It is believed that the botnet was run by infamous Russian hacking group Fancy Bear.
The Federal Bureau of Investigation (FBI) has seized a domain believed to be hosting a botnet of 500,000 compromised routers and other IoT devices – The domain is believed to be operated by Russian hackers from Fancy Bear or Sofacy hacking group.
Fancy Bear is a notorious hacking group previously known for infecting anti-theft software LoJack with malware, hacking IAAF (the International Association of Athletics Federations), officials investigating the MH17 crash, (WADA) World Anti-Doping Agency and others on behalf of the Russian government.
Hackers used VPN Filter malware to built the botnet
In their latest campaign, the group utilized a malware known as “VPN Filter” to exploit several vulnerabilities in home and office (SOHO) routers and other network-access storage (NAS) devices developed by NETGEAR, MikroTik, TP-Link, and Linksys – In total, the group infected 500,000 devices in at least 54 countries.
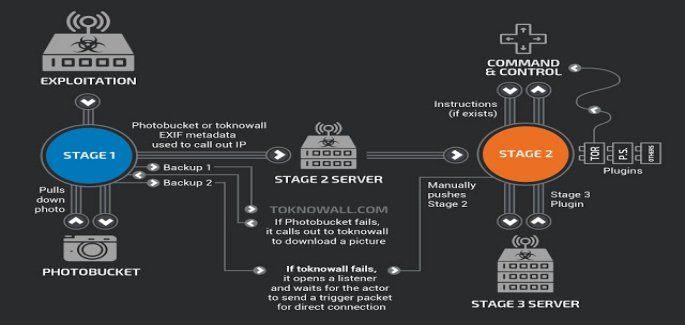
According to Cisco researcher, VPN Filter is an advanced malware while The Daily Beast noted that upon successful infection the malware reports back to a command-and-control server operated by hackers. It then checks for images on Photobucket.com and extracts information in their metadata after which the images were uploaded on ToKnowAll.com.
See: Authorities dismantle Andromeda Botnet that infected millions of devices
It then installs malicious plugins which allow hackers to steal credentials from users Internet traffic or target industrial control networks such as those in the electric grid.
“VPNFilter is an expansive, robust, highly capable, and dangerous threat that targets devices that are challenging to defend. Its highly modular framework allows for rapid changes to the actor’s operational infrastructure, serving their goals of misattribution, intelligence collection, and finding a platform to conduct attacks,” concluded Cisco researchers.
“The destructive capability particularly concerns us. This shows that the actor is willing to burn users’ devices to cover up their tracks, going much further than simply removing traces of the malware. If it suited their goals, this command could be executed on a broad scale, potentially rendering hundreds of thousands of devices unusable, disabling internet access for hundreds of thousands of victims worldwide or in a focused region where it suited the actor’s purposes.”
FBI seizes ToKnowAll.com
The malicious domain that hosted the botnet is ToKnowAll.com. According to the press release from Department of Justice on Wednesday, May 23rd, 2018 the domain was seized by the FBI, however, authorities were conducting investigations on the botnet since August last year.
See: New IoT Botnet DoubleDoor Bypass Firewall to Drop Backdoor
“In order to identify infected devices and facilitate their remediation, the U.S. Attorney’s Office for the Western District of Pennsylvania applied for and obtained court orders, authorizing the FBI to seize a domain that is part of the malware’s command-and-control infrastructure,” the press release explained.
“This will redirect attempts by stage one of the malware to reinfect the device to an FBI-controlled server, which will capture the Internet Protocol (IP) address of infected devices, pursuant to legal process. A non-profit partner organization, The Shadowserver Foundation, will disseminate the IP addresses to those who can assist with remediating the VPN Filter botnet, including foreign CERTs and internet service providers (ISPs).”
Cleaning process
Now that the domain is under the FBI, it is working on to collect the IP addresses of each and every compromised device to start operation clean up aiming it cleaning those devices from VPN Filter malware infection.
Symantec technical director Vikram Thakur told The Daily Beast that “One of the things they can do is keep track of who is currently infected and who is the victim now and pass that information to the local ISPs. Some of the ISPs have the ability to remotely restart the router. The others might even send out letters to the home users urging them to restart their devices.”
See: Hackers behind Mirai botnet & DYN DDoS attacks plead guilty
Image credit: Shutterstock
