The researcher who discovered the database leak suspects it belongs to Zenlayer, an on-demand cloud server provider. However, uncertainty persists as the company has not provided any response or confirmation.
Update: 20:44, Feb 14, 2024, GMT – Article updated with statement from Zenlayer spokesperson.
We’re aware of the data exposure, have patched the issue, and are engaged with the researcher who originally discovered the data leak. We’ll provide additional information when the investigation is complete.
Jeremiah Fowler, a cybersecurity researcher, stumbled upon something quite alarming: a cloud database leak allegedly belonging to the global network service provider Zenlayer, left unprotected and misconfigured. What’s even more shocking is the sheer volume of sensitive data it contained: a staggering 380 million records.
384,658,212 records – 57.46 GB of Database
Upon further digging into the server, the analysis revealed a disturbing truth. The leaked information wasn’t just limited to mundane details; it encompassed the company’s internal workings and, even more concerning, customer data. In total, a jaw-dropping 384,658,212 records, totaling 57.46 GB, were laid bare for all to see.
What’s truly alarming is that this treasure trove of data wasn’t safeguarded by even a basic password. It was out there in the open, accessible to anyone, including those with malicious intent. Essentially, it was a “come and take it, no questions asked” scenario, leaving the door wide open for potential exploitation by threat actors.
Trove of Records Leaked
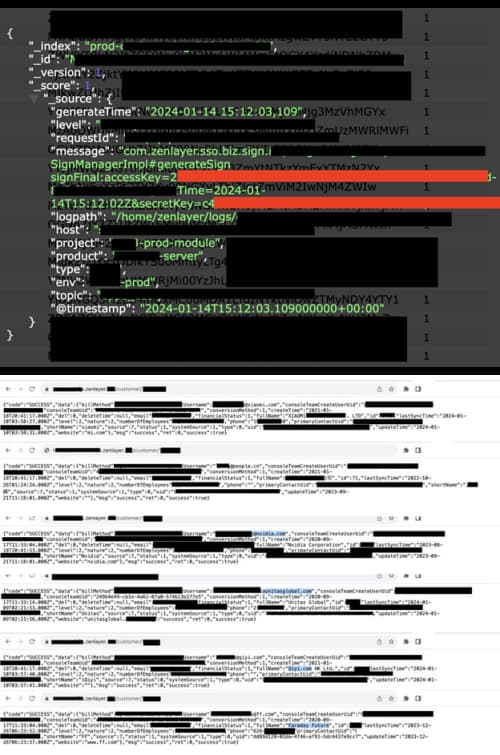
Within this database, numerous servers, error, and monitoring logs were found documenting both internal operations and customer activities. While these logs play a vital role in monitoring server performance, troubleshooting issues, and ensuring system security, they also carry a potential threat.
For your information, Zenlayer is a global network services provider offering SD-WAN, CDN, and cloud services to global brands in the telecom, gaming, media, entertainment, cloud computing, and blockchain sectors. Headquartered in Los Angeles and Shanghai, it has over 290 data centres across six continents. In 2021, Financial Times ranked it third on America’s Fastest Growing Telecom Companies list.
Exposing these logs to the public eye could disclose sensitive information. What was meant to be a tool for enhancing operational efficiency and safeguarding against potential threats could quickly turn into a liability if mishandled or accessed by unauthorized individuals.
The server also contained logging records for various applications, dashboards, vendors, notifications, and security. The exposed customer data, including names and emails of authorized individuals, could be used for targeted phishing attacks or fraudulent activities. For example, attackers may pose as a Zenlayer salesperson and ask for payment or banking information.
Additionally, the database exposure not only exposed sensitive information like user roles but also disclosed internal email addresses. This data could prove invaluable for cybercriminals, facilitating scams and social engineering attacks.
With access to these emails, malicious actors could carry out phishing campaigns targeting employees, potentially leading to the disclosure of confidential data, the installation of malware, and the compromise of credentials.
Russian Data
Fowler’s blog post on Website Planet reveals that part of the records was data of a Russian telecom carrier company, partially owned by a sanctioned state-controlled company, accused of involvement in internet traffic hijacking, or BGP (Border Gateway Protocol) hijacking, which allows attackers to intercept, inspect, or modify network traffic.
However, Fowler clarified that he wasn’t claiming that a Zenlayer customer was involved in the BGP hijacking.
Fowler also discovered logs containing VPN records and numerous IP addresses, including controller host IP, controller IP, IP LAN, jumper IP, and PXE IPMI. These IPs may reveal the organization’s internal network architecture, potentially allowing attackers to map the network, identify targets, or plan future cyberattacks.
Nevertheless, public access was secured the day after Fowler notified Zenlayer. It is unknown if the database was being managed by Zenlayer or a third party, how long it was exposed, and who else may have gained access.
Fortunately, thanks to Fowler’s prompt responsible disclosure, the administrators managed to secure the exposed database within a day. Despite this swift action, the company failed to acknowledge or respond to the researcher’s efforts. Therefore, there remains uncertainty regarding whether the database was under Zenlayer’s direct management or handled by a third party.
Update: 20:44, Feb 14, 2024, GMT –
In a statement to Hackraed.com, a Zenlayer spokesperson confirmed awareness of the issue, now patched. The company is also in contact with Fowler.
We’re aware of the data exposure, have patched the issue, and are engaged with the researcher who originally discovered the data leak. We’ll provide additional information when the investigation is complete.
Zenlayer Spokesperson
RELATED TOPICS
- Cigna Health Data Leak: 17 Billion Records Exposed
- 7TB of Healthcare Data Leak Affects 12 Million Patients
- Researcher Exposes Crypto Scam Network of 300 Domains
- US Credit Union Service Leaks Millions of Records, Passwords
- Database Leak Exposes 500K Irish Police Vehicle Seizure Records
- Data Leak Exposes 1.5B Real Estate Records, Including Kylie Jenner