The APT group known as Silent Librarian has increased its spear phishing attacks as schools and universities are back.
The IT security researchers at Malwarebytes and Peter Kruse from the CSIS Security Group have reported on an Iranian APT (advanced persistent threat) group also known as Silent Librarian, TA407, and COBALT DICKENS that has been targeting schools and universities around the world with spear phishing attacks.
According to researchers, the malicious campaign has been up and running for the last couple of years however there has been a surge in attacks from the group as students and staff members of schools/universities are coming back after COVID-19 related lockdown.
It is worth noting that in March 2018, the US Department of Justice indicted nine Iranian citizens for targeting universities to steal sensitive research records. Since then the group has gone global and its activities continue to date.
See: 40GB of leaked videos expose how Iranian hackers hijack email accounts
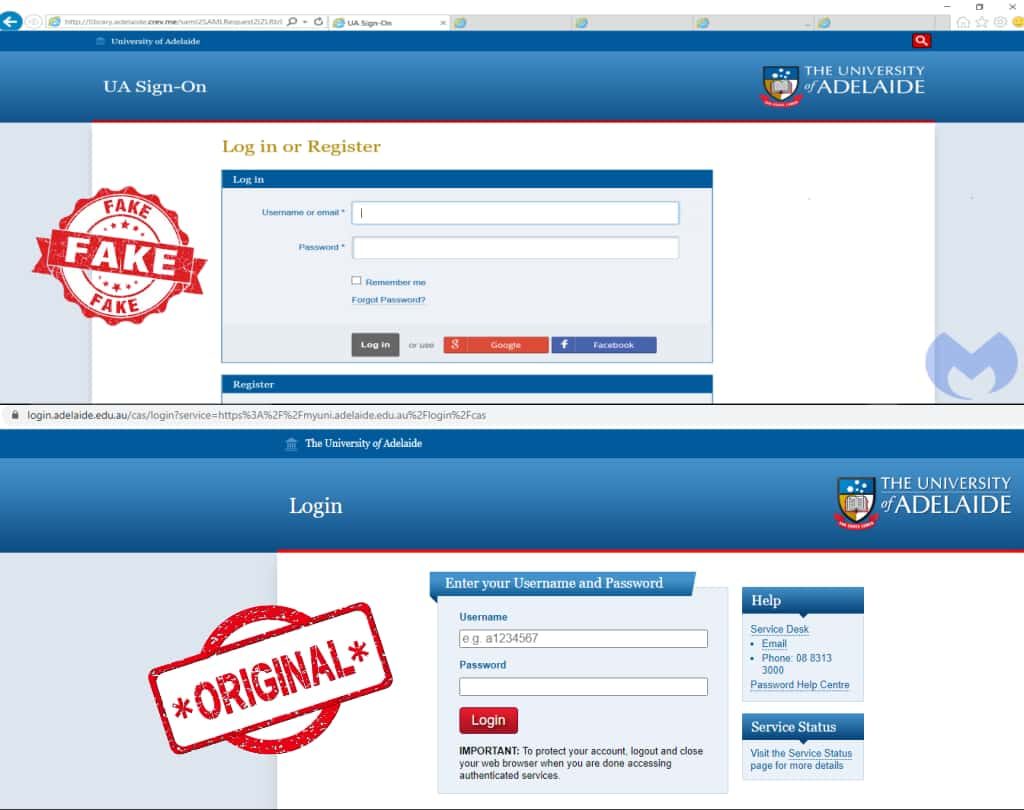
Silent Librarian operates by registering Top-level domains (TLD) with names similar to schools and colleges. A look at some of the sites operated by the group shows many of them had their login page cloned from original university sites to trick users into giving away their login credentials.
The group distributes messages that contain links or HTML attachments that direct victims to cloned university login portals. These portals incorporate stolen branding, accurate street addresses, and other social engineering techniques to manipulate users into disclosing login credentials.
Some of the university used in this attack include:
Victoria University
Universiteit Utrecht
Stony Brook University
The University of Bristol
University of Cambridge
The University of Toronto
Glasgow Caledonian University
The University of Adelaide Library
In a blog post, Malwarebytes’ Threat Intelligence Team stated that although the group covers its tracks by using Cloudflare, the researchers were able to spot some of the sites powered by local hosting companies in Iran.
The researchers believe that this could be because of US sanctions on Iran which makes it nearly impossible to deal with companies in Europe, the US, or elsewhere.
It may seem odd for an attacker to use infrastructure in their own country, possibly pointing a finger at them. However, here it simply becomes another bulletproof hosting option based on the lack of cooperation between US or European law enforcement and local police in Iran, the company said.
Nevertheless, Iran based hackers have upped their game by continuously equipping themselves with tricks. In March last year, Microsoft had announced seizing 99 key websites that Iranian hackers used for stealing sensitive information from unsuspecting users in the US as well as launching cyberattacks.
In February 2020, researchers exposed the “Fox Kitten Campaign” in which an Iranian APT group was found hacking VPN servers to install backdoors to access networks of different organizations across the globe. Moreover, just last month, a six-year-long campaign called Rampant Kitten was exposed by researchers in which Iranian hackers were found utilizing Android backdoor apps.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
