The updated version of GravityRAT malware evades detection by checking the current CPU temperature – It is believed that the malware could be sent out from Pakistan.
Cisco Talos research team has identified that the Remote Access Trojan called GravityRAT malware has been updated by its developers, who have been identified to be “The Invincible” and “TheMartian.” As a result of which it can evade detection by antiviruses deployed in the virtual environment, which in technical terms is called sandboxing.
It is worth noting that for the past 8 months, researchers at Cisco Talos have been monitoring GravityRAT Trojan. As of now, researchers have no clue about the location of malware developers but they noted that the documents used for testing detection from antivirus through VirusTotal were uploaded from Pakistan.
According to researchers Warren Mercer and Paul Rascagneres’ post published last week, the Trojan is now equipped with ‘file exfiltration, remote command execution, and anti-VM techniques.’ The RAT is being consistently modified for 18 months, which is indeed a concerning issue because it depicts the ‘determination and innovation by the actor.’
See: Pakistan linked hackers conduct 3rd cyber-espionage campaign against India
GravityRAT spreads infection is a typical manner; it lures the victim into downloading an infected Word.docx email attachment. The recipient is then asked to enable macros after which a Protected Document message appears asking the recipient to ‘prove that the user is not a robot,’ and once this is done, the infection sequence is initiated.
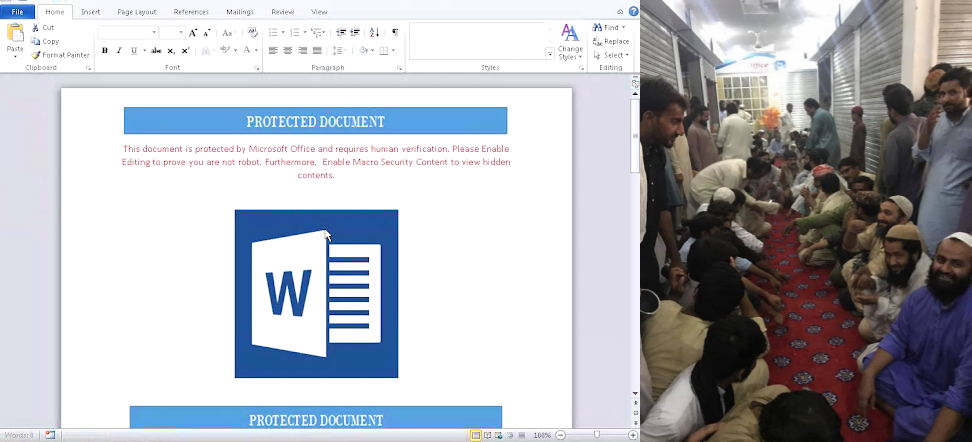
It is a multi-stage procedure that starts from renaming the Word.docx file, which is then copied as a ZIP archive to the targeted machine’s Temp directory. The second stage involves decompressing of the temporary.zip file by the infection script and a .EXE binary is extracted from it. The final step includes the creation of a scheduled task dubbed as wordtest, which is responsible for the execution of the malicious file on a daily basis.
The system’s user data is targeted by the Trojan and files bearing the extension .docx, .pptx, .ppt, .xlsx, .xlx, .RTF and.PDF are stolen. Researchers claim that malware developers are using this approach to make sure that there isn’t any direct execution involved and the additional payload is also not required to be downloaded. The .docx format is just an archive that stores the executable GravityRAT.
The new version of GravityRAT can check system temperature by recording thermal readings for detecting the presence of VMs (virtual machines). It can easily then thwart analysis efforts from researchers as VMs are deployed for identification of decompiling and reverse engineering purposes.
Its latest version can also collect open ports on the targeted system and creates a list of all the active processes after which it starts stealing files stored on any connected USB drive. The Trojan can extract CPU temperatures for nearly seven thermal zones and can identify processor name, ID, clock speed and manufacturer too.
Quite possibly, not all the machines would return this reading but the heat levels can easily reveal if a VM is in operation. Researchers stated that such monitoring is not supported on VirtualBox, Hyper-V, VMWare Fusion, XEN or KVM. If the hardware doesn’t provide heat readings then the Trojan considers them as VMs.
The earlier version of GravityRAT was named G1 and it was discovered in Dec 2016. After that, another version G2 was identified while the latest version published in Dec 2017 and discovered around two weeks back has been named as GX. This version is being referred to as the most advanced GravityRAT variant.
See: Google removes SmeshApp used by Pakistan’ ISI to spy on Indian military
‘Throughout the evolution, we saw this malware embedding open-source legitimate .NET libraries (for schedule tasks, compression, encryption, .NET loading). It contains a resource named ‘important.’ This is an archive with a password,’ wrote Cisco Talos researchers.
GravityRAT’s GX version can detect seven different types of anti-AV software that can determine whether the system is running in a VM environment, which is used by AV researchers. The tools used by the malware to detect the presence of VMs include a virtual machine detection function that searches for a VM hypervisor.
There is another tool that creates a Windows Management Instrumentation request to identify the BIOS version. In case the response is VMware, XEN, A M I, or Xen, the malware realizes that the system is actually a VM. Although this isn’t foolproof approach researchers claim that using these tools the Trojan can easily detect a number of VMs.
Last year in August, India’s National Computer Emergency Response Team (CERT) detected that the notorious GravityRAT Trojan was used to launch targeted attacks in the country.
Now, considering that the malware is even more powerful and given the amount of sandboxing that is conducted within virtual environments, it is evident that security experts would need to find out new ways to counter this issue.
Image credit: Depositphotos
