Pokémon Go is not only your favorite game but also a favorite target for cybercriminals — After malware infected apps here’s Pokémon Go Ransomware scam!
Pokémon Go’s augmented reality tech has attracted the attention of gamers and mobile phones users like no other game has done ever before. It is being played by one and all, be it a celeb or a housewife. So, how can scammers let go of such a great opportunity of trapping unsuspecting users with their never ending antics?
Therefore, not surprisingly, hackers are churning out one malware after another claiming to be apps that install Pokémon Go on your phones. This report informs you about the latest of such attempts from scammers that make use of the popular game. In this new campaign, hackers are distributing a Pokémon Go themed ransomware that is capable of encrypting all the data on the phone, data exfiltration and also creating backdoor Window accounts.
Must Read: Fake Pokémon Go app contains RAT; takes full control of infected device
The latest campaign was discovered by a security researcher Michael Gillespie and it was analyzed by Bleeping Computer team. Their analysis revealed that the new ransomware is although underdeveloped as of now but hackers are working on it and preparing for its widespread distribution campaign.
How this ransomware is spreading?
It can be distributed through PokemonGo.exe, which is an MS Windows based executable. The file displays a Pikachu icon as well. As soon as this file is installed, the process of encryption starts. Afterward, a registry key is added to hide the new Windows admin account, which has been aptly titled “Hack3r.”
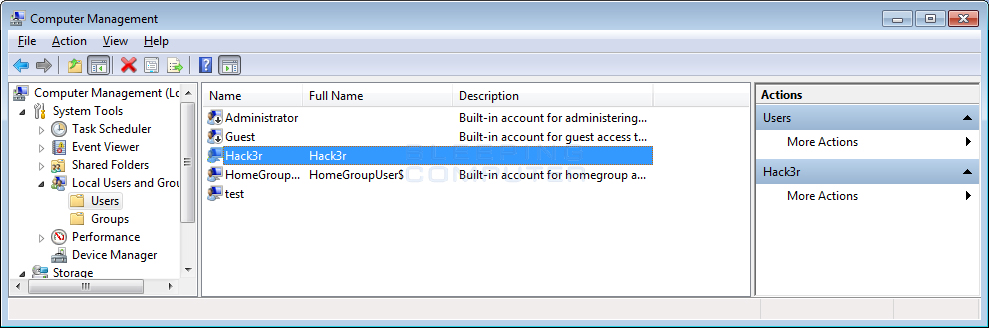
Moreover, this key also copies itself to the root directories of all the fixed drives as well as creates an autorun entry to start so that if the users reboot, the ransomware will not be detected or deleted. That’s not all; the registry key also gets added to removable drives and also creates an autorun file over there too to ensure whenever a portable device is inserted, the executable launches automatically.
Experts believe that this particular ransomware shares similarities with last year’s Hidden Tear project because it also was capable of backdoor encryption. The reason why experts are not so sure about its full development is that the ransomware’s encryption system utilizes “123vivalalgerie”, which is a static encryption key. Furthermore, it attempts to create link with a C&C server, which is identified to be located at this IP address: 10.25.0.169
#HiddenTear #Ransomware masked as @PokemonGoApp, sad Pikachu included. Note هام جدا.txt: https://t.co/UcoHYblx7g pic.twitter.com/xXO8f8nTZs
— Michael Gillespie (@demonslay335) August 12, 2016
This address is non-reachable through the Internet and happens to be a private IP address and is usable on privately routed networks. It has also been identified that the ransom screen and another information is written in the Arabic language while the AES encryption key is in Algerian and there are indications of French text too. Therefore, as of now researchers aren’t aware of the actual location of the creator.
Must Read: Malware Infected PokémonGo Apps Found on GooglePlay Store
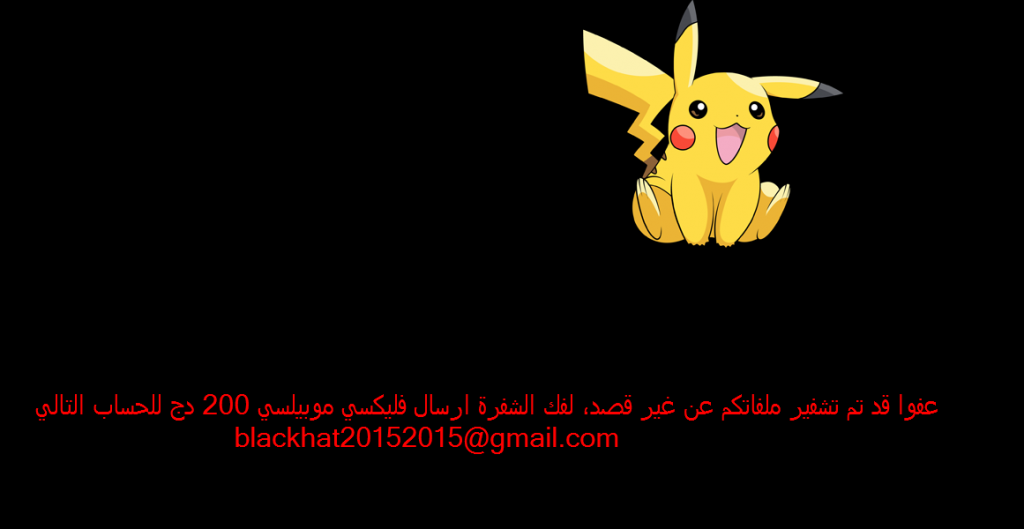
In case you have become the victim of this campaign, there is no need to pay the ransom. Instead, contact Michael Gillespie and/or Bleeping Computer to get a free decrypter.
