Meet CoronaVirus, not the virus… but the ransomware.
Another day, another Coronavirus related ransomware – This time, researchers have discovered new ransomware ironically named CoronaVirus.
This ransomware is being distributed via an infected website that pretends to advertise WiseCleaner, a legit Windows system optimization, and utility software, but actually infects the device with CoronaVirus ransomware and the information-stealing tool Khalesi or Kpot trojan.
Clearly, with this new campaign, attackers are trying to monetize from the worldwide unrest caused by the COVID-19 outbreak.
The further probe by Malware Hunter Team revealed that this ransomware is a wiper, and is distributed via a file titled WSHSetup.exe. It is the main downloader file for both CoronaVirus and Kpot. Upon its execution, the file downloads additional files from a remote website, one of which is the Kpot Trojan embedded into a file titled file1.exe.
See: Coronavirus Tracking App is ransomware; locks phones for ransom
Kpot can exfiltrate a variety of sensitive data from the device including web browser data, email, instant messengers, VPN, cryptocurrency, RDP, FTP, gaming software, and account information, apart from taking screenshots of the desktop and targeting crypto wallets stored on the device.
According to Bleeping Computer, the CoronaVirus is downloaded through another file titled file2.exe, which can target a different type of files. Its primary job is to encrypt data on the victim’s device and ask for ransom, which is considerably lower in this campaign in comparison to other ransomware campaigns as attackers are asking for 0.008BTC (USD 45). Moreover, it modifies the drive name as CoronaVirus.
The encrypted files’ names are replaced with the attacker’s email ID such as test.jpg will be renamed as ‘[email protected]___1.jpg.‘ The ransom note is displayed on the desktop in a file named CoronaVirus.txt.
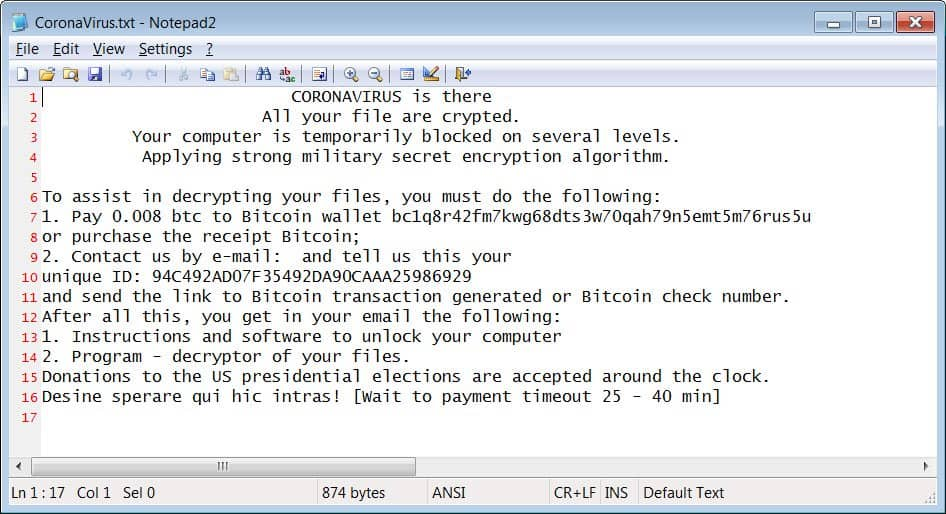
See: Hackers using fake live Coronavirus map to spread malware
It must be noted that the attackers’ Bitcoin wallet hasn’t received any payment yet, which hints upon the fact that this campaign is more about using the information provided by Kpot than receiving payments and CoronaVirus ransomware is just a distraction.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
