For now, researchers believe that the malware is targeting Vietnamese users.
Many threat actors remain in the cyber-world for specific purposes, sometimes monetary and sometimes other ones. One such actor happens to be OceanLotus aka APT32 which has in the past targeted companies including Toyota and government agencies as well.
In the latest, the Vietnamese actor is back as reported by Trend Micro researchers who have found a sample strikingly similar to that of the threat actor’s previous work naming the current one as “Backdoor.MacOS.OCEANLOTUS.F.”
See: Hackers using pirated software to spread new cryptomining Mac malware
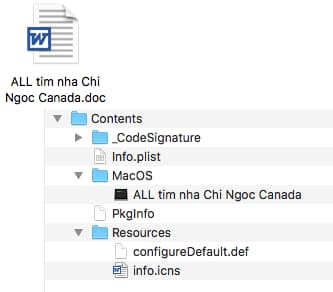
The malware targeting macOS consists of 3 main stages and shows itself as a Word document using a Vietnamese name on the surface but in actuality is an app that is enclosed within a Zip file to avoid detection.
The zip file in itself on the other hand features a shell script as well which executes the malware while showing the word document to the user.
Explaining how this works, the researchers state in a blog post that,
The operating system sees the app bundle as an unsupported directory type, so as a default action the “open” command is used to execute the malicious app. Otherwise, if the postfix is .doc without special characters, Microsoft Word is called to open the app bundle as a document; but since it is not a valid document, the app fails to open it.
In totality, the malware consists of 3 main stages with each depending on the successful functioning of the previous and is believed to target Vietnamese users.
Furthermore, it has the capability to gather data about the victim’s device including the processor, memory, serial number, and MAC addresses information. This is then sent in encrypted form to its C2 servers which number 3, namely, mihanneviscom, mykessefcom, and idtplorg.
To conclude, users need to install reputable anti-malware software to protect their devices against new variants or existing ones of malware.
See: Hackers manipulating Google searches to spread nasty Mac malware
Additionally, the corporate sector should work to make security training mandatory for employees regardless of if whether they are a tech company since a lot is at stake if an employee mistakenly opens a phishing email or downloads such a harmless looking document.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!

Excellent read! where did u come up with the information on this posting? I have read a few of the articles on your website now, and I really like your style. Thanks a million and please keep up the effective work