Another day, another popular app compromised to drop backdoor and conduct cryptomining.
Telegram Messenger’s critical zero-day flaw that according to Kaspersky Labs researchers was widely being exploited by cybercriminals since March 2017 to distribute a relatively newer kind of malware on computers has now been fixed by the messenger developers. The vulnerability was equipped with numerous capabilities such as the establishment of a backdoor Trojan and cryptomining.
As per malware analyst at Kaspersky Labs Alexey Firsh; “We have found several scenarios of this zero-day exploitation that, besides general malware and spyware, was used to deliver mining software — such infections have become a global trend that we have seen throughout the last year.”
Attackers were able to exploit the flaw in the Telegram instant messenger’s desktop app for Windows OS. This flaw is identified in the right-to-left override or RLO Unicode coding method, which is a text-formatting standard typically used for coding languages that are written in Hebrew and Arabic but they somehow reversed the order of the code by using a hidden Unicode character in the file name.
Using the Unicode formatting *U+202E* attackers were able to alter the code to hide malicious files and make them appear harmless to download them on the targeted computer. They were also able to modify the file extension to deceive victim into downloading something entirely different than what it appeared to be. Such as, a user can be tricked into believing that a .png file is being downloaded while it could actually be a .js file that runs javascript to inject malicious code into the computer.
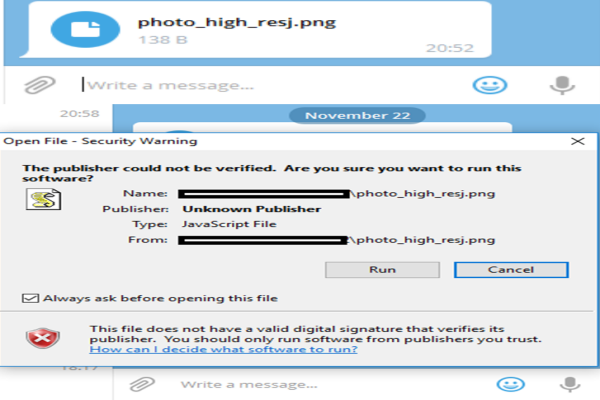
A downloader coded in .NET using the Telegram API as its command protocol can easily launch an altered start registry key on the desktop to let an attacker gain control of the device. The backdoor lets attacker carry out a number of malicious activities on the targeted system such as launching, downloading and removing files as well as accessing web browser history.
According to researchers, the attackers are based in Russia since only Russian cybercriminals were aware of this particular flaw and the commands are also implemented in the Russian language. It is believed that attackers could have stolen Telegram directories that included information about the files exchanged by the victims as well as personal communications data.
Furthermore, the flaw can be used to conduct various kinds of attacks such as to gain full control of the machine remotely and to drop other malware such as keyloggers or tailor the Telegram malware to mine cryptocurrency including Fantomcoin, Monero, and ZCash. If mining operation continues for a longer period then the excessive use of CPU power would overheat the machine ultimately rendering it useless while the victim would remain oblivious to whatever is happening to the computer.
It is yet unclear how much attackers were able to earn from this malicious scheme but researchers noted that the attacks subsided after Telegram was informed about the vulnerability.
Although the flaw has been fixed users need to remain cautious and stay protected by not downloading untrusted files from unknown or unverified sources. Moreover, it is a good idea to immediately update the Telegram Messenger Desktop App for Windows to its latest version in order to prevent your device from being exploited.
