The njRAT malware is a remote access trojan that can perform malicious activities such as keylogging, password stealing, data exfiltration, accessing webcams and microphones, and downloading additional files, posing a significant threat to system privacy and security.
In recent news, cybersecurity researchers have discovered that threat actors are utilizing the popular remote desktop support software, TeamViewer, as a delivery mechanism for the njRAT malware.
The njRAT, also known as Bladabindi, is a remote access trojan that poses a significant threat to the privacy, security, and integrity of affected systems.
The recent findings by Cyble Research & Intelligence Labs (CRIL) shed light on the deceptive tactics employed by threat actors to exploit the trust associated with well-known applications. By leveraging the widespread adoption of TeamViewer, as well as other legitimate tools like WireShark and Process Hacker, the threat actors deceive unsuspecting users into downloading and executing the malicious files.
The njRAT malware, initially discovered in 2012-2013, has primarily targeted organizations in Middle Eastern nations. This trojan is capable of carrying out a range of malicious activities, including keylogging, password stealing, data exfiltration, accessing webcams and microphones, and downloading additional files.
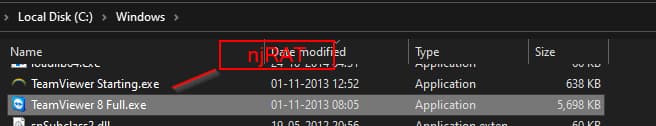
Upon closer analysis, CRIL researchers identified a 32-bit Smart Installer as the delivery mechanism for the njRAT malware. The installer drops two files in the Windows folder, one of which is the njRAT malware itself, while the other is a genuine TeamViewer application. This clever camouflage allows the malware to operate undetected within compromised systems.
Once executed, the installer triggers the njRAT malware and simultaneously launches the legitimate TeamViewer application, creating a deceptive user prompt window that requests the user to proceed with the TeamViewer installation. While the user believes they are installing legitimate software, the njRAT quietly conducts its malicious operations within the compromised system.
To ensure persistence, njRAT modifies system settings, including the “SEE_MASK_NOZONECHECKS” environment variable in the Windows registry, thereby bypassing security warning prompts. Additionally, it creates autorun entries in the system registry and copies itself to the startup directory, guaranteeing that it automatically runs every time the system boots up.
The njRAT trojan also engages in keylogging, capturing keystrokes by utilizing a dedicated thread with continuous monitoring and storage of the captured data. It collects various system information and encodes it using the base64 encoding scheme for exfiltration.
The malware establishes a connection with a Command and Control (C&C) server to transmit the gathered information, awaiting instructions from the C&C server for further malicious actions.
The exploitation of legitimate software like TeamViewer highlights the resourcefulness and adaptability of threat actors in spreading malware. Users must take precautionary measures to protect themselves from such attacks.
Recommendations include downloading tools and applications only from official websites, enabling automatic software updates, using reputable antivirus and internet security software, and exercising caution when opening untrusted links or email attachments.