Previously, it was revealed that the GO SMS Pro messaging app was exposing highly sensitive data of more than 100 million users.
A couple of weeks ago, we reported on an Android messaging app named GO SMS Pro which had a flaw that allowed unauthorized individuals to see other people’s private messages. This was due to a link being generated every time a media message was sent which could be not only used by someone other than the recipient to see the message but the link itself could also be incremented to view the messages of others.
Although at the time of the post, the flaw had not been patched, we have an update now. Covered by Trustwave, in the latest, it has been found that the developers of the app have been trying to release a patch but have been unsuccessful in doing so.
It started initially from November 20 when Google removed the app from its Play Store. Three days later, the app was up again but this time with an updated version at the helm.
However, these updated versions which number 2 did not fix the problem at hand. Firstly in the app’s version 7.93, the company disabled sending media files completely.
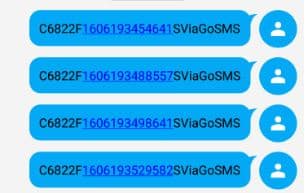
However, in another subsequent update, although the sending was enabled, the media sent was not viewable by the receiver rendering it useless as shown below:
Despite this, the researchers have stated that “we can confirm that older media used to verify the original vulnerability is still available.” This means that the sensitive data of users is still out in the open which includes driver licenses, pictures, confidential documents, and just about anything that can be sent over a chat.
What’s even more alarming is that the researchers have additionally reported finding tools on multiple sites like Github and Pastebin which are geared towards exploiting the flaw in question.

Additionally, underground forums have been “sharing images downloaded from GO SMS servers directly” which clearly spells disaster for the app’s users.
To conclude, this reflects very badly on the developers with their tries showing us that they’re pretty clueless on how the patch can be fixed.
Having such a large user base of more than 100 million users certainly requires the company to hire good cybersecurity analysts who could not only repair current security flaws but also actively conduct penetration testing in order to guard against future attacks.
For now, we would suggest users abandon the app as soon as possible and switch to secure alternatives.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!