Tor proxy owners are replacing Bitcoin payment addresses to divert payments from ransomware victims to their own wallets.
The IT security researchers at Proofpoint have discovered a new type of attack/scam in which cybercriminals are becoming victims of other cybercriminals – In this attack, cybercriminals are found using Tor proxy sites to steal Bitcoin which were originally earned by other cybercriminal groups as a result of ransomware attack.
Cybercriminals stealing from Cybercriminals
In a ransomware attack, hackers infect the computer systems of unsuspecting users with a malicious software which locks their data and asks the victims to pay a ransom in Bitcoin or Monero cryptocurrency through Tor Browser or Tor proxy sites. Due to the unprecedented growth of the value of cryptocurrencies, there has been an increase in ransomware attacks accordingly.
But since not every user is familiar with how Tor works, desperate victims rely on Tor proxies to send ransom payment and receive the decryption key for their data. However, these proxies are owned by people (web administrators) who by default can work as man-in-the-middle and keep an eye on whatever a user does on the proxy.
According to Proofpoint security researchers, the proxy owners of the site Onion.top have been found to be modifying the transit source of web pages used for payments and diverting Bitcoin payments from ransomware victims to their own wallets. This means once the victim performs a transaction, the ransom money goes to administrators rather than the hackers behind ransomware attack. This also means that administrators are preventing victims from receiving their keys and stealing from hackers.
“This appears to be the first scheme of this type affecting both ransomware victims and operators,” noted Proofpoint.
How the scam was unearthed
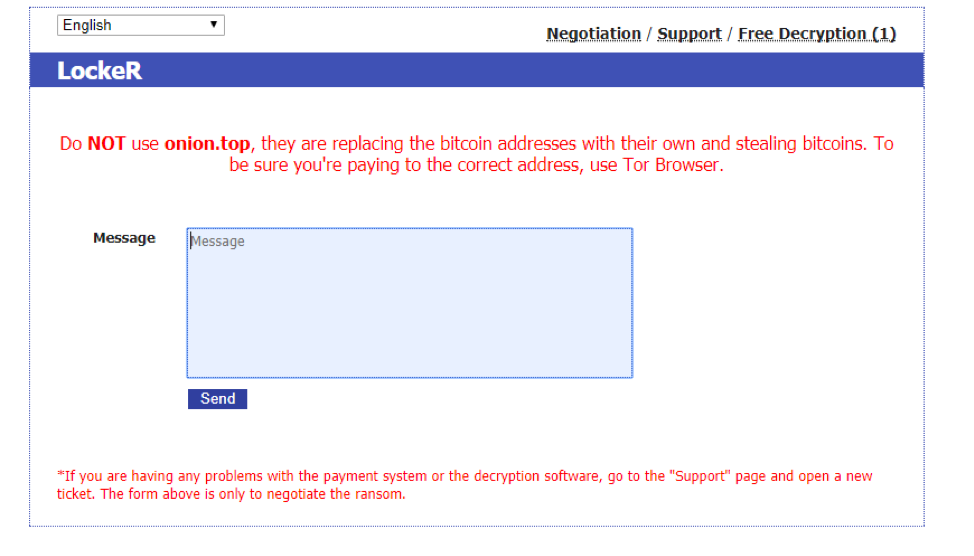
The researchers first learned about the scam during LockeR, Globelmposter and Sigma ransomware campaigns. In LockeR campaign, researchers identified that its payment portal warned users of not using onion.top proxy to send ransom payment.
“Do NOT use onion.top, they are replacing the bitcoin addresses with their own and stealing bitcoins. To be sure you’re paying the correct address, use Tor Browser,” the warning said.
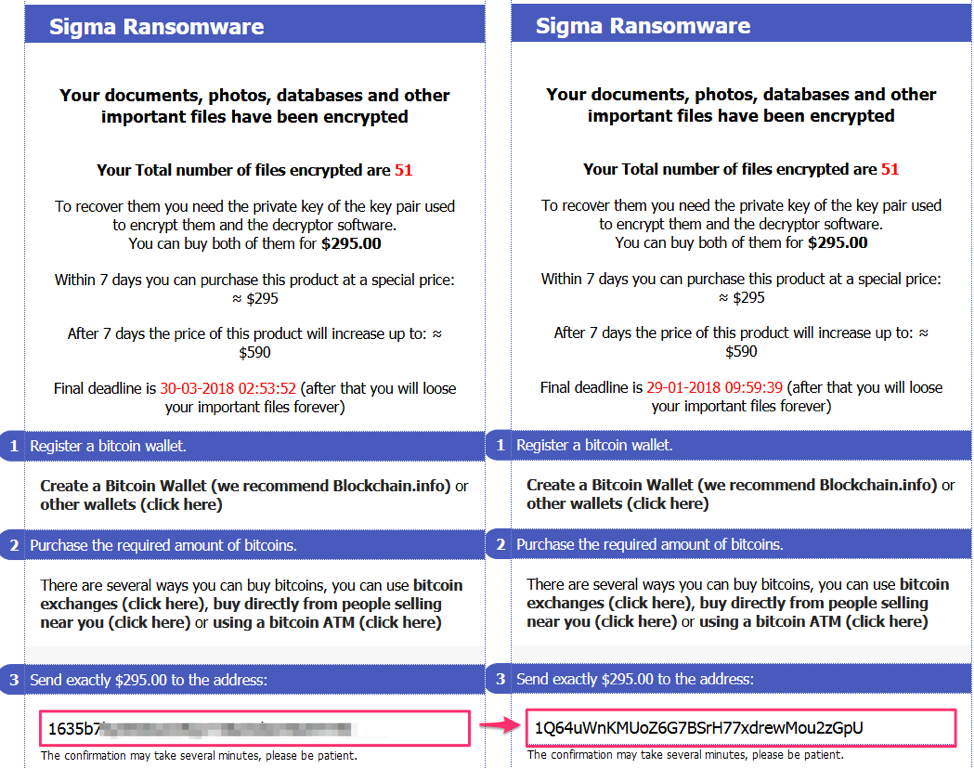
The researchers also tested Globelmposter and Sigma ransomware on Tor and Onion.top and found two different Bitcoin addresses each time. For instance, Tor Browser showed the correct Bitcoin payment address while Onion.topshowed a different payment address, however, both replacement addresses were the same that means Onion.top proxy owners are using one Bitcoin address to steal ransom payment.
$20,000 worth of Bitcoin stolen
Proofpoint analyzed the payment addresses and found out that so far $20,154 (BTC 1.82) have been transferred but it is unclear if the cybercriminals are using other address or proxies to scam innocent victims of ransomware attacks.
Not every ransomware campaign is targeted
It may come as a surprise but the proxy administrators are not replacing payment address for every ransomware campaign. During their test, the researchers noted that the BitPaymer ransomware Bitcoin address was unchanged while sophisticated ransomware operators appear to be aware of this behavior and are attempting to mitigate with “user education” and technical workarounds.
A growing threat
Although Onion.top
“This kind of scheme also reflects the broader trend of threat actors of all stripes targeting cryptocurrency theft. Continued volatility in cryptocurrency markets and increasing interest in the Tor network will likely drive further potential abuses of Tor proxies, creating additional risks for new users,” researchers concluded.
