Hackers have developed a highly sophisticated malware named “Milkydoor” which can turn any infected Android phone into a hacking tool. Trend Micro, a security firm, revealed on Thursday the discovery of a new malware “Milkydoor” which can be used by hackers to access the networks the phone is connected to, and steal data from it.
Businesses in trouble
Keeping in mind that the hackers can easily access the networks, businesses which allow employees to connect their phones with their servers can face a lot of trouble. With this malware, hackers can easily gain access to the company’s servers allowing them to steal data or perhaps do much more damage.
Mark Nunnikhover, a researcher at Trend Micro said that “Attackers can poke around the network… and then ask for a response from the system that it can see from the Android device… It’s just using the phone as a bridge.”
What’s behind the scenes?
The Socket Secure (SOCKS) based malware uses Secure Shell (SSH) tunneling to remain undetected in the networks. This happens because the firewalls don’t usually block the traffic flowing through Port 22, and of course, the traffic is encrypted which doesn’t alarm the network admins.
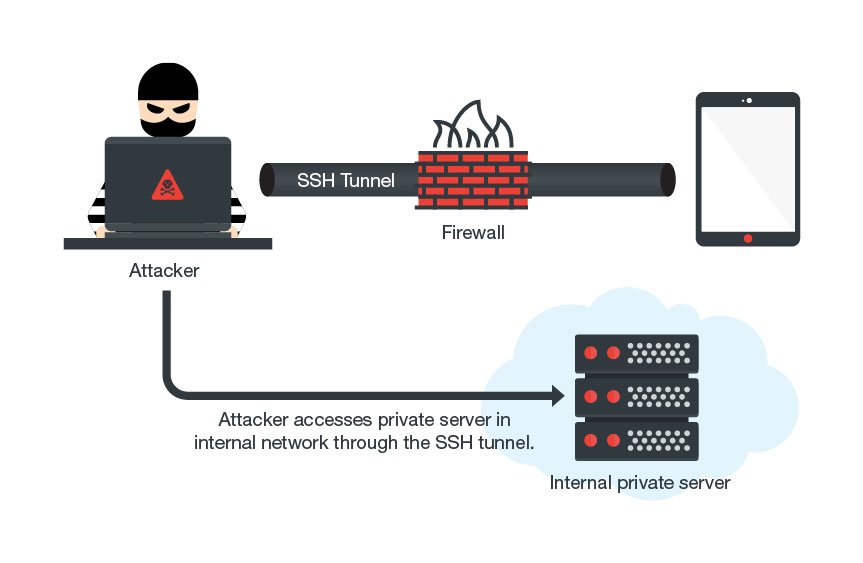
Milkydoor belongs to the same malware family as DressCode. However, it is much more lethal because of its perfect disguise and the sophisticated attacks.
“You’re essentially unimpacted as an Android user… You’re just blissfully unaware. There’s no… an external indicator that’s something wrong, I don’t know that I’m a ‘walking backdoor’ for the attacker,” Nunnikhoven explained.
Affected parties
According to research conducted by Trend Micro, around 200 Android apps contained this malware, and the number of affected parties could be between 500,000- 1000,000. The number of affected devices is so vast because the malware has been spreading since August 2016 and the affected apps were a re-creation of famous style guides, children’s books, drawing applications and other recreational apps.
Related: New Android ransomware proves why antivirus software are a joke
Trend Micro’s Mobile Threat Response Team wrote in the blog post that “We surmise that these are legitimate apps which cyber criminals repackaged and trojanized then republished in Google Play, banking on their popularity to draw victims.”
A word of advice
As always, we highly recommend users to download apps from trusted sources and keep your operating system updated.
DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.
