The new capability of Emotet trojan highlights the fact that one should always secure their device with a strong password.
Initially identified in 2014, Emotet is a banking trojan that has been used in various malicious campaigns in the past for gaining financial data. An example is of 2017 when it infected Mcafee’s ClickProtect service to trick users by making them download a legitimate-looking Word document which in actuality contained the malware.
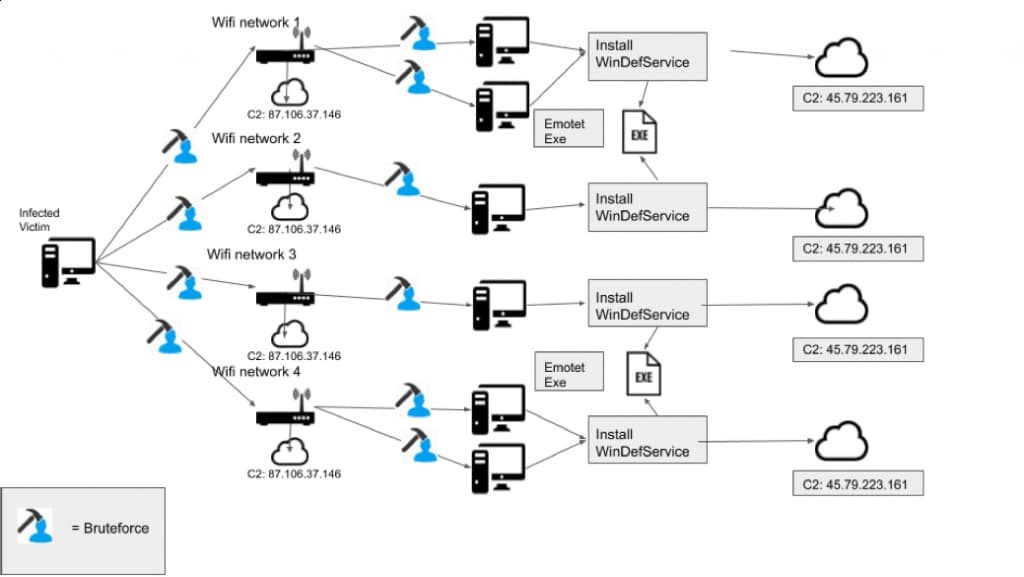
Now, it is back albeit with a new way to spread its infection. Featuring a new WiFi module; the trojan now focuses on compromising machines on the same WiFi network. Simply put: Emotet trojan can now spread through nearby wireless networks if the networks use insecure passwords.
To carry the entire operation out, it firstly uses wlanAPI.dll calls to find wireless networks surrounding it excluding the current computer system it has infected.
See: Hackers using Coronavirus emergency to spread Emotet malware
Commenting on the reason wlanAPI.dll calls are used, researchers at BinaryDefence state that,
“It is one of the libraries used by Native WiFi to manage wireless network profiles and wireless network connections” becoming a natural choice.”
Once it finds such a network, it would connect to it automatically and by using brute-force techniques if it is password protected. Therefore, it searches for Windows-based devices and tries to find its way into user accounts through brute-forcing once again. If successful, it proceeds by adding malicious files for different purposes.
The first one is named “service.exe” which installs an additional service by the name of “Windows Defender System Service.” This helps the attacker maintain access to the system and in a very unsuspicious way indeed in the eyes of a layman.
An interesting thing here is that “although the connection to the server uses port 443, which is normally used for Transport Layer Security (TLS) encrypted communications, the connection is unencrypted HTTP.”
Second is “worm.exe” with a timestamp of ” 04/16/2018” and containing a hard-coded IP address to its C2 server. Explaining this, BinaryDefence states how “this hints that this Wi-Fi spreading behavior has been running unnoticed for close to two years. This may be in part due to how infrequently the binary is dropped.”
A reason that could be attributed to it not being discovered despite the more-than-1-year-old timestamp is that when analyzed on a virtual machine, it does not show any spreading behavior without a WiFi card.
To sum up, both of these help the malware gain access to computers in such a way, particularly those that use weak passwords as brute-forcing them would become much easier this way too. These can then be used for hurting the victim through various ways such as data theft and even ransomware. Hence, we would recommend a range of precautions to guard against such attacks:
- Add passwords to your user accounts even if you do not share your computer system with someone else. This at least gives you a shot to fight anyone trying to get in through such methods.
- Use strong passwords, one that particularly could withstand a large number of attempts per second, a trillion if you’re an Edward Snowden fan and live near the NSA.
- Try to monitor the processes running on your computer to see for suspicious ones. This could be easily done using Window’s in-built task manager.
- Install a good anti-malware software that could also help in network monitoring and recognize “patterns that identify the malware message content.”
- Last but not least avoid using public Wi-Fi spots.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.