Lamphone attack allowed researchers to recover conversations from a distance of 25 meters (82 feet).
Earlier this year it was reported that hackers can exploit a critical vulnerability in Philips smart light bulbs to spread malware. Now, scientists at the Ben-Gurion University of the Negev, Israel, and Weizmann Institute of Science have identified that it is possible to use a light bulb’s vibration patterns and evaluate the amount of light emitted to spy on secret conversations from a remote location.
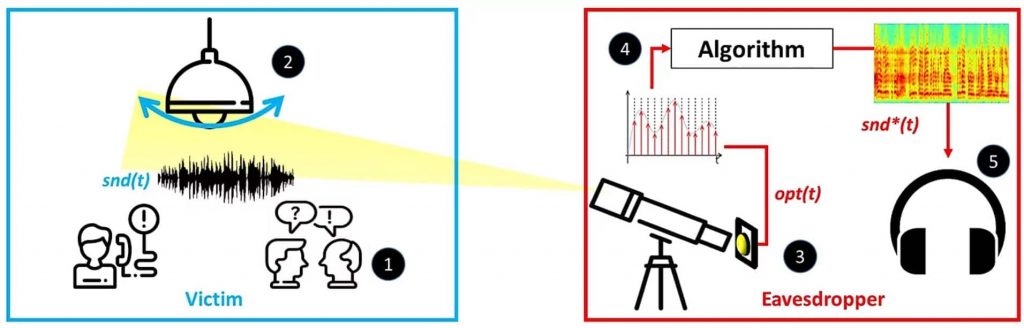
The spying can be conducted simply by observing a hanging light bulb visible from a window in the room.
Scientists Ben Nassi, Yaron Pirutin, Adi Shamir, Yuval Elovici, and Boris Zadov claim that the hanging bulb is the key to this attack, which they have dubbed “Lamphone” attack because it serves as a diaphragm and a transducer.
See: Using a laser on Alexa & Google Home hackers can unlock your front door
This means a hanging light bulb can be used by secret agents and spies to eavesdrop on confidential conversations by detecting vibrations from the bulb that result from naturally occurring air pressure fluctuations when sound waves hit its surface. By measuring the changes in the hanging bulb’s output, snippets of conversations can be picked up including music.
The researchers based their research on the principle that objects vibrate when sound waves hit their surface. They used a setup comprising of a telescope to get a close-up view of the room where the light bulb was present, and an electro-optical sensor mounted on the telescope.
The purpose of the sensor was to convert light into electrical current, that is, to transform the analog output to a digital signal.
Furthermore, by using a laptop researchers could process the incoming optical signals and recovered sound data. By using powerful sensors, the researchers noted, it was possible to record the light variations, and the sound waves hitting the light bulb could be reverse engineered to retrieve the audio.
However, the Lamphone technique has its fair share of limitations. For instance, an attacker would require a direct line of sight to the light bulb, and bulbs that are decorated with covers or other materials cannot be targeted.
See: 8 Technologies That Can Hack Into Your Offline Computer and Phone
Similarly, conversations in windowless rooms cannot be spied upon, and for the attack to be successful the conversation has to be very loud, or else, the speaker should be closer to the light bulb.
In their experiments , the researchers were able to recover conversations from a distance of 25 meters, and they could recover both human conversation and room effects such as the music playing in the background.
The fact that their experiment was successful is alarming for many companies as the technique can be used to spy upon unsuspecting users and retrieve audio from devices that offer similar functions as the microphone. These include vibration devices, speakers, motion sensors, magnetic hard disk drives, and even wooden tables.
The findings of this research will be shared with the public at the Black Hat USA 2020 conference due to be held in August.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.