Cybersecurity firm FireEye’s Mandiant subsidiary responded to an incident caused by a new malware attempting to target Industrial safety systems of a critical infrastructure plant. The Triconex industrial safety technology developed by Schneider Electric SE was targeted with the malware with the sole aim of causing physical damages.
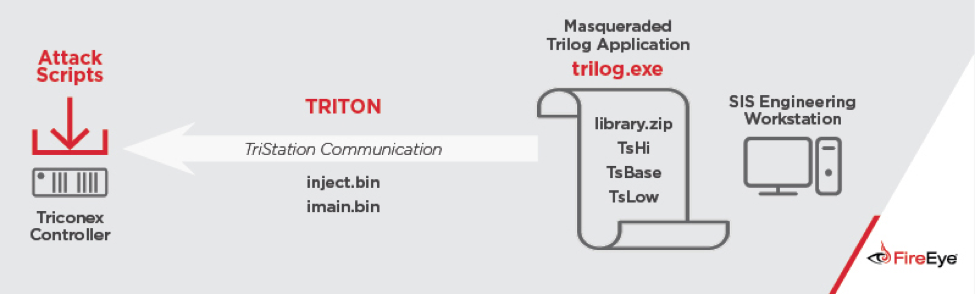
The malware has been dubbed as TRITON and according to FireEye’s analysis, the possible perpetrator wants to exploit emergency shutdown capabilities of the organization’s industrial processes. TRITON is believed to be designed to interact with industrial controllers to cripple safety features and fail the system.
Reportedly, TRITON comes from a very small and limited family of malware equipped with the capability of causing physical damage via cyberspace. The attacker hasn’t been identified by the company but there is evidence that the activity is related to a Nation-State that is preparing for an attack. FireEye claims that this deployment of malware is not the work of a cyber-crime group primarily because the attack on industrial control safety systems of the company hints at a bigger goal, which probably is to cause a highly impactful attack that leads to dire consequences.
Security experts are regarding it as a watershed attack since the safety systems attacked this time are the units used in gas, oil, and nuclear plants. According to FireEye, at least one facility’s operations were halted with the malware. Attackers took remote control of the workstation that ran Triconex safety shutdown system and then reprogrammed the controllers to identify security flaws. When some of the controllers entered Fail Safe mode, the processes were shut down and this is how the attack was identified.
The incident was reported by FireEye on Thursday. After the news broke, Schneider also released a statement confirming the incident and stated that a security alert has been issued by the company for alerting Triconex users.
“While evidence suggests this was an isolated incident and not due to a vulnerability in the Triconex system or its program code, we continue to investigate whether there are additional attack vectors,” read Schneider’s security alert.
It is worth noting that Triconex is widely used in oil/gas plants as well as nuclear facilities and it is vital for energy industry’s operations. However, neither FireEye nor Schneider has identified the company, industry and the location of this attack. All that Dan Scali from FireEye told media is that the hack occurred recently and none of the equipment was damaged and physical damage also wasn’t caused.
Symantec’s researchers noted that TRITON was identified to be active since September. The malware works by infecting a computer running Windows and connected with a safety system. They also asserted that although there have been cases of malware that can attack industrial control systems this is the first malware involving an incident in which attacks “safety instrumented system devices.”
The US Department of Homeland Security also issued a statement claiming that it was assessing the situation and probable impact on the “critical infrastructure.”
