Google Sites and Adwords to spread malicious content, one cannot blame unsuspecting users for falling for the scam.
Not for the first time
This is not the first time that hackers have used Google Adwords to trick people online. Previously, fake Bittrex cryptocurrency exchange site also used Adwords service to display advertisement on the top slot of Google Search Engine. The campaign did not only trick Bittrex users into believing that they are on an authentic site but also stole their funds. More details about Bittrex phishing scam are available here.

