Dubbed Rampant Kitten; the campaign has been going on for the last 6 years in which, among other tools and platforms, Iranian hackers have been utilizing Android backdoor apps.
State-sponsored attackers happen to be one of the most dangerous threats out there due to the vast amount of resources they have backing them up. While almost every country engages in it, some are at the forefront.
One such example is Iran who uses it for a range of purposes. Keeping this in mind, in the latest, researchers from Checkpoint have uncovered an Iranian espionage cyber-campaign running for the past 6 years whose main focus is to target its own citizens living abroad in addition to state critics.
Some examples of these targets, according to researchers, include the Azerbaijan National Resistance Organization and Association of Families of Camp Ashraf and Liberty Residents (AFALR).
See: Iranian APT group hacking VPN servers for “Fox Kitten Campaign”
Delving into the details, the entire campaign dubbed as Rampant Kitten centered around using a variety of tools and attack tactics. Firstly, they targeted 2 main applications, the desktop app of famous messenger Telegram and a password manager named KeePass.
They did so by making users access a malicious MS Word document named “The Regime Fears the Spread of the Revolutionary Cannons.docx” which runs a payload to check if Telegram is installed on the user’s machine.
If found, 3 more payloads are installed helping the attackers to access the victim’s Telegram account.
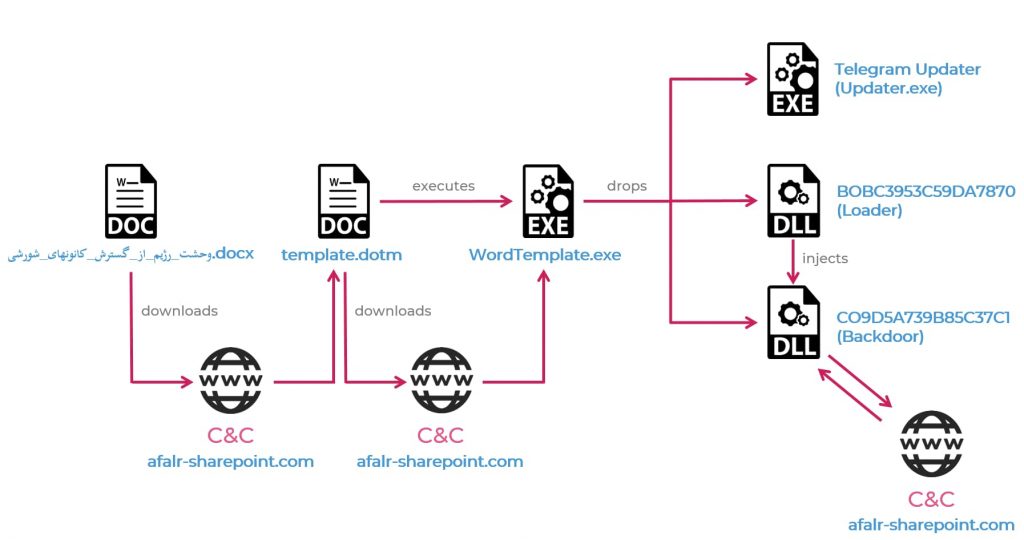 An illustration of the entire infection chain
An illustration of the entire infection chain
Then, an info-stealer is employed which collects data from the victim’s device and transmits it to the attackers via their C2 server. This data involves Telegram files, clipboard data, screenshots of the user’s desktop, and critical info from KeePass.
See: 40GB of leaked videos expose how Iranian hackers hijack email accounts
Secondly, it downloads additional modules on the victim’s computer along with implementing “a persistence mechanism based on Telegram’s internal update procedure.” However, this was not all. Telegram phishing pages were also found related to this campaign designed to also steal user credentials.
An Android backdoor app that markets itself as helping “Persian speakers in Sweden get their driver’s license” was also found. Its real purpose included stealing text messages with 2FA codes, stealing the victim’s contact details, conducting covert voice recordings, and even engaging in phishing to steal Google account credentials.
We have located two different variants of the same application, one which appears to be compiled for testing purposes, and the other is the release version, to be deployed on a target’s device, researchers wrote in a blog post.
How the app looks like:
To conclude, this is one more example of a war front that countries may employ in order to preserve their regimes apart from the apparent censorship. Although it is not confirmed for certain that the Iranian state indeed was involved in this, all evidence indicates so. To top this off, we’ll leave it with a statement from the researchers:
Since most of the targets we identified are Iranians, it appears that similarly to other attacks attributed to the Islamic Republic, this might be yet another case in which Iranian threat actors are collecting intelligence on potential opponents to the regiment.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.


