Hackers exploit unpatched Ivanti vulnerabilities to deploy malware on Linux systems. Magnet Goblin targets businesses using outdated software. Patch immediately and implement strong security measures to protect against these attacks.
Cybersecurity researchers at Check Point are warning of a malicious campaign targeting one-day vulnerabilities in Ivanti and other security software products, potentially impacting a wide range of organizations.
The culprit behind this campaign is a financially motivated hacker group known as Magnet Goblin. This group has been active since January 2022 and specializes in leveraging newly disclosed vulnerabilities, targeting public-facing servers and edge devices.
According to Check Point’s research, Magnet Goblin is using one-day security vulnerabilities to breach edge devices and public-facing services and deploy custom malware on Linux systems. For your information, after zero-day vulnerabilities are disclosed publicly and patches are released, they are referred to as one-day vulnerabilities.
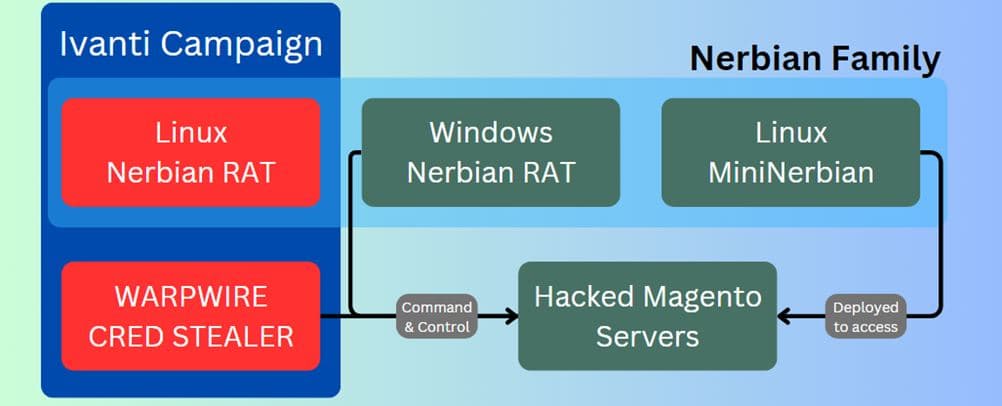
The attackers exploit unpatched servers like Ivanti Connect Secure VPN, Magento, Qlik Sense, and possibly Apache ActiveMQ to deploy a cross-platform remote access trojan (RAT) called Nerbian RAT, first documented by Proofpoint in 2022. It also utilized Nerbian RAT’s simplified variant, MiniNerbian, which allows arbitrary command execution from a C2 server.
“NerbianRAT and MiniNerbian… these tools have operated under the radar as they mostly reside on edge devices. This is part of an ongoing trend for threat actors to target areas which until now have been left unprotected,” researchers noted.
NerbianRAT is downloaded from compromised systems with critical Ivanti Connect Secure flaws. While researching, CheckPoint discovered a 1-day vulnerability infection that led to the download of the NerbianRAT Linux variant.
The variant was used to execute various malicious activities on compromised systems, including modifying connection intervals, work time settings, and updating configuration variables.
Magnet Goblin leveraged CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, and CVE-2024-21893 in Ivanti VPNs, CVE-2022-24086 in Magento, and CVE-2023-41265, CVE-2023-41266, and CVE-2023-48365 in Qlik Sense.
They used a JavaScript credential stealer called Warpwire and the open-source tunnelling tool Ligolo to exploit these vulnerabilities. Warpwire stealer is linked to mass Ivanti vulnerability exploitation and was used in a 2022 Magento server attack. In addition, they used remote monitoring tools ScreenConnect and AnyDesk, targeting Qlik Sense and Apache ActiveMQ.
It is worth noting that Ivanti issued a public advisory in January for CVE-2024-21887, a command injection vulnerability, urging users to patch their systems against wild exploitations. However, Check Point found that Magnet Goblin exploitations occurred within a day of patch issuance, targeting systems not yet patched with available fixed updates.
John Gallagher, Vice President of Viakoo Labs at Viakoo commented on the findings stating, “It’s clear that Magnet Goblin is taking the easy route; using recently disclosed vulnerabilities to exploit poorly defended systems. With many edge and IoT devices and applications there is a lag time between when a vulnerability is disclosed and when a patch is available…and then another lag time between when the patch is released and when it is implemented.”
“Often the teams managing edge and IoT systems are outside of IT and may have different priorities or sense of urgency when it comes to patching. One can expect that one-day threats will be a major security issue, as the speed of AI can accelerate these specific types of threats. Until the speed of delivery by threat actors is matched by the speed of response by defenders this will be an ongoing security risk.”
Organisations of all sizes relying on Ivanti software for endpoint management and security are at potential risk. This includes companies in various sectors that utilize Ivanti to safeguard their critical infrastructure.
Therefore, patching Ivanti software is necessary to prevent exploitation along with increased monitoring, and adopting a layered security approach, including implementing Endpoint Detection and Response (EDR) solutions to strengthen the overall security of the network and devices.