How to identify a website running magecart or web skimming scam? Look no further as Trustwave’s new tool does it for you.
Web skimming is a type of online fraud in which a website’s payment page is compromised through malware or other malicious means. This fraud/attack has recently gained momentum as a popular technique among the black hat hackers community.
By bypassing certain web application security protocols such as the Same Origin Policy (SOP), it is known to bring in lucrative returns. In response to this, various other protocols also exist as an additional layer of security or perhaps an additional measure implemented alongside. These include those like Content Security Polic (CSP) and Sub Resource Integrity (SRI).
However, not everyone has the expertise or resources to ensure these are implemented on their website, particularly individuals and small businesses. So how do users go about finding which site to trust and not end up getting conned? Turns out there’s a tool that can easily help you do so.
See: Bluetana app detects gas pumps card skimmers in 3 seconds
Using “bumperworksonline.com” as an example in light of the analysis done by Trustwave, let’s explore this tool.
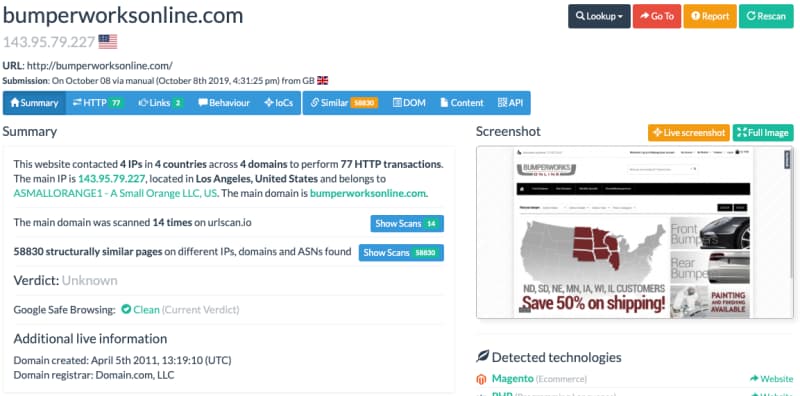
Called “urlscan.io,” the popular tool allows you to enter any URL or hostname and presents a range of information for you to analyze and make a decision. This includes the site’s status in the eye of Google Safe Browsing which is the very first point to check for.
If this indicator contains a “Not clean” status, you would know that the site has been infected. Yet, this is not the only tool that displays such information, others like Sucuri site check show such statuses for a range of other security services like Mcafee as well.
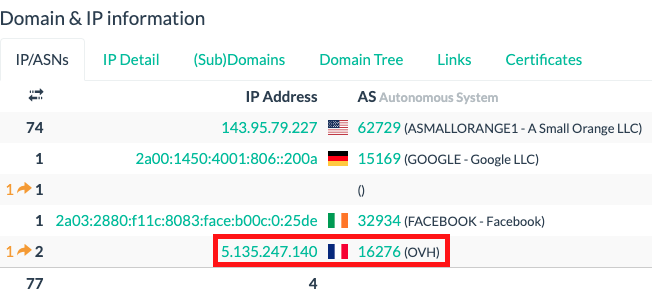
The main finding though is the “domain & IP information” found in the bottom left side of the page. It helps users identify with which addresses all of the site’s HTTP transactions occurred and the number of total IP addresses involved in the entire requests process.
In this case, we know that one IP address is from “A Small Orange” which is the web host in this case (trustable), the second one is from Google (trustable), one is from Facebook (Trustable) whereas the fourth one seems suspicious. With the notion of innocent until proven guilty, we delve deeper by analyzing the details associated with it in the very next tab.
Furthermore, a look at the certificates tab allows users to determine if they are valid in the first place. Since this also appears to be good, we can conclude that the site is not infected by any malicious script.
Now let’s look at a malicious website used as an example by Trustwave. Although a look at the summary presented indicated the site was clean, exploring the domain & IP address information section proved the opposite.
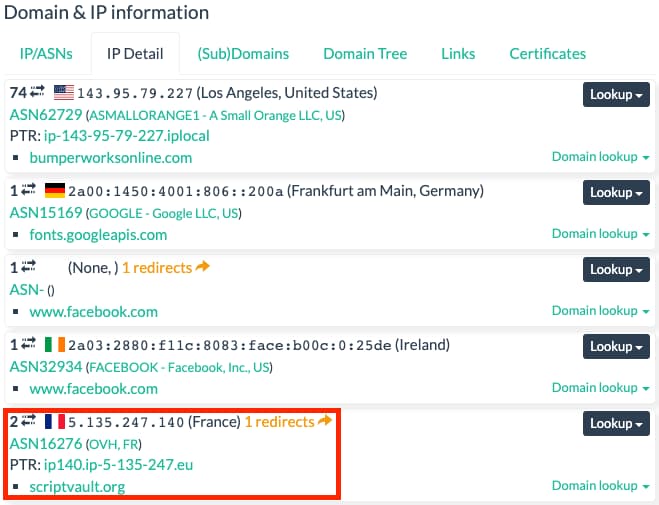
As seen above, the first three IP addresses originate from legitimate web services. However, the fourth one seems suspicious. With the notion of innocent until proven guilty, we delve deeper by analyzing the details associated with it in the very next tab.
