It is common notion that antivirus software keeps our computers safe from all types of bugs and malware. However, it seems that cybercriminals are hell-bent on changing this belief by using these programs for fulfilling their malicious objectives. As per the findings of Kapsch’s security researcher Florian Bogner, hackers have learned to exploit the Restore from Quarantine feature, and a number of AV solutions have been affected. The flaw has been named AVGater.
Bogner, an Austrian security editor, states that once it is on a system, this vulnerability relocates malware from an AV quarantine folder and stores it to another sensitive location. It is rather surprising that all antivirus programs available nowadays are plagued with this flaw including Kaspersky, ZoneAlarm, Malwarebytes, Emsisoft, Trend Micro and Ikarus to name a few.
To perform penetration testing, Bogner infected clients’ computer with a conventional phishing email method, and then it was identified that the malware got quarantined by the AV program after which he was able to exploit the software’s flaws. The flaws exploited by Bogner allowed unprivileged users to perform restoration of quarantined documents, while these documents could be relayed to a privileges directory of his own choice (e.g., C:\Program Files or C:\Windows) if NTFS file junction feature in MS Windows was exploited.
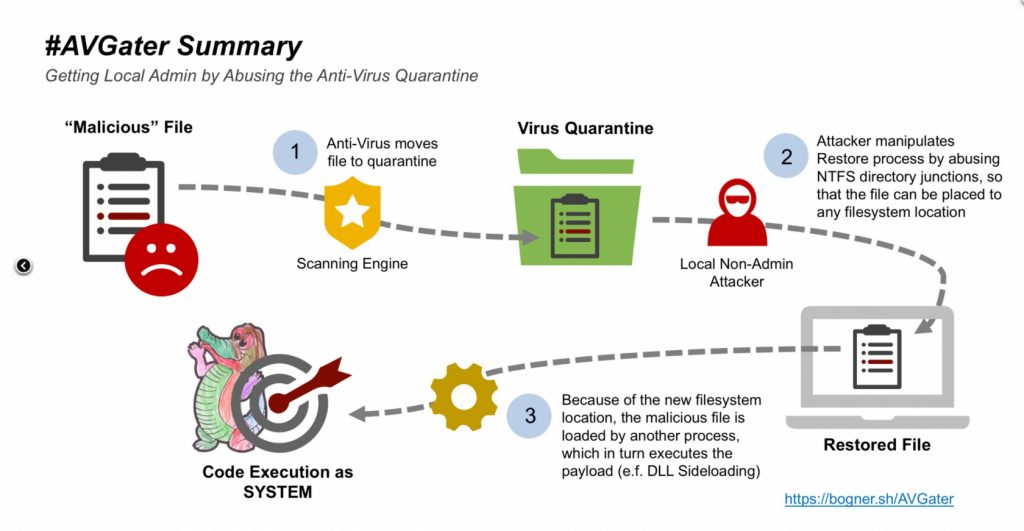
It was also possible to exploit the Dynamic Link Library search order function so that malware could obtain full privileges. A key limitation associated with AVGater is that to launch it attackers need to obtain physical access to a computer and in shared computer environments attack becomes a lot more difficult.
It must be noted that usually, the restore from Quarantine feature doesn’t let a non-administrator to write a document to any other folder but the malware hijacks the NTFS function to perform this task.
According to Bogner, to prevent AVGater, users need to update the antivirus programs installed on their devices. On the contrary, enterprise computer is more at risk to this attack and therefore, Bogner suggests that enterprise users must remove the restore files from quarantine feature for good.
A video was uploaded by Bogner that explains the way this exploit performs its malicious functions while the antivirus software vendors have been notified about the flaw and some already have released security patches to fix the problem.
Source: Bogner | Image Via: Blue Coat Photos
