The misconfigured server logged data from the Bing Mobile App.
The WizCase online security team discovered a massive data leak in a Microsoft owned server that was logging Bing Mobile App data. The leak was discovered via an unsecured ElasticSearch server.
The research team was led by white hat hacker Ata Hackil, who believes that the unsecured server could have allowed third-parties to obtain critically sensitive data such as search queries.
Bing mobile app is available both on Google and Apple stores. It has over 10,000,000 downloads on Google Play Store, and millions of searches are performed through it daily.
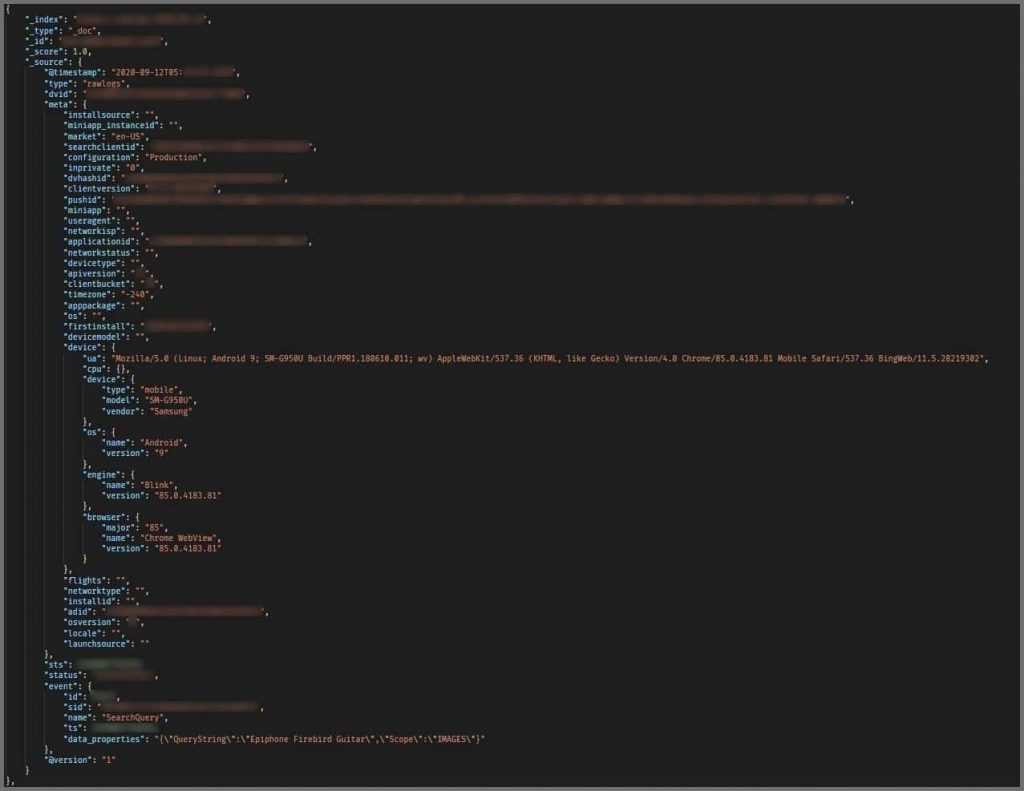
WizCase’s research team found the database when searching for open databases or servers on the internet, and located an unprotected ElasticSearch server that was logging search query terms in clear text format, location coordinates, and device details.
See: Personal details of 38 million+ US citizens leaked in database mess up
The server also revealed the exact time of search query execution, device model, Firebase Notification Tokens (that can allow developers to send notifications to a specific device), a list of URLs the user selected to visit from search results, and coupon data, including the information when the code was copied.
Also, part of the leaked data is unique ID numbers (such as ADID, Devicehash, and DeviceID), and operating system data.
Furthermore, researchers identified that the server exposed precise location data within the distance of 500meters if the user had enabled location permission on the Bing app. Researchers claim that although the exposed coordinates aren’t exact, but can give a likely parameter of the user’s location.
“By simply copying them on Google Maps, it could be possible to use them to trace back to the owner of the phone,” the researchers wrote in a blog post.
The good news is that Bing search engine mobile app users’ personal data, such as their names, wasn’t exposed. Moreover, users who had entered queries in the private mode were not affected.
However, WizCase researchers argue that whatever data is leaked is enough to let bad actors conduct phishing scams, blackmail attacks, and other kinds of malicious campaigns. All they need to do is link user identities to location data and search queries.
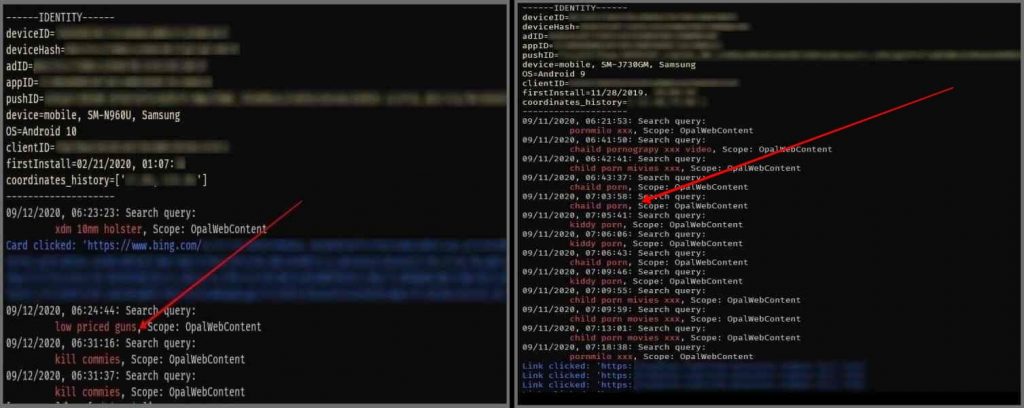
Moreover, the attacker would learn about the user’s daily routine and whether they have cash or expensive items based on search query data. This information would pose the risk of robbery.
“For example, if one were to search for where to buy an expensive item or directions to store, the attacker could be ready to steal the item,” researchers noted.
Bing’s mobile-app version stored a whopping 6.5tb server, which researchers believe was password protected until September 10. On September 12, they discovered that it was unprotected, and the next day they informed Microsoft about the issue. By September 16, the server was secured.
See: Gaming giant Razer leaks customer data in Elasticsearch database mess up
WizCase researcher Chase Williams stated that they didn’t calculate the precise number of users affected by the exposure, but they speculate that the number could be high.
“Based on the sheer amount of data, it is safe to speculate that anyone who has made a Bing search with the mobile app while the server has been exposed is at risk. We saw records of people searching from more than 70 countries,” wrote Williams.
They also claim that the server was targeted with a Meow Attack between September 10, September 12, and September 14.
“From what we saw, between September 10th – 12th, the server was targeted by a Meow attack that deleted nearly the entire database. When we discovered the server on the 12th, 100 million records had been collected since the attack. There was a second Meow attack on the server on September 14.”
Watch the video shared by researchers about the data leak:
The incident should not come as a surprise since Elasticsearch servers have a long history of exposing data online. Furthermore, misconfigured databases have exposed billions of sensitive records in the last couple of years.
Microsoft, in its defense, claims that the amount of exposed data is small. The company’s spokesperson stated that:
“We’ve fixed a misconfiguration that caused a small amount of search query data to be exposed. After analysis, we’ve determined that the exposed data was limited and de-identified.”
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