From this, we come to know that the “fourth one” originated from a domain named “scriptvault.org” which is based in France. Let’s rewind a bit and proceed to the HTTP tab at the very top now to understand what was being requested by this domain.
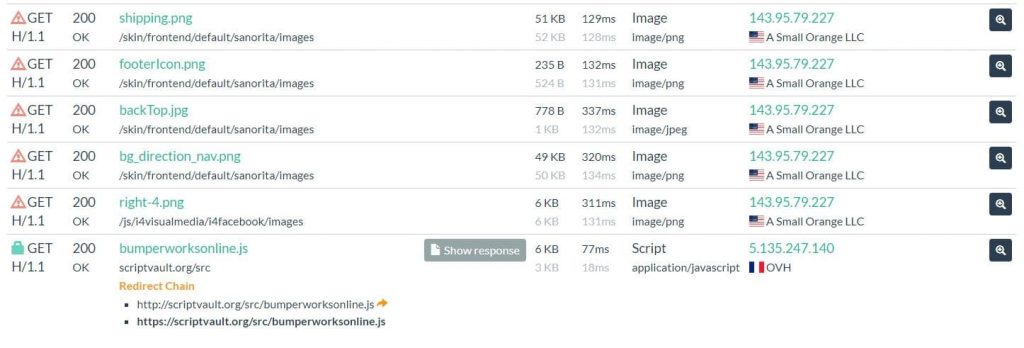
Using the image above, we see that the very last record is loading a script by the name of “bumperworksonline.js”. This is problematic in itself as it is very strange to see a particular script being loaded from an entirely different site while all other scripts originate from a common domain.
Nonetheless, to verify if this is something trustworthy, we can conduct a two-fold test. Firstly, using common sense, why not just go to the originating website itself and see what type of content it hosts? In this case, when we do that, we encounter our first red flag – the URL is blacklisted by prominent anti-virus software.
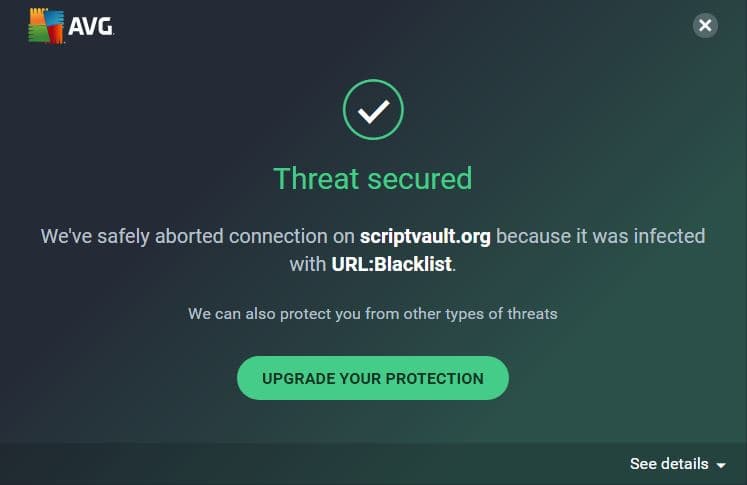
Secondly, we click on the “show response” button to see what’s behind the asset encountering an “obfuscated Magecart script” which has been known to steal payment details through a process we elaborated upon above, known as web skimming.

Yet, we’re still not done. Hackers are not stupid and so they can conceal malware even within innocent-looking files. Hence, we take a look at another record which is this time originating from the host’s IP address.
Clicking the show response button reveals another malicious script.
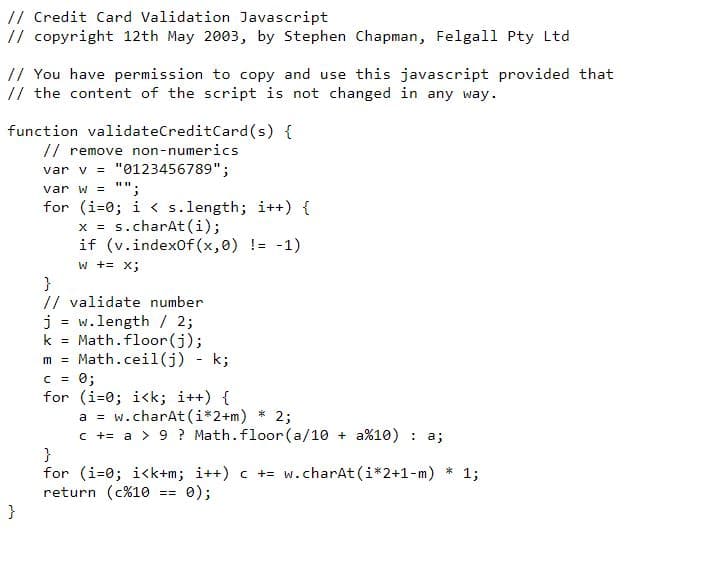
Even if one may not personally recognize that it is a skimming script through a look at its code, a quick Google search of the script’s first 2 lines reveals its true nature. Hence, through this simple process, we can identify a site’s structure and pick out any anomalies to further inspect.
See: New privacy tool exposes which website leaves your data unprotected
For the unacquainted, it may seem a futile exercise but evidence seems to suggest otherwise. As we’ve covered before on HackRead, credit card skimming and specifically scripts like Magecart can result not only in the loss of one’s payment details but also other crucial information such as phone numbers, home addresses, and security codes.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
