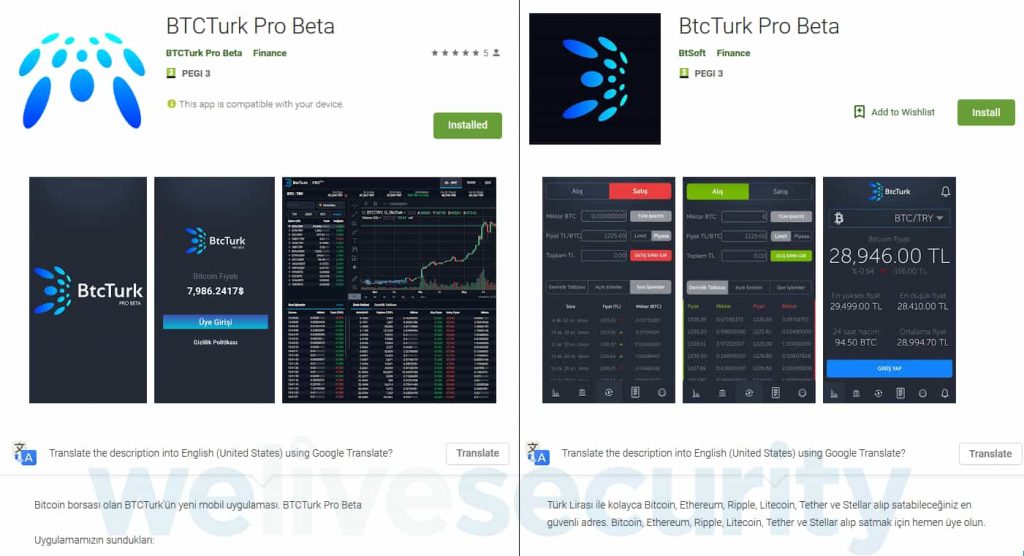
These apps were designed to pass as BtcTurk, a Turkish cryptocurrency exchange.
Researcher Lukas Stefanko at the Slovakian security firm ESET has discovered Android malware in new apps that can bypass the SMS-based two-factor authentication (2FA) without using SMS permissions. The malicious apps are available on the very reliable platform Google Play Store.
Don’t buy cheap phones: Google confirms Triada backdoor in cheap Android phones
Infected apps can access one time passwords (OTPs) sent through SMS and email despite not possessing necessary permissions. Once the passwords from notification sent to the targeted device are stolen, these notifications are immediately hidden so that the user doesn’t suspect any foul play.
In simple words, some malicious, infected apps can read the notifications on your phone and steal 2FA passwords without intercepting SMS or emails. Stefanko wrote in a blog post that using the technique it is possible to “obtain OTPs from some email-based 2FA systems.”
These apps were designed to pass as BtcTurk, a Turkish cryptocurrency exchange. These apps used phishing for obtaining the exchange’s login credentials and took the OTP from the notifications that were displayed on the screen of a compromised device.
First such app was uploaded on Google Play Store on June 7 and was titled BTCTurk Pro Beta, explained Stefanko, while its developer name was also mentioned as BTCTurk Pro Beta. This app was installed by over 50 users until the ESET learned about it and alerted Google’s security teams.
Stefanko further added that another app was uploaded only four days later, that is, on 12 June on the same platform but this time the app was titled differently as BtcTurk Pro Beta and the developer’s name was completely different as BtSoft. This time ESET notified Google earlier than 50 users could install it.
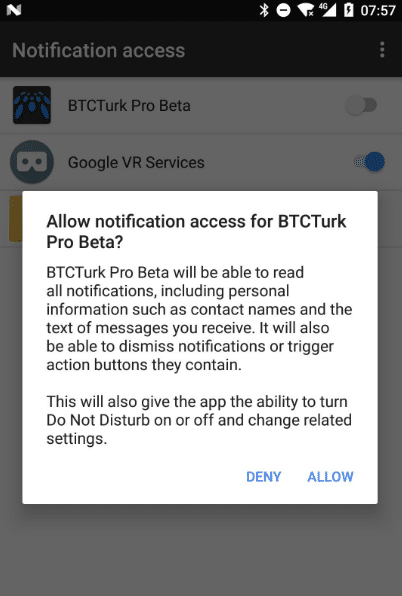
According to Stefanko, when one of the apps were launched, the first thing these asked for is permission named Notification access, which let the app read and dismiss the notifications from other apps on the compromised device as well as click on buttons of different apps.
Afterward, the app shows a fake login screen where it asks for credentials to let the user log in to BtcTurk and the information received is immediately sent to the attacker’s server followed by a fake error message that appears on the device’s screen in the Turkish language.
See: Download official version of Tor browser on Android devices
The restriction on accessing OTPs by apps was enforced by Google in March this year specifically for limiting the incidences of apps receiving sensitive permissions unnecessarily. This is a step taken to make the protection of 2FA codes that are delivered via SMS much stronger.
However, somehow cybercriminals discovered a way to bypass this limitation and uploaded apps that directly tap into the notifications for obtaining the OTPs delivered via SMS and emails.
Stefanko urges users to only download apps from the official websites of the cryptocurrency exchanges and other financial platforms that they intend to use. Moreover, notifications must be allowed to access only those apps that legitimately need to request for it. Keeping all apps on Android devices updated will help as well.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.