Mamba Ransomware Resurfaces in Brazil and Saudi Arabia With Nefarious Objectives
Last year we informed you about Mamba ransomware that attacked computers across the globe and was detected by Morphus Labs research team. Mamba (a large, agile, highly venomous African snake in real life) was so dangerous that it encrypted the entire hard drive, not just a few files. This Windows based malware was infecting computers in the US, India, and Brazil. It was among the first ransomware samples that encrypted hard drive and launched attacks against organizations including the high profile ransomware attack on SFMTA (San Francisco Municipal Transportation Agency).

Kaspersky Lab researchers have identified the reemergence of Mamba infection in Brazil and Saudi Arabia. This means, the attackers are now disguising sabotage in ransomware, which isn’t a new practice at all since attackers used the same strategy in Petya and Mischa in 2016. However, the attacks met an unprecedented rise in 2017 with the emergence of ExPetr/NotPetya wiper malware attacks.
The perpetrators of the new wave of Mamba ransomware are yet unknown; at the moment it is unclear whether a criminal gang is behind the attacks or a nation-state sponsoring them.
Mamba is quite different from ExPetr/NotPetya attacks since victims cannot recover their computer systems. ExPetr uses a randomly generated key for encrypting the targeted system and does not save the key for decryption later, therefore, it can be called a Wiper, explained Kaspersky Lab researcher Orkhan Memedov.
Currently, Mamba is targeting users in Brazil and Saudi Arabia
Conversely, Mamba passes the key to the Trojan as a command line argument, which means the attacker possesses the key and can decrypt the machine. When the malware infects a Windows based machine, the Trojan overwrites the Master Boot Record through a custom MBR and encrypts the hard drive. This is achieved through an open source full disk encryption utility, which is known as DiskCryptor.
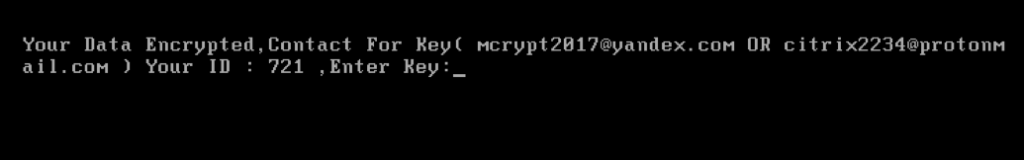
Kaspersky Lab has also published a ransom note which proves that unlike original Mamba infections the latest wave of malware does not demand money but only encrypts data and sends two email addresses along with an ID number for recovering the encryption key. There is no way for data decrypting because DiskCryptor is a legitimate utility that uses extremely strong encryption algorithms.
Kaspersky Lab report suggests that the perpetrators behind newest Mamba attacks in Saudi Arabia and Brazil utilize PSEXEC utility for execution of the malware across the corporate network, which is the same utility used in ExPetr malware attacks. The attacks are also quite similar to the Petya attacks. The bottom line is that the purpose behind the latest attacks is destruction and not profit because the malware’s functioning is faulty and victims cannot recover files. The actual purpose is to wipe out data stored on the hard drives of targeted computers.
Kaspersky Lab states that the attacks occur in two stages, in the first stage DiskCryptor is stored into a folder created and installed by the malware. A system service dubbed as DefragmentService is also registered to ensure persistence. The targeted machine is then rebooted. The second stage creates the new bootloader, and in this stage, disk partitions are encrypted through DiskCryptor. The system is then booted again.
The report further explained that for every machine on the targeted network a password is generated by the threat actor for DiskCryptor utility. The password is then passed through the command line arguments to reach ransomware dropper.
To protect yourself from Mamba and other ransomware attacks, check our exclusive and in-depth “How To” on tackling such threats. Stay safe online.
